diff --git a/CHANGELOG.md b/CHANGELOG.md
index bbfe465..2efce7c 100644
--- a/CHANGELOG.md
+++ b/CHANGELOG.md
@@ -7,6 +7,20 @@ and this project adheres to [Semantic Versioning](https://semver.org/spec/v2.0.0
## [Unreleased] (in 'dev')
+### Changed
+
+- updated npm dependencies
+- renamed Azure, AzureAD, ... to Microsoft Entra ID
+
+### Fixed
+
+- checked and fixed all links
+
+### Added
+
+- example [customizer](./customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js) to sync only users within specified groups
+- usage examples for `Portainer`, `Authelia` and `Synology Radius with UniFi` in the [documentation](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/usage/)
+
## [2.0.1] - 2023-07-21
### Changed
@@ -57,7 +71,7 @@ As a result, existing customizers (mapped `/app/customizer/ldap_customizer.js`)
### Added
- Env var `GRAPH_IGNORE_MFA_ERRORS` to allow logins despite required MFA. When set to true, some MFA-related error codes are treated as successful logins. Attention, this is only a first attempt and may not work in all cases. Please open an issue if you encounter any problems with this.
-- Deleted users and groups in Azure are now also removed from the LDAP entries. The number of days these entries should be kept in this wrapper before deletion can be specified with the env var `LDAP_DAYSTOKEEPDELETEDUSERS`. (see [FAQ](./FAQ.md#are-deleted-users-or-groups-in-azure-also-removed-from-the-ldap-entries) for more details)
+- Deleted users and groups in Azure are now also removed from the LDAP entries. The number of days these entries should be kept in this wrapper before deletion can be specified with the env var `LDAP_DAYSTOKEEPDELETEDUSERS`. (see [FAQ](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/troubleshooting/#are-deleted-users-or-groups-in-azure-also-removed-from-the-ldap-entries) for more details)
- Env var `LDAP_PORT` to set a custom port for the listener (e.g. 389 for running the container directly on the host network)
- Print version at start-up, so you don't have to remember which version you are currently using.
- Check if the volume /app/.cache is mapped inside a docker container
@@ -268,7 +282,7 @@ if set to true and the login is failed, the login is retried against the sambaNT
- Dockerfile
- Container on hub.docker.cm
-[Unreleased]: https://github.com/ahaenggli/AzureAD-LDAP-wrapper/projects/1
+[Unreleased]: https://github.com/ahaenggli/AzureAD-LDAP-wrapper/
[2.0.1]: https://github.com/ahaenggli/AzureAD-LDAP-wrapper/releases/tag/v2.0.1
[2.0.0]: https://github.com/ahaenggli/AzureAD-LDAP-wrapper/releases/tag/v2.0.0
[1.8.2]: https://github.com/ahaenggli/AzureAD-LDAP-wrapper/releases/tag/v1.8.2
diff --git a/README.md b/README.md
index 38ce6c8..de1b2c0 100644
--- a/README.md
+++ b/README.md
@@ -1,6 +1,8 @@
-# LDAP-wrapper for AzureAD users/groups [](https://github.com/ahaenggli/AzureAD-LDAP-wrapper)  +# LDAP-wrapper for Microsoft Entra ID users/groups [](https://github.com/ahaenggli/AzureAD-LDAP-wrapper)
+# LDAP-wrapper for Microsoft Entra ID users/groups [](https://github.com/ahaenggli/AzureAD-LDAP-wrapper)  -AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from Azure Active Directory to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This enables other applications to connect to the LDAP server and utilize AzureAD login credentials, making it a possible solution for older applications that lack AzureAD support or for scenarios where managing a local AD controller is undesirable.
+LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from `Microsoft Entra ID` (formerly `Azure Active Directory`) to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This allows your other applications to connect to the LDAP server and thus allows your end users to authenticate with a work or school account.
+
+This it a possible workaround for older applications that lack Microsoft Entra ID support or for scenarios where managing a local AD controller is undesirable.
## Table of Contents
@@ -10,7 +12,7 @@ AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://
* [Run the LDAP-wrapper](#run-the-ldap-wrapper)
* [Usage](#usage)
* [Settings](#settings)
-* [Troubleshooting](#troubleshooting)
+* [Troubleshooting / FAQ](#troubleshooting-/-faq)
* [Security](#security)
* [Contributing](#contributing)
* [Support this project](#support-this-project)
@@ -22,49 +24,49 @@ AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://
sequenceDiagram
autonumber
participant LDAP client
- participant AzureAD-LDAP-wrapper
- participant AAD (Graph API)
+ participant LDAP-wrapper
+ participant ME-ID (Graph API)
- Note over AzureAD-LDAP-wrapper: start LDAP server
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups
- Note over AzureAD-LDAP-wrapper: cache users and groups locally
+ Note over LDAP-wrapper: start LDAP server
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups
+ Note over LDAP-wrapper: cache users and groups locally
- LDAP client->>+AzureAD-LDAP-wrapper: Attempt to bind with user credentials
- AzureAD-LDAP-wrapper->>+AAD (Graph API): Check user credentials
- AAD (Graph API)-->>-AzureAD-LDAP-wrapper: Valid credentials
+ LDAP client->>+LDAP-wrapper: Attempt to bind with user credentials
+ LDAP-wrapper->>+ME-ID (Graph API): Check user credentials
+ ME-ID (Graph API)-->>-LDAP-wrapper: Valid credentials
- Note over AzureAD-LDAP-wrapper: save password hash locally in the cache
- AzureAD-LDAP-wrapper->>-LDAP client: Successful bind/authenticate
+ Note over LDAP-wrapper: save password hash locally in the cache
+ LDAP-wrapper->>-LDAP client: Successful bind/authenticate
loop every 30 minutes
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups again
- Note over AzureAD-LDAP-wrapper: merge and cache users and groups locally
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups again
+ Note over LDAP-wrapper: merge and cache users and groups locally
end
```
-The AzureAD-LDAP-wrapper starts an LDAP server and fetches users and groups from the AAD Graph API. These are cached and merged locally.
+The LDAP-wrapper starts an LDAP server and fetches users and groups from the Microsoft Graph API. These are cached and merged locally.
-When an LDAP client attempts to bind with user credentials, the AzureAD-LDAP-wrapper checks these credentials by communicating with the AAD Graph API. If the credentials are valid, the AAD Graph API sends a success response to the AzureAD-LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the AzureAD-LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
+When an LDAP client attempts to bind with user credentials, the LDAP-wrapper checks these credentials by communicating with the Microsoft Graph API. If the credentials are valid, the Microsoft Graph API sends a success response to the LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
-The AzureAD-LDAP-wrapper periodically fetches user and group information from the AAD Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
+The LDAP-wrapper periodically fetches user and group information from the Microsoft Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
## Getting Started
### Requirements
-To use the AzureAD-LDAP-wrapper, you will need:
+To use the LDAP-wrapper, you will need:
-* An Azure Active Directory (AD) tenant with at least one registered user.
-* An Azure AD application registered in your tenant, with the following permissions:
+* A Microsoft Entra tenant with at least one registered user.
+* A Microsoft Entra application registered in your tenant, with the following permissions:
* For type `Application` grant `User.Read.All` and `Group.Read.All`.
* For type `Delegated` grant `User.Read`.
You can follow the instructions in the [installation guide](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/installation/create-azuread-application) to set up your application.
-To run the AzureAD-LDAP-wrapper, you'll need to have your Tenant ID, Application ID, and Application Secret available. These values are required to authenticate and authorize the application to access your Azure AD resources. You can find these values in the Azure portal.
+To run the LDAP-wrapper, you'll need to have your Tenant ID, Application ID, and Application Secret available. These values are required to authenticate and authorize the application to access your resources. You can find these values in the Microsoft Entra ID portal.
-Once you have created your Azure AD application, you can run the LDAP wrapper on your local machine, on a server or even a Synology NAS. Depending on your setup you will either need:
+Once you have created your Microsoft Entra application, you can run the LDAP-wrapper on your local machine, on a server or even a Synology NAS. Depending on your setup you will either need:
* Node.js version 17 or higher, which can be downloaded from the official [Node.js website](https://nodejs.org/en/download/).
@@ -93,7 +95,7 @@ Use "bridge" as your network.
4. Give your container a name and enable auto-restart.
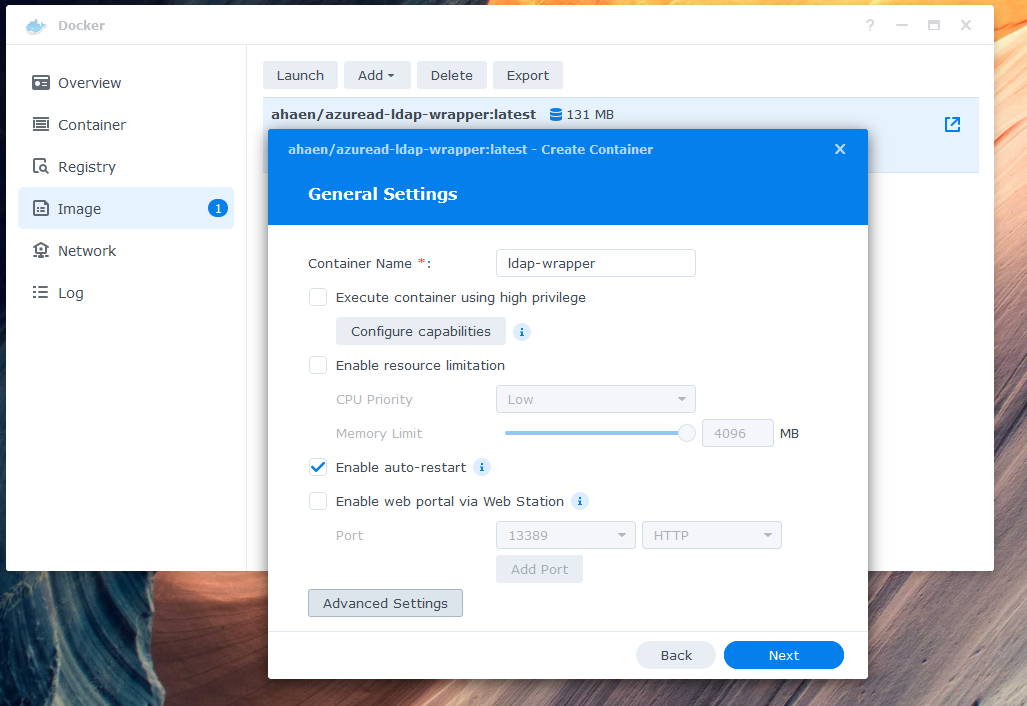
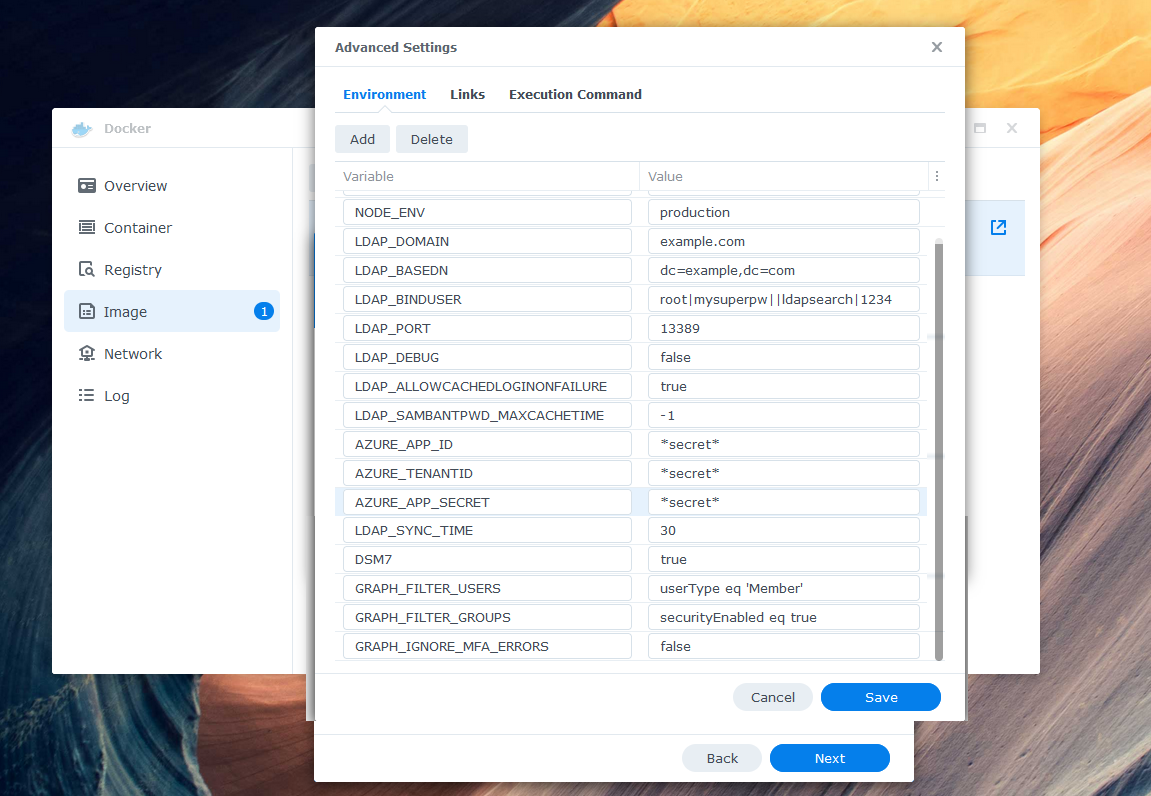
-5. Configure the environment variables in "Advanced Settings". Be sure to double check your Azure values and define at least one binduser. The binduser (superuser like root) does not need to exist in your AzureAD. Replace example.com with your domain. Here is an example of a minimum required configuration:
+5. Configure the environment variables in "Advanced Settings". Be sure to double check your Microsoft Entra values and define at least one binduser. The binduser (superuser like root) does not need to exist in your tenant. Replace example.com with your domain. Here is an example of a minimum required configuration:
```bash
TZ: "Europe/Zurich" # optional
@@ -109,7 +111,7 @@ Use "bridge" as your network.
```
- A full list of all environment variables can be found [here](../../configuration/settings/).
+ A full list of all environment variables can be found [here](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/configuration/settings/).
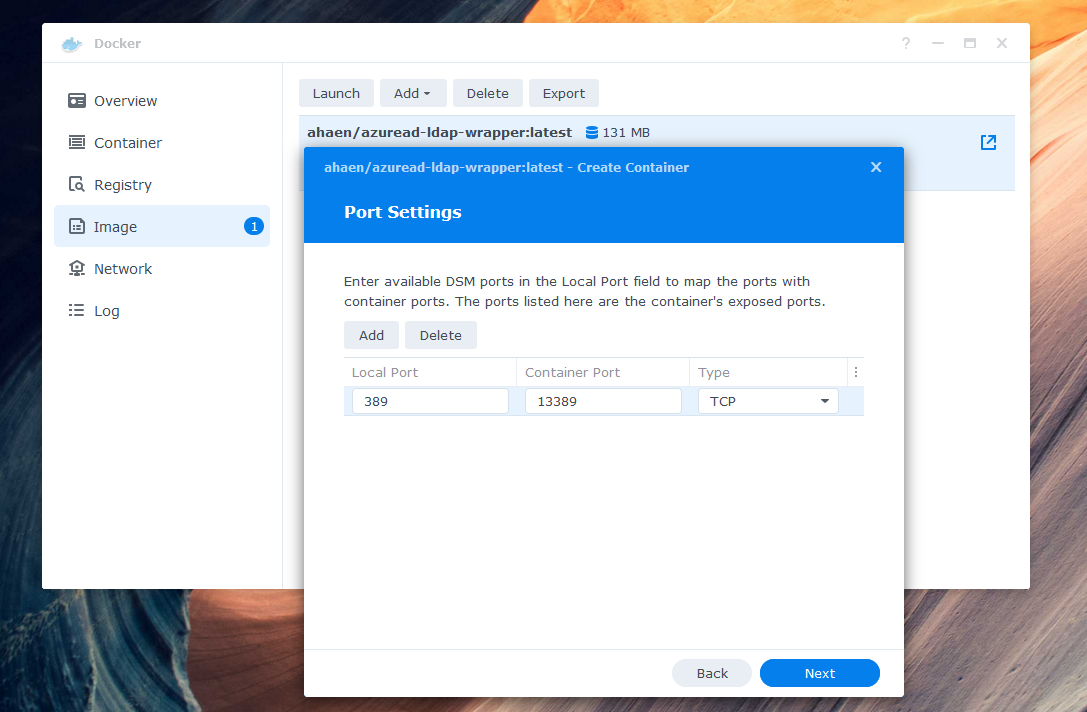
6. Set local Port 389 to the Container Port 13389. If you receive the error Local port 389 conflicts with other ports used by other services, make sure that Synology Directory Service and Synology LDAP Server are not installed - they also use this port.
@@ -122,7 +124,7 @@ Use "bridge" as your network.
### Usage
-To enable users to log in to Synology NAS with their Azure credentials, you need to connect the NAS to the AzureAD-LDAP-wrapper. Here are the steps:
+To enable end users to log in to Synology NAS with their work or school account, you need to connect the NAS to the LDAP-wrapper. Here are the steps:
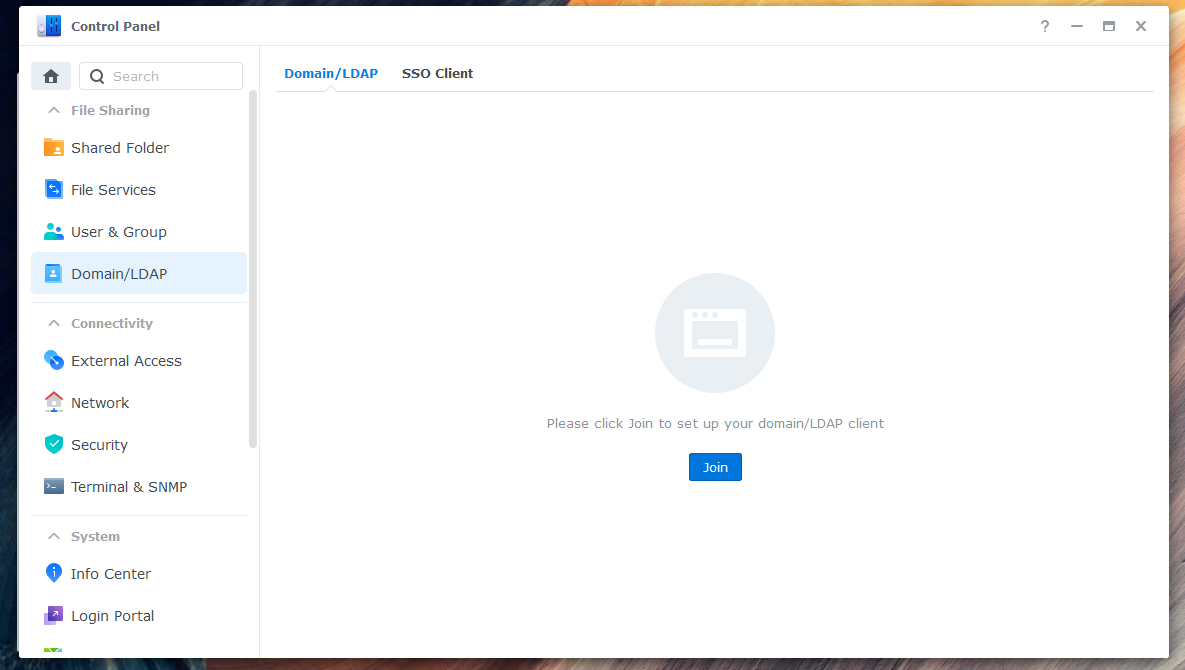
1. Go to Control Panel > Domain/LDAP and click "Join".
@@ -136,10 +138,10 @@ To enable users to log in to Synology NAS with their Azure credentials, you need
4. If you see a warning about a local group having the same name as a synchronized group, you can ignore it and skip the warning in "Details".
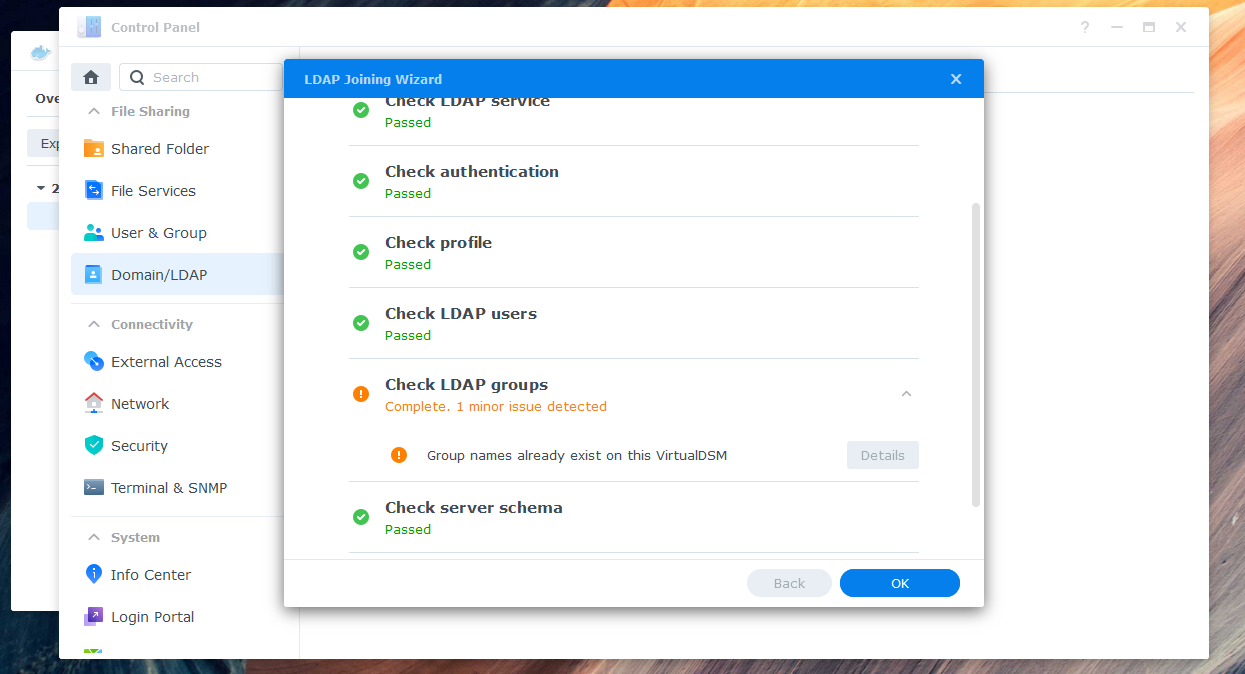
-5. Your NAS should now be connected successfully to the Azure AD LDAP-wrapper.
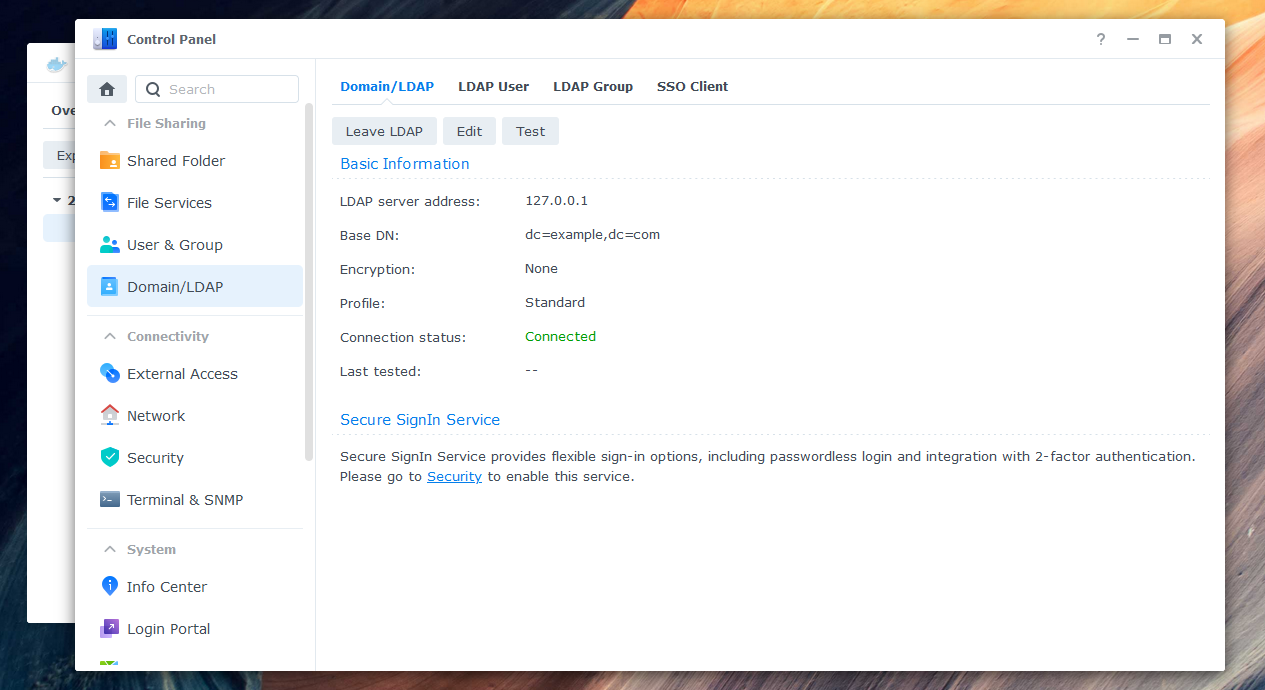
+5. Your NAS should now be connected successfully to the LDAP-wrapper.
-6. Check the "LDAP User" and "LDAP Group" tabs to ensure that all entries are fully synced. Assign the desired permissions to your synchronized users and groups. You can now log in with your Azure AD credentials.
+6. Check the "LDAP User" and "LDAP Group" tabs to ensure that all entries are fully synced. Assign the desired permissions to your synchronized users and groups. You can now log in with your Microsoft Entra account (work or school account).
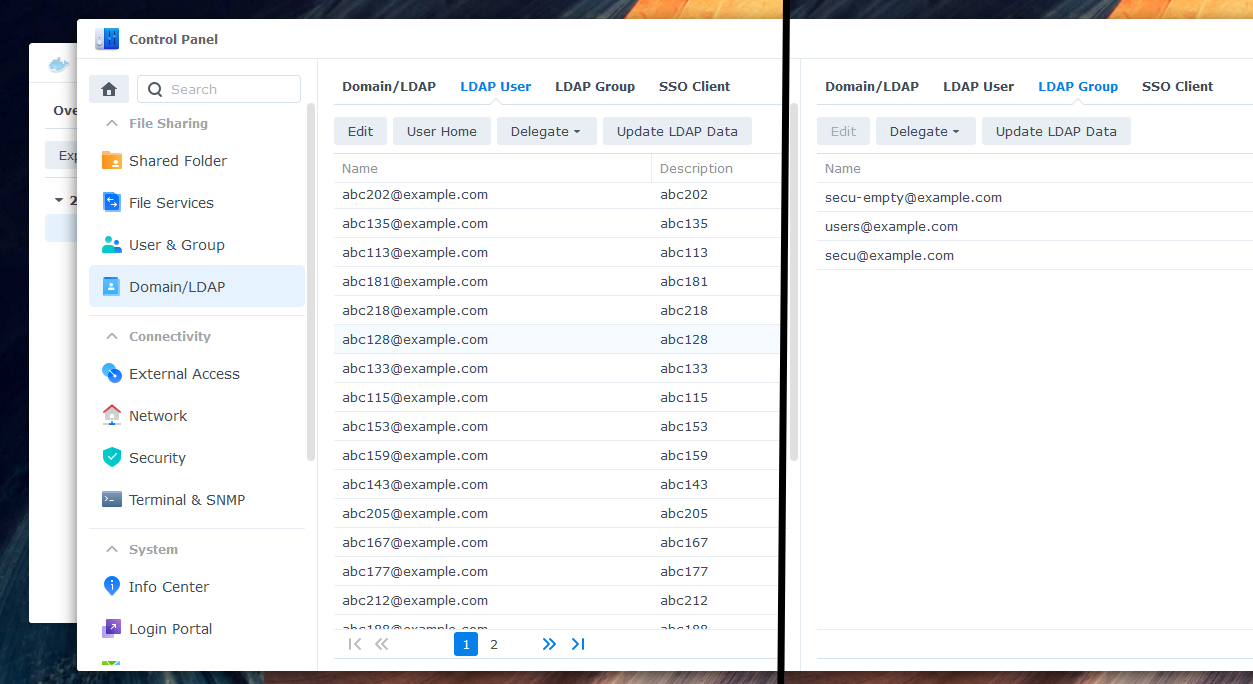
7. Note that before accessing shared folders or files via network or Samba, each user must log in to DSM web GUI or another tool directly connected to the LDAP server. This step is also required after a password change, as the password hash for Samba is only set after a successful login.
@@ -148,19 +150,19 @@ To enable users to log in to Synology NAS with their Azure credentials, you need
To configure the LDAP-wrapper, you can use environment variables as it is intended to be used with Docker. A complete list of available variables can be found in the [configuration settings page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/configuration/settings) of the documentation.
-## Troubleshooting
+## Troubleshooting / FAQ
If you encounter any issues, start by checking the Docker log. Many errors are logged there, and this can help you identify the root cause of the problem. Additionally, the [troubleshooting page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/troubleshooting/) in the documentation provides further guidance on debugging common issues, including Samba-related ones. If you're still stuck, don't hesitate to open an issue, but be sure to attach relevant log files to help others diagnose the issue.
## Security
-It's important to note that the AzureAD-LDAP-wrapper involves transferring sensitive user information, so it's essential to ensure that it's used securely. There are several potential security risks to be aware of when using this wrapper. For more information on these risks and how to mitigate them, please read the [security page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/security/) in the documentation.
+It's important to note that the LDAP-wrapper involves transferring sensitive user information, so it's essential to ensure that it's used securely. There are several potential security risks to be aware of when using this wrapper. For more information on these risks and how to mitigate them, please read the [security page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/security/) in the documentation.
If you discover any security vulnerabilities, please refer to the instructions in [SECURITY.md](SECURITY.md) on how to report them.
## Contributing
-Contributions to the AzureAD-LDAP-wrapper are always welcome! If you have any suggestions, bug reports, or pull requests, please feel free to open an issue or a pull request on the project's GitHub repository.
+Contributions to the LDAP-wrapper are always welcome! If you have any suggestions, bug reports, or pull requests, please feel free to open an issue or a pull request on the project's GitHub repository.
## Support this project
@@ -170,4 +172,4 @@ Your support helps me maintain and improve this project. Thank you!
## License
-The AzureAD-LDAP-wrapper is licensed under the [MIT License](LICENSE).
+The LDAP-wrapper is licensed under the [MIT License](LICENSE).
diff --git a/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js b/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js
new file mode 100644
index 0000000..e8a6d7c
--- /dev/null
+++ b/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js
@@ -0,0 +1,111 @@
+/**
+ * This module contains customizer functions for modifying LDAP and Azure objects.
+ * @module customizer
+ *
+ * Modify the following variables to your needs:
+ * pets - The list of group names to filter the Azure groups by.
+ * Only users within these groups will be synced.
+ */
+
+'use strict';
+
+// keep only users within these groups from Azure
+const pets = ['group-b', 'administrators'];
+
+const config = require('../src/config');
+const helper = require('../src/helper');
+
+var customizer = {};
+
+/**
+ * Modifies the Azure groups by filtering them based on a predefined list of group names.
+ * @param {Array} azuregroups - The array of Azure groups.
+ * @returns {Array} - The modified array of Azure groups.
+ */
+customizer.ModifyAzureGroups = function (azuregroups) {
+ return azuregroups.filter(group => pets.includes(group.displayName.toLowerCase()));
+};
+
+/**
+ * Modifies the LDAP group by converting the gidNumber from string to int.
+ * @param {Object} ldapgroup - The LDAP group object.
+ * @param {Object} azuregroup - The Azure group object.
+ * @returns {Object} - The modified LDAP group object.
+ */
+customizer.ModifyLDAPGroup = function (ldapgroup, azuregroup) {
+ helper.log("customizer", "ModifyLDAPGroup", "called");
+ if (ldapgroup.hasOwnProperty("gidNumber")) {
+ let parsed = parseInt(ldapgroup.gidNumber);
+ if (isNaN(parsed)) parsed = ldapgroup.gidNumber;
+ ldapgroup.gidNumber = parsed;
+ }
+
+ return ldapgroup;
+};
+
+/**
+ * Modifies the LDAP user by converting the gidNumber and uidNumber from string to int.
+ * Sets gidNumber to 0 if the user has no groups.
+ * @param {Object} ldapuser - The LDAP user object.
+ * @param {Object} azureuser - The Azure user object.
+ * @returns {Object} - The modified LDAP user object.
+ */
+customizer.ModifyLDAPUser = function (ldapuser, azureuser) {
+ helper.log("customizer", "ModifyLDAPUser", "called");
+ if (ldapuser.hasOwnProperty("gidNumber")) {
+ let parsed = parseInt(ldapuser.gidNumber);
+ if (isNaN(parsed)) parsed = ldapuser.gidNumber;
+ ldapuser.gidNumber = parsed;
+ }
+ if (ldapuser.hasOwnProperty("uidNumber")) {
+ let parsed = parseInt(ldapuser.uidNumber);
+ if (isNaN(parsed)) parsed = ldapuser.uidNumber;
+ ldapuser.uidNumber = parsed;
+ }
+
+ // no groups for user? set gidNumber to 0
+ ldapuser.memberOf = ldapuser.memberOf.filter(e => e != config.LDAP_USERSGROUPSBASEDN);
+ if (Array.isArray(ldapuser.memberOf) && ldapuser.memberOf.length === 0) ldapuser.gidNumber = 0;
+
+ return ldapuser;
+};
+
+/**
+ * Modifies the LDAP objects globally by setting default values for certain properties.
+ * @param {Object} all - The object containing all LDAP objects.
+ * @returns {Object} - The modified object containing all LDAP objects.
+ */
+customizer.ModifyLDAPGlobal = function (all) {
+ let root = "uid=root," + config.LDAP_USERSDN;
+ for (var key of Object.keys(all)) {
+ all[key].creatorsName = root;
+
+ if (!all[key].hasOwnProperty("createTimestamp"))
+ all[key].createTimestamp = helper.ldap_now() + "Z";
+
+ if (!all[key].hasOwnProperty("entryCSN"))
+ all[key].entryCSN = helper.ldap_now() + ".000000Z#000000#000#000000";
+
+ all[key].modifiersName = root;
+
+ if (!all[key].hasOwnProperty("modifyTimestamp"))
+ all[key].modifyTimestamp = all[key].createTimestamp;
+
+ if (all[key].hasOwnProperty("sambaDomainName")) {
+ all[key].sambaDomainName = all[key].sambaDomainName.toLowerCase();
+ }
+
+ // only users with gidNumber > 0
+ if (all[key].hasOwnProperty("uidNumber")
+ && all[key].hasOwnProperty("gidNumber")
+ && all[key].uidNumber > 0
+ && all[key].gidNumber === 0
+ ) {
+ delete all[key];
+ }
+ }
+
+ return all;
+};
+
+module.exports = customizer;
\ No newline at end of file
diff --git a/docs/content/_index.md b/docs/content/_index.md
index b0e2b34..01f864d 100644
--- a/docs/content/_index.md
+++ b/docs/content/_index.md
@@ -1,12 +1,14 @@
---
-title: AzureAD-LDAP-wrapper
+title: LDAP-wrapper for Microsoft Entra ID
---
-AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from Azure Active Directory to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This enables other applications to connect to the LDAP server and utilize AzureAD login credentials, making it a possible solution for older applications that lack AzureAD support or for scenarios where managing a local AD controller is undesirable.
+LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from `Microsoft Entra ID` (formerly `Azure Active Directory`) to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This allows your other applications to connect to the LDAP server and thus allows your end users to authenticate with a work or school account.
+
+This it a possible workaround for older applications that lack Microsoft Entra ID support or for scenarios where managing a local AD controller is undesirable.
{{< hint type=note title="About the motivation" >}}
-I run the project on my Synology NAS in a Docker container. By connecting the NAS and some intranet web applications to the LDAP server, my users can log in to these services using their AzureAD credentials. Although it is possible to achieve this by [joining the NAS to AADDS](https://kb.synology.com/en-global/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain), I preferred not to maintain such a big setup, which includes a virtual machine, VPN, and AADDS, just to allow my three users to use their credentials almost everywhere.
+I run the project on my Synology NAS in a Docker container. By connecting the NAS and some intranet web applications to the LDAP server, my users can log in to these services using their work accounts. Although it is possible to achieve this by [joining the NAS to AADDS](https://kb.synology.com/en-global/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain), I preferred not to maintain such a big setup, which includes a virtual machine, VPN, and Microsoft Entra Domain Services (formerly AADDS / Azure Active Directory Domain Services), just to allow my three users to use their credentials almost everywhere.
{{< /hint >}}
@@ -16,31 +18,29 @@ I run the project on my Synology NAS in a Docker container. By connecting the NA
sequenceDiagram
autonumber
participant LDAP client
- participant AzureAD-LDAP-wrapper
- participant AAD (Graph API)
-
- Note over AzureAD-LDAP-wrapper: start LDAP server
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups
- Note over AzureAD-LDAP-wrapper: cache users and groups locally
-
- LDAP client->>+AzureAD-LDAP-wrapper: Attempt to bind with user credentials
- AzureAD-LDAP-wrapper->>+AAD (Graph API): Check user credentials
- AAD (Graph API)-->>-AzureAD-LDAP-wrapper: Valid credentials
-
- Note over AzureAD-LDAP-wrapper: save password hash locally in the cache
- AzureAD-LDAP-wrapper->>-LDAP client: Successful bind/authenticate
-
+ participant LDAP-wrapper
+ participant ME-ID (Graph API)
+
+ Note over LDAP-wrapper: start LDAP server
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups
+ Note over LDAP-wrapper: cache users and groups locally
+
+ LDAP client->>+LDAP-wrapper: Attempt to bind with user credentials
+ LDAP-wrapper->>+ME-ID (Graph API): Check user credentials
+ ME-ID (Graph API)-->>-LDAP-wrapper: Valid credentials
+
+ Note over LDAP-wrapper: save password hash locally in the cache
+ LDAP-wrapper->>-LDAP client: Successful bind/authenticate
+
loop every 30 minutes
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups again
- Note over AzureAD-LDAP-wrapper: merge and cache users and groups locally
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups again
+ Note over LDAP-wrapper: merge and cache users and groups locally
end
```
-The diagram shows the flow of communication between an LDAP client, the AzureAD-LDAP-wrapper, and the Azure Active Directory (AAD) via Graph API.
-
-First, the AzureAD-LDAP-wrapper starts an LDAP server and fetches users and groups from the AAD Graph API. These are cached and merged locally.
+The LDAP-wrapper starts an LDAP server and fetches users and groups from the Microsoft Graph API. These are cached and merged locally.
-When an LDAP client attempts to bind with user credentials, the AzureAD-LDAP-wrapper checks these credentials by communicating with the AAD Graph API. If the credentials are valid, the AAD Graph API sends a success response to the AzureAD-LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the AzureAD-LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
+When an LDAP client attempts to bind with user credentials, the LDAP-wrapper checks these credentials by communicating with the Microsoft Graph API. If the credentials are valid, the Microsoft Graph API sends a success response to the LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
-The AzureAD-LDAP-wrapper periodically fetches user and group information from the AAD Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
+The LDAP-wrapper periodically fetches user and group information from the Microsoft Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
diff --git a/docs/content/configuration/bypass-mfa.md b/docs/content/configuration/bypass-mfa.md
index 8a6a4ad..36e875f 100644
--- a/docs/content/configuration/bypass-mfa.md
+++ b/docs/content/configuration/bypass-mfa.md
@@ -2,25 +2,25 @@
title: Bypass MFA
---
-Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
+Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
There is no interactive window to enter another factor, and LDAP does not support this either.
If you need to use this LDAP-wrapper despite of activated MFA, there are two options:
-1. Disable MFA for this application in AzureAD (preferred).\
+1. Disable MFA for this application in your tenant (preferred).\
There are several ways to define MFA, but only some of them allows you to disable MFA.
- Per-user MFA\
- MFA could be [enabled individually](https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates) for each user. A possible workaround seems to be the [trusted IPs feature](https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings#trusted-ips), which allows to disable MFA for some IPs, but this feature requires Azure AD Premium.\
+ MFA could be [enabled individually](https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-userstates) for each user. A possible workaround seems to be the [trusted IPs feature](https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-mfasettings#trusted-ips), which allows to disable MFA for some IPs, but this feature requires Microsoft Entra ID Premium.\
If a login fails due to this MFA method, the error code is AADSTS50079.
- Security defaults\
- [Security defaults](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults) seems to be the only ways for customers using the free Azure AD plan to [enable multi-factor authentication](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-mfa-get-started#free-option) in their whole environment. It looks like there are no workarounds to disable MFA for certain IPs or applications.\
+ [Security defaults](https://learn.microsoft.com/en-us/entra/fundamentals/security-defaults) seems to be the only ways for customers using the free Microsoft Entra ID plan to [enable multi-factor authentication](https://learn.microsoft.com/en-us/entra/identity/authentication/concept-mfa-licensing#free-option) in their whole environment. It looks like there are no workarounds to disable MFA for certain IPs or applications.\
If a login fails due to this MFA method, the error code is AADSTS50076.
- Conditional Access\
- [Conditional Access](https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-all-users-mfa) can be used to require MFA for some or all the users. This is the most flexible way to activate MFA, but it is a premium feature. The settings allows to exclude certain apps. If a login fails due to this MFA method, the error codea are either AADSTS50158 (for external MFA like Duo) or also AADSTS50079. As a simple workaround, the app used by the LDAP-wrapper can be excluded:
- - Add a URL in the app (e.g. "https://localhost")
+ [Conditional Access](https://learn.microsoft.com/en-us/entra/identity/conditional-access/howto-conditional-access-policy-all-users-mfa) can be used to require MFA for some or all the users. This is the most flexible way to activate MFA, but it is a premium feature. The settings allows to exclude certain apps. If a login fails due to this MFA method, the error codea are either AADSTS50158 (for external MFA like Duo) or also AADSTS50079. As a simple workaround, the app used by the LDAP-wrapper can be excluded:
+ - Add a URL in the app (e.g. "")

- The App can now be selected in the exclude list

2. Let the LDAP-wrapper internally treat some MFA/2FA related error codes as a successful login.\
There is an experimental feature to ***bypass*** MFA/2FA. It must be manually enabled by setting the the env var `GRAPH_IGNORE_MFA_ERRORS` to true.\
- Even if the env var is set to true, the login attempt appears as "Failure" in the AzureAD sign-in logs due to MFA/2FA. Only the LDAP wrapper internally treats some MFA/2FA-related error codes as successful logins. Specifically, these are the error codes AADSTS50076, AADSTS50079 and AADSTS50158, as mentioned above.
+ Even if the env var is set to true, the login attempt appears as "Failure" in the Microsoft Entra ID sign-in logs due to MFA/2FA. Only the LDAP wrapper internally treats some MFA/2FA-related error codes as successful logins. Specifically, these are the error codes AADSTS50076, AADSTS50079 and AADSTS50158, as mentioned above.
diff --git a/docs/content/installation/create-azuread-application.md b/docs/content/installation/create-azuread-application.md
index 5251025..2c5986a 100644
--- a/docs/content/installation/create-azuread-application.md
+++ b/docs/content/installation/create-azuread-application.md
@@ -1,21 +1,21 @@
---
-title: 1.1 Create an AzureAD application
+title: 1.1 Register an application with the Microsoft identity platform
---
{{< toc format=raw >}}
## Prerequisites
-To register an application in your Azure AD tenant, you need:
+To register an application with the Microsoft identity platform, you need:
-- An Azure AD user account. If you don't already have one, you can [create an account for free](https://azure.microsoft.com/free/).
+- A Microsoft Entra ID user account. If you don't already have one, you can [create an account for free](https://azure.microsoft.com/free/).
-## Register an application with Azure AD and create a service principal
+## Register an application with the Microsoft identity platform
-Register a new application in your [aad-portal](https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps). More descriptions can be found [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/howto-create-service-principal-portal).
+Register a new application in your [Microsoft Entra Admin Center](https://entra.microsoft.com/#view/Microsoft_AAD_RegisteredApps/ApplicationsListBlade/quickStartType~/null/sourceType/Microsoft_AAD_IAM). More descriptions can be found [here](https://learn.microsoft.com/en-us/entra/identity-platform/howto-create-service-principal-portal).
-- Sign-in to the Azure portal.
-- Select Azure Active Directory and navigateo to [App registrations](https://aad.portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/RegisteredApps).
+- Sign-in to the Microsoft Entra Admin Center.
+- Browse to Identity > Applications > [App registrations](https://entra.microsoft.com/#view/Microsoft_AAD_RegisteredApps/ApplicationsListBlade/quickStartType~/null/sourceType/Microsoft_AAD_IAM)
- Select New registration.
- Name the application, for example "ldap-wrapper".
- Select a supported account type, which determines who can use the application.\
@@ -26,17 +26,17 @@ Register a new application in your [aad-portal](https://aad.portal.azure.com/#bl
## Set permissions
-- Set the following Graph-API Application permissions:
+- Set the following Microsoft Graph API Application permissions:
For type `Application` allow `User.Read.All` and `Group.Read.All`.\
For type `Delegated` allow `User.Read`.\
- 
+ 
- Click "Grant admin consent". The status should be "Granted for".\
If you see en entry with "Not granted for", click again:
- 
+ 
-- Set [Treat application as a public client](https://github.com/AzureAD/microsoft-authentication-library-for-dotnet/wiki/Username-Password-Authentication#application-registration) to `Yes`
-(former "Allow public client flows")
+- Set [Allow public client flows](https://learn.microsoft.com/de-de/entra/msal/dotnet/acquiring-tokens/desktop-mobile/username-password-authentication#application-registration) to `Yes`
+
## Get TenantId, AppId and AppSecret
diff --git a/docs/content/installation/azure_ROPC.png b/docs/content/installation/entra_ROPC.png
similarity index 100%
rename from docs/content/installation/azure_ROPC.png
rename to docs/content/installation/entra_ROPC.png
diff --git a/docs/content/installation/azure_permissions.png b/docs/content/installation/entra_permissions.png
similarity index 100%
rename from docs/content/installation/azure_permissions.png
rename to docs/content/installation/entra_permissions.png
diff --git a/docs/content/installation/azure_permissions_notgranted.png b/docs/content/installation/entra_permissions_notgranted.png
similarity index 100%
rename from docs/content/installation/azure_permissions_notgranted.png
rename to docs/content/installation/entra_permissions_notgranted.png
diff --git a/docs/content/installation/run-ldap-wrapper.md b/docs/content/installation/run-ldap-wrapper.md
index af1f930..3daee9e 100644
--- a/docs/content/installation/run-ldap-wrapper.md
+++ b/docs/content/installation/run-ldap-wrapper.md
@@ -4,7 +4,7 @@ title: Run the LDAP-wrapper
The preferred way to use the LDAP wrapper is with Docker. Alternatively, the source can be downloaded and started manually with npm/node.
-As domain (and basedn, if manually specified) it is recommended to use the same as used in AzureAD tenant (e.g. `@domain.tld`). This way, the spelling of the users (e.g. `username@domain.tld`) will match at the end. Otherwise, your users will have to use `username@example.com` instead of the estimated `username@domain.tld`, for example.
+As domain (and basedn, if manually specified) it is recommended to use the same as used in your Microsoft Entra tenant (e.g. `@domain.tld`). This way, the spelling of the users (e.g. `username@domain.tld`) will match at the end. Otherwise, your users will have to use `username@example.com` instead of the estimated `username@domain.tld`, for example.
{{< hint type=note >}}
The API results and a local copy of the LDAP entries are stored as JSON files inside the container at this path: `/app/.cache`
@@ -35,7 +35,7 @@ Use "bridge" as your network.
4. Give your container a name and enable auto-restart.

-5. Configure the environment variables in "Advanced Settings". Be sure to double check your Azure values and define at least one binduser. The binduser (superuser like root) does not need to exist in your AzureAD. Replace example.com with your domain. Here is an example of a minimum required configuration:
+5. Configure the environment variables in "Advanced Settings". Be sure to double check your AZURE_* values and define at least one binduser. The binduser (superuser like root) does not need to exist in your Microsoft Entra tenant. Replace example.com with your domain. Here is an example of a minimum required configuration:
```bash
TZ: "Europe/Zurich" # optional
@@ -69,6 +69,7 @@ Use "bridge" as your network.
docker run -d `
-p 389:13389 `
--volume /volume1/docker/ldapwrapper:/app/.cache `
+-e TZ="Europe/Zurich" `
-e AZURE_TENANTID="0def2345-ff01-56789-1234-ab9d6dda1e1e" `
-e AZURE_APP_ID="abc12345-ab01-0000-1111-a1e1eab9d6dd" `
-e AZURE_APP_SECRET="iamasecret~yep-reallyreallysecret" `
@@ -141,7 +142,7 @@ You can either set environment variables or create an .env file in the root dire
```env
## .env file or environment variables ##
-# Values of your AzureAD application
+# Values of your Microsoft Entra application
AZURE_APP_ID="abc12345-ab01-0000-1111-a1e1eab9d6dd"
AZURE_TENANTID="0def2345-ff01-56789-1234-ab9d6dda1e1e"
AZURE_APP_SECRET="iamasecret~yep-reallyreallysecret"
diff --git a/docs/content/security/_index.md b/docs/content/security/_index.md
index bf2c799..08eff41 100644
--- a/docs/content/security/_index.md
+++ b/docs/content/security/_index.md
@@ -9,7 +9,7 @@ title: 3. Security
- An LDAP search on the NAS must be possible without any authentication in order to be able to select the domain/baseDN at all.
Therefore, some queries can be run as anonymous by default. Data like domain/baseDN or schema can be fetched without authentication.
- Since this LDAP-wrapper is originally only meant to use the same credentials as in Azure on a NAS, this is the default behaviour.
+ Since this LDAP-wrapper is originally only meant to use my work account (Microsoft Entra Account) on a NAS, this is the default behaviour.
You can change this via the env var `LDAP_ANONYMOUSBIND` if required.
- In order to use samba, the user credentials hashes are cached in the ldap attribute sambaNTPassword.\
@@ -19,13 +19,13 @@ However, if you do not disable the cache, there is a special treatment for these
- Each user has access to his own cached credential hash.
- In all other cases the attribute is returned with XXXX instead of the hash value.
-- In cases such as network/internet issues or Azure not being reachable, the cached hash is used for authentication.\
+- In cases such as network/internet issues or Microsoft Graph API / Entra ID not being reachable, the cached hash is used for authentication.\
This can be a problem if the user has been deactivated in the meantime or the password would be invalid.
The use of the cached password during authentication can be disabled by setting the `LDAP_ALLOWCACHEDLOGINONFAILURE` parameter to false.
- Using the experimental feature to bypass MFA/2FA\
- Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
- There is an experimental feature to **bypass** MFA/2FA. It must be manually enabled by setting the the env var `GRAPH_IGNORE_MFA_ERRORS` to true. Even if the env var is set to true, the login attempt appears as "Failure" in the AzureAD sign-in logs due to MFA/2FA. It is only the LDAP-wrapper that internally treats some MFA/2FA related error codes as a successful login.
+ Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
+ There is an experimental feature to **bypass** MFA/2FA. It must be manually enabled by setting the the env var `GRAPH_IGNORE_MFA_ERRORS` to true. Even if the env var is set to true, the login attempt appears as "Failure" in the Microsoft Entra ID sign-in logs due to MFA/2FA. It is only the LDAP-wrapper that internally treats some MFA/2FA related error codes as a successful login.
- Mapped docker volume\
Be aware that other users with access on your file system may also be able to read the JSON files in the mounted docker path (/app/.cache) and thus get access to the cached sambaNTPassword attribute.
diff --git a/docs/content/troubleshooting/_index.md b/docs/content/troubleshooting/_index.md
index 9bf97bc..b3a8c36 100644
--- a/docs/content/troubleshooting/_index.md
+++ b/docs/content/troubleshooting/_index.md
@@ -9,15 +9,15 @@ The first step is always to look at the Docker log. Many errors are handled ther
- [How do I give some synced users the DSM-Administrator permission on a Synology-NAS?](#how-do-i-give-some-synced-users-the-dsm-administrator-permission-on-a-synology-nas)
- [Can I use LDAPS (LDAP over SSL) instead of LDAP (with no encryption)?](#can-i-use-ldaps-ldap-over-ssl-instead-of-ldap-with-no-encryption)
- [Can I use LDAP over TLS (STARTTLS) instead of LDAP (with no encryption)?](#can-i-use-ldap-over-tls-starttls-instead-of-ldap-with-no-encryption)
-- [Join NAS to Azure AD Domain](#join-nas-to-azure-ad-domain)
+- [Join NAS to Microsoft Entra Domain Services](#join-nas-to-microsoft-entra-domain-services)
- [Why are personal microsoft accounts not supported?](#why-are-personal-microsoft-accounts-not-supported)
- [Samba is not working, what can I do?](#samba-is-not-working-what-can-i-do)
-- [Are deleted users or groups in Azure also removed from the LDAP entries?](#are-deleted-users-or-groups-in-azure-also-removed-from-the-ldap-entries)
+- [Are deleted users or groups in Entra also removed from the LDAP entries?](#are-deleted-users-or-groups-in-entra-also-removed-from-the-ldap-entries)
## Does it support MFA (multi-factor authentication)?
Yes and no... There is an experimental feature to bypass MFA/2FA. It can be enabled by setting the the env var `GRAPH_IGNORE_MFA_ERRORS` to `true`.
-Officially no, because the login simply fails, as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93). Even if the env var is set to true, the login attempt appears as "Failure" in the AzureAD sign-in logs due to MFA/2FA. It is only the LDAP-wrapper that internally treats some MFA/2FA related error codes as a successful login.
+Officially no, because the login simply fails, as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93). Even if the env var is set to true, the login attempt appears as "Failure" in the Microsoft Entra sign-in logs due to MFA/2FA. It is only the LDAP-wrapper that internally treats some MFA/2FA related error codes as a successful login.
## How do I give some synced users the DSM-Administrator permission on a Synology-NAS?
@@ -32,15 +32,15 @@ Sure. Mount your certificate file and private key file to the docker container a
Nope, that's not (yet) possible.
-## Join NAS to Azure AD Domain
+## Join NAS to Microsoft Entra Domain Services
-If you don't need support for older software, the officially Synology solution to [join your NAS to a Azure AD Domain](https://kb.synology.com/en-my/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain) will work fine.
+If you don't need support for older software, the officially Synology solution to [join your NAS to a Microsoft Entra Domain Services](https://kb.synology.com/en-my/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain) will work fine.
My wrapper creates an entire ldap server. So you can use it with several 3rd party (legacy) software in the same network.
## Why are personal microsoft accounts not supported?
-This wrapper uses the ROPC flow for authentication. Microsoft doesn't support that for personal accounts as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc):
-> Personal accounts that are invited to an Azure AD tenant can't use ROPC.
+This wrapper uses the ROPC flow for authentication. Microsoft doesn't support that for personal accounts as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc):
+> Personal accounts that are invited to an Microsoft Entra tenant can't use ROPC.
## Samba is not working, what can I do?
@@ -51,7 +51,7 @@ Check the following points first:
- Look into the docker Log. Are there any errors you should resolve? 
- Did you really connect your device/NAS with a non-existing user from the env var `LDAP_BINDUSER`? Otherwise the required password hash for Samba is not available and access will fail.
- Before accessing files via network/Samba, each user must log in to dsm-web-gui or another tool that is directly connected to the ldap server. This also applies after a password change, since the password hash for Samba is only set after a successful login.
-- Is your (Windows) device connected to Azure? Make sure you log in with username/password over the network, not with your pin code.
+- Is your (Windows) device connected to Microsoft Entra (formerly Azure AD joined devices)? Make sure you log in with username/password over the network, not with your pin code.
- Can you successfully access the shares with a local user?
- Make sure Synology Directory Service and Synology LDAP server are not installed.
- Maybe there is someting in the samba log. Get it to open an issue:
@@ -62,6 +62,6 @@ Check the following points first:
- Run `cat /var/log/samba/log.smbd` and copy the latest error/fail/... messages - please replace sensitive informations like domains, ip addresses or names.
- Don't forget to disable "collect debug logs" before opening an issue
-## Are deleted users or groups in Azure also removed from the LDAP entries?
+## Are deleted users or groups in Entra also removed from the LDAP entries?
-Yes, but with a delay. After a user has been deleted in Azure, it remains available there for about 30 days to undo the deletion. The API stops listing the user a earlier, a few hours after the deletion. In the meantime, the wrapper fetches the user as usual. After this time, the wrapper no longer receives the user. The deletion in the wrapper takes place 7 days later. Why not removing the user immediately? A user could also no longer be in the wrapper due to a misconfigured filter (env var). But just because of such an error, users (and their cached password hashes) should not be deleted immediately. Why not keeping it also 30 days? The user can no longer log in anyway. If the time span is too long (or short), it can be adjusted via the environment variable LDAP_DAYSTOKEEPDELETEDUSERS.
\ No newline at end of file
+Yes, but with a delay. After a user has been deleted in Microsoft Entra, it remains available there for about 30 days to undo the deletion. The API stops listing the user a earlier, a few hours after the deletion. In the meantime, the wrapper fetches the user as usual. After this time, the wrapper no longer receives the user. The deletion in the wrapper takes place 7 days later. Why not removing the user immediately? A user could also no longer be in the wrapper due to a misconfigured filter (env var). But just because of such an error, users (and their cached password hashes) should not be deleted immediately. Why not keeping it also 30 days? The user can no longer log in anyway. If the time span is too long (or short), it can be adjusted via the environment variable LDAP_DAYSTOKEEPDELETEDUSERS.
diff --git a/docs/content/usage/_index.md b/docs/content/usage/_index.md
new file mode 100644
index 0000000..7f87476
--- /dev/null
+++ b/docs/content/usage/_index.md
@@ -0,0 +1,9 @@
+---
+title: Usage examples
+---
+
+{{< hint type=note >}}
+
+Some examples how to use the LDAP-wrapper. This may also help configure similar services/apps.
+
+{{< /hint >}}
diff --git a/docs/content/usage/authelia.md b/docs/content/usage/authelia.md
new file mode 100644
index 0000000..98af88b
--- /dev/null
+++ b/docs/content/usage/authelia.md
@@ -0,0 +1,89 @@
+---
+title: 6.2 Authelia with LDAP-wrapper
+---
+
+Authelia supports LDAP authentication, enabling users to log in by authenticating against your LDAP directory. This guide outlines the steps to set up LDAP authentication with Authelia using LDAP-wrapper.
+
+{{< toc format=raw >}}
+
+## Prerequisites
+
+Before configuring LDAP authentication for Authelia with LDAP-wrapper, ensure the following prerequisites are met:
+
+- **LDAP-wrapper**: Ensure you have a functioning [LDAP-wrapper](https://github.com/ahaenggli/AzureAD-LDAP-wrapper/).
+- **Authelia**: Set up and configure [Authelia](https://www.authelia.com/overview/prologue/introduction/) for your environment.
+
+## Settings for Authelia LDAP Authentication with LDAP-wrapper
+
+To configure LDAP authentication with Authelia using LDAP-wrapper, follow these steps:
+
+1. Open your `configuration.yml` file in the Authelia configuration directory.
+2. Locate the `authentication_backend` section and configure it with the following example, adjusting the `url`,`base_dn`, `user`, and `password` based on your LDAP-wrapper setup:
+
+```yaml
+ ## Authentication Backend Provider Configuration
+ authentication_backend:
+
+ ## Password Reset Options
+ password_reset:
+ ## Disable both the HTML element and the API for reset password functionality.
+ disable: true
+ ## External reset password url for Microsoft
+ custom_url: "https://account.activedirectory.windowsazure.com/ChangePassword.aspx"
+
+ ## The amount of time to wait before we refresh data from the authentication backend. Uses duration notation
+ ## See the below documentation for more information
+ ## Duration Notation docs:
+ ## Refresh Interval docs:
+ refresh_interval: 5m
+
+ ##
+ ## LDAP (Authentication Provider)
+ ##
+ ldap:
+ ## The LDAP implementation, this affects elements like the attribute utilised for resetting a password.
+ implementation: custom
+ ## The url to the ldap server. Format: ://[:].
+ url: ldap://my-nas-name.local:389
+ ## The dial timeout for LDAP.
+ timeout: 5s
+ ## Use StartTLS with the LDAP connection.
+ start_tls: false
+ tls:
+ ## Server Name for certificate validation (in case it's not set correctly in the URL).
+ # server_name: ldap.domain.tld
+ ## Skip verifying the server certificate (to allow a self-signed certificate).
+ skip_verify: false
+ ## Minimum TLS version for either Secure LDAP or LDAP StartTLS.
+ minimum_version: TLS1.2
+ ## The distinguished name of the container searched for objects in the directory information tree.
+ base_dn: dc=domain,dc=tld
+ ## The attribute holding the username of the user. This attribute is used to populate the username in the session
+ username_attribute: uid
+ ## The additional_users_dn is prefixed to base_dn and delimited by a comma when searching for users.
+ additional_users_dn: cn=users
+ ## The users filter used in search queries to find the user profile based on input filled in login form.
+ users_filter: (&(|({username_attribute}={input})({mail_attribute}={input}))(objectClass=person))
+ ## The additional_groups_dn is prefixed to base_dn and delimited by a comma when searching for groups.
+ additional_groups_dn: cn=groups
+ ## The groups filter used in search queries to find the groups based on relevant authenticated user.
+ groups_filter: (&(member={dn})(objectClass=posixGroup))
+ ## The attribute holding the name of the group.
+ group_name_attribute: cn
+ ## The attribute holding the mail address of the user. If multiple email addresses are defined for a user, only the
+ mail_attribute: mail
+ ## The attribute holding the display name of the user. This will be used to greet an authenticated user.
+ display_name_attribute: displayName
+ ## Follow referrals returned by the server.
+ ## This is especially useful for environments where read-only servers exist. Only implemented for write operations.
+ permit_referrals: false
+ ## The username and password of the admin user, matching an entry of your LDAP-wrapper environment variable `LDAP_BINDUSER`.
+ user: uid=root
+ ## Password can also be set using a secret:
+ password: 1234
+```
+
+3. Save the changes to your `configuration.yml` file.
+4. Restart Authelia to apply the new configuration.
+
+Now, Authelia is configured to authenticate users against your LDAP directory through LDAP-wrapper.
diff --git a/docs/content/usage/portainer.md b/docs/content/usage/portainer.md
new file mode 100644
index 0000000..3479749
--- /dev/null
+++ b/docs/content/usage/portainer.md
@@ -0,0 +1,41 @@
+---
+title: 6.1 Portainer
+---
+
+Portainer supports LDAP authentication, allowing users to log in by authenticating against your LDAP directory. This guide outlines the steps to set up LDAP authentication over LDAP-wrapper with Portainer.
+
+{{< toc format=raw >}}
+
+## Prerequisites
+
+Before configuring LDAP authentication for Portainer, ensure the following prerequisites are met:
+
+- **LDAP-wrapper**: Make sure you have a working [LDAP-wrapper](https://github.com/ahaenggli/AzureAD-LDAP-wrapper/).
+- **Portainer**: Install and set up a working instance of [Portainer](https://docs.portainer.io/start/install-ce).
+
+## Settings for Portainer LDAP Authentication with LDAP-wrapper
+
+### LDAP Configuration
+
+- **LDAP Server**: Specify the IP or name of your NAS with Port 389.
+ Example: `192.168.1.2:389` or `my-nas-name.local:389`
+- **Reader DN**: Set it to `uid=root`, matching an entry of your LDAP-wrapper environment variable `LDAP_BINDUSER`.
+- **Password**: Set it to the password corresponding to the entry in your LDAP-wrapper environment variable `LDAP_BINDUSER`.
+
+### LDAP Security
+
+- Ensure that `StartTLS`, `Use TLS`, and `Skip verification` are set to off.
+
+### User Search Configurations
+
+- **Base DN**: Define the base DN as `cn=users,dc=domain,dc=tld`.
+- **Username Attribute**: Specify `mail`.
+- **Filter**: Use the following filter to restrict access:
+
+ ```plaintext
+ (|(&(uid=*)(memberOf=cn=users,cn=groups,dc=domain,dc=tld))(&(cn=administrators)))
+ ```
+
+ This filter ensures that only users within the administrators group can log into Portainer.
+
+Don't forget to save your LDAP-wrapper configuration. Now, users attempting to log into Portainer will be authenticated against your LDAP directory. Only users within the administrators group, as specified in the LDAP filter, will be allowed access to Portainer.
diff --git a/docs/content/usage/radius_settings_certs.png b/docs/content/usage/radius_settings_certs.png
new file mode 100644
index 0000000..c31975e
Binary files /dev/null and b/docs/content/usage/radius_settings_certs.png differ
diff --git a/docs/content/usage/radius_settings_clients.png b/docs/content/usage/radius_settings_clients.png
new file mode 100644
index 0000000..a57b489
Binary files /dev/null and b/docs/content/usage/radius_settings_clients.png differ
diff --git a/docs/content/usage/radius_settings_common.png b/docs/content/usage/radius_settings_common.png
new file mode 100644
index 0000000..7a3caa3
Binary files /dev/null and b/docs/content/usage/radius_settings_common.png differ
diff --git a/docs/content/usage/radius_unifi_profiles_detail.png b/docs/content/usage/radius_unifi_profiles_detail.png
new file mode 100644
index 0000000..0007e0f
Binary files /dev/null and b/docs/content/usage/radius_unifi_profiles_detail.png differ
diff --git a/docs/content/usage/radius_unifi_profiles_find.png b/docs/content/usage/radius_unifi_profiles_find.png
new file mode 100644
index 0000000..89f3d43
Binary files /dev/null and b/docs/content/usage/radius_unifi_profiles_find.png differ
diff --git a/docs/content/usage/radius_unifi_wlan_detail.png b/docs/content/usage/radius_unifi_wlan_detail.png
new file mode 100644
index 0000000..57ca227
Binary files /dev/null and b/docs/content/usage/radius_unifi_wlan_detail.png differ
diff --git a/docs/content/usage/radius_unifi_wlan_new.png b/docs/content/usage/radius_unifi_wlan_new.png
new file mode 100644
index 0000000..2a6c6a2
Binary files /dev/null and b/docs/content/usage/radius_unifi_wlan_new.png differ
diff --git a/docs/content/usage/synology-radius-unifi.md b/docs/content/usage/synology-radius-unifi.md
new file mode 100644
index 0000000..1316779
--- /dev/null
+++ b/docs/content/usage/synology-radius-unifi.md
@@ -0,0 +1,88 @@
+---
+title: 6.3 Synology Radius with UniFi
+---
+
+UniFi allows you to use a custom Radius server like the default package from Synology. Combined with the LDAP-wrapper, this creates a powerful setup for your users.
+
+{{< hint type=tip title="This setup was successfully tested with these versions">}}
+DSM 7.2.1-69057 Update 3
+LDAP-wrapper v2.0.2
+RADIUS Server Package 3.0.25-0515
+UniFi Network Application 8.0.24
+{{< /hint >}}
+
+{{< toc format=raw >}}
+
+## Prerequisites
+
+Before configuring Synology Radius and UniFi, ensure the following prerequisites are met:
+
+- **Synology NAS**: Ensure you are up to date with your DSM, and install the current RADIUS Server package.
+- **LDAP-wrapper**: Ensure you have a functioning [LDAP-wrapper](https://github.com/ahaenggli/AzureAD-LDAP-wrapper/).
+- **UniFi AP**: Ensure you are up to date and have access to your controller settings.
+
+## Settings in Synology RADIUS Server
+
+1. Open the RADIUS Server package on your Synology NAS.
+
+2. Configure the RADIUS `Common Settings` with the following parameters:
+
+ - **Authentication port**: Set the RADIUS Server's port number for interface protocols. The default value is 1812 for authentication.
+ - **Select network interface**: Choose the network interfaces connected to RADIUS client devices (e.g., a router). RADIUS Server provides authentication services only for access requests coming from the specified interface.
+ - **TLS/SSL profile level**: Choose "Intermediate compatibility," which is the default setting. This option is recommended because it is compatible with general-purpose browsers but is not compatible with insecure cipher suites.
+ - **Source for user authentication**: Enable LDAP users.
+
+ 
+
+3. Check your certificates.
+
+ - RADIUS Server requires a valid certificate.
+
+ 
+
+4. Configure the RADIUS `Clients` by adding clients based on the IP address range.
+
+ {{< hint type=warning title="Important Notice">}}
+ Each UniFi AP will directly contact your Synology RADIUS Server. Ensure that your firewall allows all those APs to connect to your NAS with the previously defined port (e.g., 1812).
+ {{< /hint >}}
+
+ To set up clients by IP address range:
+
+ - Click **Add** and choose **Subnet**, then enter the following information:
+
+ - **Name**: Enter a display name for the collection of clients, making it easier to identify.
+ - **IP address**: Enter the base IP addresses of the RADIUS clients (e.g., 192.168.10.1).
+ - **Subnet mask**: Enter a subnet mask, for example, 255.255.255.0.
+ - **Shared secret**: Enter a text string used as a password between the clients and RADIUS Server. This secret will also be needed in your UniFi configuration.
+
+ 
+
+## Settings in UniFi Controller
+
+1. Log in to your UniFi controller.
+2. Navigate to **Settings > Profiles > RADIUS** and create a new entry.
+
+ 
+
+ - Enable **Wired Networks**.
+ - Enable **Wireless Networks**.
+ - Enter the IP address of your Synology NAS in the **IP Address** field.
+ - Specify the RADIUS authentication port (typically 1812) in the **Port** field.
+ - Enter the same shared secret configured in the Synology RADIUS Server in the **Shared Secret** field.
+ - Disable **Accounting**.
+
+ 
+
+3. Navigate to the **Wireless Networks** section (**Settings > WiFi**) and edit your network.
+
+ 
+
+4. Edit the Wireless Network where you want to enable RADIUS authentication.
+ - Enable **WPA Enterprise**.
+ - Select the previously added RADIUS Profile.
+
+ 
+
+5. Save the settings and apply the changes to your UniFi network.
+
+Now, UniFi is configured to use the Synology RADIUS Server for authentication. Users authenticated through UniFi will be verified against your LDAP directory using LDAP-wrapper, creating a robust and secure setup.
diff --git a/docs/data/menu/main.yaml b/docs/data/menu/main.yaml
index 757f90e..965cd03 100644
--- a/docs/data/menu/main.yaml
+++ b/docs/data/menu/main.yaml
@@ -4,24 +4,24 @@ main:
ref: /
- name: 1. Installation
- ref: "/installation"
+ ref: '/installation'
sub:
- name: 1.1 Create an AzureAD application
- ref: "/installation/create-azuread-application"
+ ref: '/installation/create-azuread-application'
- name: 1.2 Run the LDAP-wrapper
- ref: "/installation/run-ldap-wrapper"
+ ref: '/installation/run-ldap-wrapper'
- name: 1.3 Use on a Synology NAS
- ref: "/installation/use-synology-nas"
+ ref: '/installation/use-synology-nas'
- name: 2. Configuration
ref: /configuration
sub:
- name: 2.1 Settings
- ref: "/configuration/settings"
+ ref: '/configuration/settings'
- name: 2.2 Bypass MFA
- ref: "/configuration/bypass-mfa"
+ ref: '/configuration/bypass-mfa'
- name: 2.3 Customize attributes
- ref: "/configuration/customize-attributes"
+ ref: '/configuration/customize-attributes'
- name: 4. Security
ref: /security
@@ -29,3 +29,12 @@ main:
- name: 5. Troubleshooting
ref: /troubleshooting
+ - name: 6. Usage examples
+ ref: /usage
+ sub:
+ - name: 6.1 Portainer
+ ref: '/usage/portainer'
+ - name: 6.2 Authelia
+ ref: '/usage/authelia'
+ - name: 6.3 Synology Radius with UniFi
+ ref: '/usage/synology-radius-unifi'
diff --git a/package-lock.json b/package-lock.json
index 10b73c7..cc3065f 100644
--- a/package-lock.json
+++ b/package-lock.json
@@ -1,32 +1,32 @@
{
"name": "AzureAD-LDAP-wrapper",
- "version": "2.0.1",
+ "version": "2.0.2",
"lockfileVersion": 3,
"requires": true,
"packages": {
"": {
"name": "AzureAD-LDAP-wrapper",
- "version": "2.0.1",
+ "version": "2.0.2",
"license": "MIT",
"dependencies": {
- "@azure/msal-node": "2.2.0",
- "axios": "~1.6.0",
+ "@azure/msal-node": "2.6.1",
+ "axios": "~1.6.5",
"diacritic": "0.0.2",
"dotenv": "^16.3.1",
"fs": "0.0.1-security",
"hashcode": "1.0.3",
"https-proxy-agent": "7.0.2",
- "ldapjs": "~3.0.5"
+ "ldapjs": "~3.0.7"
},
"devDependencies": {
- "eslint": "^8.51.0",
+ "eslint": "^8.56.0",
"eslint-config-standard": "^17.1.0",
- "eslint-plugin-import": "^2.28.1",
- "eslint-plugin-jest": "^27.4.2",
- "eslint-plugin-n": "^16.2.0",
+ "eslint-plugin-import": "^2.29.1",
+ "eslint-plugin-jest": "^27.6.2",
+ "eslint-plugin-n": "^16.6.2",
"eslint-plugin-node": "~11.1.0",
"eslint-plugin-promise": "^6.1.1",
- "eslint-plugin-security": "~1.7.1",
+ "eslint-plugin-security": "~2.1.0",
"jest": "^29.7.0"
},
"engines": {
@@ -56,33 +56,33 @@
}
},
"node_modules/@azure/msal-common": {
- "version": "14.1.0",
- "resolved": "https://registry.npmjs.org/@azure/msal-common/-/msal-common-14.1.0.tgz",
- "integrity": "sha512-xphmhcfl5VL+uq5//VKMwQn+wfEZLMKNpFCcMi8Ur8ej5UT166g6chBsxgMzc9xo9Y24R9FB3m/tjDiV03xMIA==",
+ "version": "14.6.0",
+ "resolved": "https://registry.npmjs.org/@azure/msal-common/-/msal-common-14.6.0.tgz",
+ "integrity": "sha512-AGusT/JvxdzJIYi5u0n97cmhd3pUT6UuI6rEkT5iDeT2FGcV0/EB8pk+dy6GLPpYg9vhDCuyoYrEZGd+2UeCCQ==",
"engines": {
"node": ">=0.8.0"
}
},
"node_modules/@azure/msal-node": {
- "version": "2.2.0",
- "resolved": "https://registry.npmjs.org/@azure/msal-node/-/msal-node-2.2.0.tgz",
- "integrity": "sha512-aZZ1m7OATOR9kz7+/Kl+/LZrNEj+HYaEH84XZfnBtN/9JPRazngk1XTjvAkh7W1u/O/yQrlYiiSwSAKHnNBc8A==",
+ "version": "2.6.1",
+ "resolved": "https://registry.npmjs.org/@azure/msal-node/-/msal-node-2.6.1.tgz",
+ "integrity": "sha512-wYwz83pWatTNWUCkTi3cAOXbchad5FnZz/pbZz7b8Z6FuEqohXcTtg6BLip9SmcjN6FlbwUdJIZYOof2v1Gnrg==",
"dependencies": {
- "@azure/msal-common": "14.1.0",
+ "@azure/msal-common": "14.6.0",
"jsonwebtoken": "^9.0.0",
"uuid": "^8.3.0"
},
"engines": {
- "node": "18 || 20"
+ "node": ">=16"
}
},
"node_modules/@babel/code-frame": {
- "version": "7.22.13",
- "resolved": "https://registry.npmjs.org/@babel/code-frame/-/code-frame-7.22.13.tgz",
- "integrity": "sha512-XktuhWlJ5g+3TJXc5upd9Ks1HutSArik6jf2eAjYFyIOf4ej3RN+184cZbzDvbPnuTJIUhPKKJE3cIsYTiAT3w==",
+ "version": "7.23.5",
+ "resolved": "https://registry.npmjs.org/@babel/code-frame/-/code-frame-7.23.5.tgz",
+ "integrity": "sha512-CgH3s1a96LipHCmSUmYFPwY7MNx8C3avkq7i4Wl3cfa662ldtUe4VM1TPXX70pfmrlWTb6jLqTYrZyT2ZTJBgA==",
"dev": true,
"dependencies": {
- "@babel/highlight": "^7.22.13",
+ "@babel/highlight": "^7.23.4",
"chalk": "^2.4.2"
},
"engines": {
@@ -161,30 +161,30 @@
}
},
"node_modules/@babel/compat-data": {
- "version": "7.23.2",
- "resolved": "https://registry.npmjs.org/@babel/compat-data/-/compat-data-7.23.2.tgz",
- "integrity": "sha512-0S9TQMmDHlqAZ2ITT95irXKfxN9bncq8ZCoJhun3nHL/lLUxd2NKBJYoNGWH7S0hz6fRQwWlAWn/ILM0C70KZQ==",
+ "version": "7.23.5",
+ "resolved": "https://registry.npmjs.org/@babel/compat-data/-/compat-data-7.23.5.tgz",
+ "integrity": "sha512-uU27kfDRlhfKl+w1U6vp16IuvSLtjAxdArVXPa9BvLkrr7CYIsxH5adpHObeAGY/41+syctUWOZ140a2Rvkgjw==",
"dev": true,
"engines": {
"node": ">=6.9.0"
}
},
"node_modules/@babel/core": {
- "version": "7.23.2",
- "resolved": "https://registry.npmjs.org/@babel/core/-/core-7.23.2.tgz",
- "integrity": "sha512-n7s51eWdaWZ3vGT2tD4T7J6eJs3QoBXydv7vkUM06Bf1cbVD2Kc2UrkzhiQwobfV7NwOnQXYL7UBJ5VPU+RGoQ==",
+ "version": "7.23.7",
+ "resolved": "https://registry.npmjs.org/@babel/core/-/core-7.23.7.tgz",
+ "integrity": "sha512-+UpDgowcmqe36d4NwqvKsyPMlOLNGMsfMmQ5WGCu+siCe3t3dfe9njrzGfdN4qq+bcNUt0+Vw6haRxBOycs4dw==",
"dev": true,
"dependencies": {
"@ampproject/remapping": "^2.2.0",
- "@babel/code-frame": "^7.22.13",
- "@babel/generator": "^7.23.0",
- "@babel/helper-compilation-targets": "^7.22.15",
- "@babel/helper-module-transforms": "^7.23.0",
- "@babel/helpers": "^7.23.2",
- "@babel/parser": "^7.23.0",
+ "@babel/code-frame": "^7.23.5",
+ "@babel/generator": "^7.23.6",
+ "@babel/helper-compilation-targets": "^7.23.6",
+ "@babel/helper-module-transforms": "^7.23.3",
+ "@babel/helpers": "^7.23.7",
+ "@babel/parser": "^7.23.6",
"@babel/template": "^7.22.15",
- "@babel/traverse": "^7.23.2",
- "@babel/types": "^7.23.0",
+ "@babel/traverse": "^7.23.7",
+ "@babel/types": "^7.23.6",
"convert-source-map": "^2.0.0",
"debug": "^4.1.0",
"gensync": "^1.0.0-beta.2",
@@ -200,12 +200,12 @@
}
},
"node_modules/@babel/generator": {
- "version": "7.23.0",
- "resolved": "https://registry.npmjs.org/@babel/generator/-/generator-7.23.0.tgz",
- "integrity": "sha512-lN85QRR+5IbYrMWM6Y4pE/noaQtg4pNiqeNGX60eqOfo6gtEj6uw/JagelB8vVztSd7R6M5n1+PQkDbHbBRU4g==",
+ "version": "7.23.6",
+ "resolved": "https://registry.npmjs.org/@babel/generator/-/generator-7.23.6.tgz",
+ "integrity": "sha512-qrSfCYxYQB5owCmGLbl8XRpX1ytXlpueOb0N0UmQwA073KZxejgQTzAmJezxvpwQD9uGtK2shHdi55QT+MbjIw==",
"dev": true,
"dependencies": {
- "@babel/types": "^7.23.0",
+ "@babel/types": "^7.23.6",
"@jridgewell/gen-mapping": "^0.3.2",
"@jridgewell/trace-mapping": "^0.3.17",
"jsesc": "^2.5.1"
@@ -215,14 +215,14 @@
}
},
"node_modules/@babel/helper-compilation-targets": {
- "version": "7.22.15",
- "resolved": "https://registry.npmjs.org/@babel/helper-compilation-targets/-/helper-compilation-targets-7.22.15.tgz",
- "integrity": "sha512-y6EEzULok0Qvz8yyLkCvVX+02ic+By2UdOhylwUOvOn9dvYc9mKICJuuU1n1XBI02YWsNsnrY1kc6DVbjcXbtw==",
+ "version": "7.23.6",
+ "resolved": "https://registry.npmjs.org/@babel/helper-compilation-targets/-/helper-compilation-targets-7.23.6.tgz",
+ "integrity": "sha512-9JB548GZoQVmzrFgp8o7KxdgkTGm6xs9DW0o/Pim72UDjzr5ObUQ6ZzYPqA+g9OTS2bBQoctLJrky0RDCAWRgQ==",
"dev": true,
"dependencies": {
- "@babel/compat-data": "^7.22.9",
- "@babel/helper-validator-option": "^7.22.15",
- "browserslist": "^4.21.9",
+ "@babel/compat-data": "^7.23.5",
+ "@babel/helper-validator-option": "^7.23.5",
+ "browserslist": "^4.22.2",
"lru-cache": "^5.1.1",
"semver": "^6.3.1"
},
@@ -277,9 +277,9 @@
}
},
"node_modules/@babel/helper-module-transforms": {
- "version": "7.23.0",
- "resolved": "https://registry.npmjs.org/@babel/helper-module-transforms/-/helper-module-transforms-7.23.0.tgz",
- "integrity": "sha512-WhDWw1tdrlT0gMgUJSlX0IQvoO1eN279zrAUbVB+KpV2c3Tylz8+GnKOLllCS6Z/iZQEyVYxhZVUdPTqs2YYPw==",
+ "version": "7.23.3",
+ "resolved": "https://registry.npmjs.org/@babel/helper-module-transforms/-/helper-module-transforms-7.23.3.tgz",
+ "integrity": "sha512-7bBs4ED9OmswdfDzpz4MpWgSrV7FXlc3zIagvLFjS5H+Mk7Snr21vQ6QwrsoCGMfNC4e4LQPdoULEt4ykz0SRQ==",
"dev": true,
"dependencies": {
"@babel/helper-environment-visitor": "^7.22.20",
@@ -329,9 +329,9 @@
}
},
"node_modules/@babel/helper-string-parser": {
- "version": "7.22.5",
- "resolved": "https://registry.npmjs.org/@babel/helper-string-parser/-/helper-string-parser-7.22.5.tgz",
- "integrity": "sha512-mM4COjgZox8U+JcXQwPijIZLElkgEpO5rsERVDJTc2qfCDfERyob6k5WegS14SX18IIjv+XD+GrqNumY5JRCDw==",
+ "version": "7.23.4",
+ "resolved": "https://registry.npmjs.org/@babel/helper-string-parser/-/helper-string-parser-7.23.4.tgz",
+ "integrity": "sha512-803gmbQdqwdf4olxrX4AJyFBV/RTr3rSmOj0rKwesmzlfhYNDEs+/iOcznzpNWlJlIlTJC2QfPFcHB6DlzdVLQ==",
"dev": true,
"engines": {
"node": ">=6.9.0"
@@ -347,32 +347,32 @@
}
},
"node_modules/@babel/helper-validator-option": {
- "version": "7.22.15",
- "resolved": "https://registry.npmjs.org/@babel/helper-validator-option/-/helper-validator-option-7.22.15.tgz",
- "integrity": "sha512-bMn7RmyFjY/mdECUbgn9eoSY4vqvacUnS9i9vGAGttgFWesO6B4CYWA7XlpbWgBt71iv/hfbPlynohStqnu5hA==",
+ "version": "7.23.5",
+ "resolved": "https://registry.npmjs.org/@babel/helper-validator-option/-/helper-validator-option-7.23.5.tgz",
+ "integrity": "sha512-85ttAOMLsr53VgXkTbkx8oA6YTfT4q7/HzXSLEYmjcSTJPMPQtvq1BD79Byep5xMUYbGRzEpDsjUf3dyp54IKw==",
"dev": true,
"engines": {
"node": ">=6.9.0"
}
},
"node_modules/@babel/helpers": {
- "version": "7.23.2",
- "resolved": "https://registry.npmjs.org/@babel/helpers/-/helpers-7.23.2.tgz",
- "integrity": "sha512-lzchcp8SjTSVe/fPmLwtWVBFC7+Tbn8LGHDVfDp9JGxpAY5opSaEFgt8UQvrnECWOTdji2mOWMz1rOhkHscmGQ==",
+ "version": "7.23.8",
+ "resolved": "https://registry.npmjs.org/@babel/helpers/-/helpers-7.23.8.tgz",
+ "integrity": "sha512-KDqYz4PiOWvDFrdHLPhKtCThtIcKVy6avWD2oG4GEvyQ+XDZwHD4YQd+H2vNMnq2rkdxsDkU82T+Vk8U/WXHRQ==",
"dev": true,
"dependencies": {
"@babel/template": "^7.22.15",
- "@babel/traverse": "^7.23.2",
- "@babel/types": "^7.23.0"
+ "@babel/traverse": "^7.23.7",
+ "@babel/types": "^7.23.6"
},
"engines": {
"node": ">=6.9.0"
}
},
"node_modules/@babel/highlight": {
- "version": "7.22.20",
- "resolved": "https://registry.npmjs.org/@babel/highlight/-/highlight-7.22.20.tgz",
- "integrity": "sha512-dkdMCN3py0+ksCgYmGG8jKeGA/8Tk+gJwSYYlFGxG5lmhfKNoAy004YpLxpS1W2J8m/EK2Ew+yOs9pVRwO89mg==",
+ "version": "7.23.4",
+ "resolved": "https://registry.npmjs.org/@babel/highlight/-/highlight-7.23.4.tgz",
+ "integrity": "sha512-acGdbYSfp2WheJoJm/EBBBLh/ID8KDc64ISZ9DYtBmC8/Q204PZJLHyzeB5qMzJ5trcOkybd78M4x2KWsUq++A==",
"dev": true,
"dependencies": {
"@babel/helper-validator-identifier": "^7.22.20",
@@ -455,9 +455,9 @@
}
},
"node_modules/@babel/parser": {
- "version": "7.23.0",
- "resolved": "https://registry.npmjs.org/@babel/parser/-/parser-7.23.0.tgz",
- "integrity": "sha512-vvPKKdMemU85V9WE/l5wZEmImpCtLqbnTvqDS2U1fJ96KrxoW7KrXhNsNCblQlg8Ck4b85yxdTyelsMUgFUXiw==",
+ "version": "7.23.6",
+ "resolved": "https://registry.npmjs.org/@babel/parser/-/parser-7.23.6.tgz",
+ "integrity": "sha512-Z2uID7YJ7oNvAI20O9X0bblw7Qqs8Q2hFy0R9tAfnfLkp5MW0UH9eUvnDSnFwKZ0AvgS1ucqR4KzvVHgnke1VQ==",
"dev": true,
"bin": {
"parser": "bin/babel-parser.js"
@@ -527,9 +527,9 @@
}
},
"node_modules/@babel/plugin-syntax-jsx": {
- "version": "7.22.5",
- "resolved": "https://registry.npmjs.org/@babel/plugin-syntax-jsx/-/plugin-syntax-jsx-7.22.5.tgz",
- "integrity": "sha512-gvyP4hZrgrs/wWMaocvxZ44Hw0b3W8Pe+cMxc8V1ULQ07oh8VNbIRaoD1LRZVTvD+0nieDKjfgKg89sD7rrKrg==",
+ "version": "7.23.3",
+ "resolved": "https://registry.npmjs.org/@babel/plugin-syntax-jsx/-/plugin-syntax-jsx-7.23.3.tgz",
+ "integrity": "sha512-EB2MELswq55OHUoRZLGg/zC7QWUKfNLpE57m/S2yr1uEneIgsTgrSzXP3NXEsMkVn76OlaVVnzN+ugObuYGwhg==",
"dev": true,
"dependencies": {
"@babel/helper-plugin-utils": "^7.22.5"
@@ -629,9 +629,9 @@
}
},
"node_modules/@babel/plugin-syntax-typescript": {
- "version": "7.22.5",
- "resolved": "https://registry.npmjs.org/@babel/plugin-syntax-typescript/-/plugin-syntax-typescript-7.22.5.tgz",
- "integrity": "sha512-1mS2o03i7t1c6VzH6fdQ3OA8tcEIxwG18zIPRp+UY1Ihv6W+XZzBCVxExF9upussPXJ0xE9XRHwMoNs1ep/nRQ==",
+ "version": "7.23.3",
+ "resolved": "https://registry.npmjs.org/@babel/plugin-syntax-typescript/-/plugin-syntax-typescript-7.23.3.tgz",
+ "integrity": "sha512-9EiNjVJOMwCO+43TqoTrgQ8jMwcAd0sWyXi9RPfIsLTj4R2MADDDQXELhffaUx/uJv2AYcxBgPwH6j4TIA4ytQ==",
"dev": true,
"dependencies": {
"@babel/helper-plugin-utils": "^7.22.5"
@@ -658,20 +658,20 @@
}
},
"node_modules/@babel/traverse": {
- "version": "7.23.2",
- "resolved": "https://registry.npmjs.org/@babel/traverse/-/traverse-7.23.2.tgz",
- "integrity": "sha512-azpe59SQ48qG6nu2CzcMLbxUudtN+dOM9kDbUqGq3HXUJRlo7i8fvPoxQUzYgLZ4cMVmuZgm8vvBpNeRhd6XSw==",
+ "version": "7.23.7",
+ "resolved": "https://registry.npmjs.org/@babel/traverse/-/traverse-7.23.7.tgz",
+ "integrity": "sha512-tY3mM8rH9jM0YHFGyfC0/xf+SB5eKUu7HPj7/k3fpi9dAlsMc5YbQvDi0Sh2QTPXqMhyaAtzAr807TIyfQrmyg==",
"dev": true,
"dependencies": {
- "@babel/code-frame": "^7.22.13",
- "@babel/generator": "^7.23.0",
+ "@babel/code-frame": "^7.23.5",
+ "@babel/generator": "^7.23.6",
"@babel/helper-environment-visitor": "^7.22.20",
"@babel/helper-function-name": "^7.23.0",
"@babel/helper-hoist-variables": "^7.22.5",
"@babel/helper-split-export-declaration": "^7.22.6",
- "@babel/parser": "^7.23.0",
- "@babel/types": "^7.23.0",
- "debug": "^4.1.0",
+ "@babel/parser": "^7.23.6",
+ "@babel/types": "^7.23.6",
+ "debug": "^4.3.1",
"globals": "^11.1.0"
},
"engines": {
@@ -688,12 +688,12 @@
}
},
"node_modules/@babel/types": {
- "version": "7.23.0",
- "resolved": "https://registry.npmjs.org/@babel/types/-/types-7.23.0.tgz",
- "integrity": "sha512-0oIyUfKoI3mSqMvsxBdclDwxXKXAUA8v/apZbc+iSyARYou1o8ZGDxbUYyLFoW2arqS2jDGqJuZvv1d/io1axg==",
+ "version": "7.23.6",
+ "resolved": "https://registry.npmjs.org/@babel/types/-/types-7.23.6.tgz",
+ "integrity": "sha512-+uarb83brBzPKN38NX1MkB6vb6+mwvR6amUulqAE7ccQw1pEl+bCia9TbdG1lsnFP7lZySvUn37CHyXQdfTwzg==",
"dev": true,
"dependencies": {
- "@babel/helper-string-parser": "^7.22.5",
+ "@babel/helper-string-parser": "^7.23.4",
"@babel/helper-validator-identifier": "^7.22.20",
"to-fast-properties": "^2.0.0"
},
@@ -723,18 +723,18 @@
}
},
"node_modules/@eslint-community/regexpp": {
- "version": "4.9.1",
- "resolved": "https://registry.npmjs.org/@eslint-community/regexpp/-/regexpp-4.9.1.tgz",
- "integrity": "sha512-Y27x+MBLjXa+0JWDhykM3+JE+il3kHKAEqabfEWq3SDhZjLYb6/BHL/JKFnH3fe207JaXkyDo685Oc2Glt6ifA==",
+ "version": "4.10.0",
+ "resolved": "https://registry.npmjs.org/@eslint-community/regexpp/-/regexpp-4.10.0.tgz",
+ "integrity": "sha512-Cu96Sd2By9mCNTx2iyKOmq10v22jUVQv0lQnlGNy16oE9589yE+QADPbrMGCkA51cKZSg3Pu/aTJVTGfL/qjUA==",
"dev": true,
"engines": {
"node": "^12.0.0 || ^14.0.0 || >=16.0.0"
}
},
"node_modules/@eslint/eslintrc": {
- "version": "2.1.2",
- "resolved": "https://registry.npmjs.org/@eslint/eslintrc/-/eslintrc-2.1.2.tgz",
- "integrity": "sha512-+wvgpDsrB1YqAMdEUCcnTlpfVBH7Vqn6A/NT3D8WVXFIaKMlErPIZT3oCIAVCOtarRpMtelZLqJeU3t7WY6X6g==",
+ "version": "2.1.4",
+ "resolved": "https://registry.npmjs.org/@eslint/eslintrc/-/eslintrc-2.1.4.tgz",
+ "integrity": "sha512-269Z39MS6wVJtsoUl10L60WdkhJVdPG24Q4eZTH3nnF6lpvSShEK3wQjDX9JRWAUPvPh7COouPpU9IrqaZFvtQ==",
"dev": true,
"dependencies": {
"ajv": "^6.12.4",
@@ -755,22 +755,22 @@
}
},
"node_modules/@eslint/js": {
- "version": "8.51.0",
- "resolved": "https://registry.npmjs.org/@eslint/js/-/js-8.51.0.tgz",
- "integrity": "sha512-HxjQ8Qn+4SI3/AFv6sOrDB+g6PpUTDwSJiQqOrnneEk8L71161srI9gjzzZvYVbzHiVg/BvcH95+cK/zfIt4pg==",
+ "version": "8.56.0",
+ "resolved": "https://registry.npmjs.org/@eslint/js/-/js-8.56.0.tgz",
+ "integrity": "sha512-gMsVel9D7f2HLkBma9VbtzZRehRogVRfbr++f06nL2vnCGCNlzOD+/MUov/F4p8myyAHspEhVobgjpX64q5m6A==",
"dev": true,
"engines": {
"node": "^12.22.0 || ^14.17.0 || >=16.0.0"
}
},
"node_modules/@humanwhocodes/config-array": {
- "version": "0.11.12",
- "resolved": "https://registry.npmjs.org/@humanwhocodes/config-array/-/config-array-0.11.12.tgz",
- "integrity": "sha512-NlGesA1usRNn6ctHCZ21M4/dKPgW9Nn1FypRdIKKgZOKzkVV4T1FlK5mBiLhHBCDmEbdQG0idrcXlbZfksJ+RA==",
+ "version": "0.11.14",
+ "resolved": "https://registry.npmjs.org/@humanwhocodes/config-array/-/config-array-0.11.14.tgz",
+ "integrity": "sha512-3T8LkOmg45BV5FICb15QQMsyUSWrQ8AygVfC7ZG32zOalnqrilm018ZVCw0eapXux8FtA33q8PSRSstjee3jSg==",
"dev": true,
"dependencies": {
- "@humanwhocodes/object-schema": "^2.0.0",
- "debug": "^4.1.1",
+ "@humanwhocodes/object-schema": "^2.0.2",
+ "debug": "^4.3.1",
"minimatch": "^3.0.5"
},
"engines": {
@@ -791,9 +791,9 @@
}
},
"node_modules/@humanwhocodes/object-schema": {
- "version": "2.0.0",
- "resolved": "https://registry.npmjs.org/@humanwhocodes/object-schema/-/object-schema-2.0.0.tgz",
- "integrity": "sha512-9S9QrXY2K0L4AGDcSgTi9vgiCcG8VcBv4Mp7/1hDPYoswIy6Z6KO5blYto82BT8M0MZNRWmCFLpCs3HlpYGGdw==",
+ "version": "2.0.2",
+ "resolved": "https://registry.npmjs.org/@humanwhocodes/object-schema/-/object-schema-2.0.2.tgz",
+ "integrity": "sha512-6EwiSjwWYP7pTckG6I5eyFANjPhmPjUX9JRLUSfNPC7FX7zK9gyZAfUEaECL6ALTpGX5AjnBq3C9XmVWPitNpw==",
"dev": true
},
"node_modules/@istanbuljs/load-nyc-config": {
@@ -1255,9 +1255,9 @@
}
},
"node_modules/@ldapjs/controls": {
- "version": "2.0.0",
- "resolved": "https://registry.npmjs.org/@ldapjs/controls/-/controls-2.0.0.tgz",
- "integrity": "sha512-NpFmdIc2q83tYRGR2a3NDulKgU1e4YOgqjQmmMezCoN4Xz0tju4yB4eibQNC+Zg8YRW06KPwFPKbebDaCqFF0w==",
+ "version": "2.1.0",
+ "resolved": "https://registry.npmjs.org/@ldapjs/controls/-/controls-2.1.0.tgz",
+ "integrity": "sha512-2pFdD1yRC9V9hXfAWvCCO2RRWK9OdIEcJIos/9cCVP9O4k72BY1bLDQQ4KpUoJnl4y/JoD4iFgM+YWT3IfITWw==",
"dependencies": {
"@ldapjs/asn1": "^1.2.0",
"@ldapjs/protocol": "^1.2.1"
@@ -1288,17 +1288,17 @@
}
},
"node_modules/@ldapjs/messages": {
- "version": "1.2.1",
- "resolved": "https://registry.npmjs.org/@ldapjs/messages/-/messages-1.2.1.tgz",
- "integrity": "sha512-QPeDcwEJmYou6QxPZqr2VibJlrZkb+qSjwxmFJgfss2Hz9wTncgs27CDloD5vOQlE65fUnhEKlzuzMi1a4oxUQ==",
+ "version": "1.3.0",
+ "resolved": "https://registry.npmjs.org/@ldapjs/messages/-/messages-1.3.0.tgz",
+ "integrity": "sha512-K7xZpXJ21bj92jS35wtRbdcNrwmxAtPwy4myeh9duy/eR3xQKvikVycbdWVzkYEAVE5Ce520VXNOwCHjomjCZw==",
"dependencies": {
- "@ldapjs/asn1": "2.0.0",
- "@ldapjs/attribute": "1.0.0",
- "@ldapjs/change": "1.0.0",
- "@ldapjs/controls": "2.0.0",
+ "@ldapjs/asn1": "^2.0.0",
+ "@ldapjs/attribute": "^1.0.0",
+ "@ldapjs/change": "^1.0.0",
+ "@ldapjs/controls": "^2.1.0",
"@ldapjs/dn": "^1.1.0",
"@ldapjs/filter": "^2.1.1",
- "@ldapjs/protocol": "1.2.1",
+ "@ldapjs/protocol": "^1.2.1",
"process-warning": "^2.2.0"
}
},
@@ -1367,9 +1367,9 @@
}
},
"node_modules/@types/babel__core": {
- "version": "7.20.3",
- "resolved": "https://registry.npmjs.org/@types/babel__core/-/babel__core-7.20.3.tgz",
- "integrity": "sha512-54fjTSeSHwfan8AyHWrKbfBWiEUrNTZsUwPTDSNaaP1QDQIZbeNUg3a59E9D+375MzUw/x1vx2/0F5LBz+AeYA==",
+ "version": "7.20.5",
+ "resolved": "https://registry.npmjs.org/@types/babel__core/-/babel__core-7.20.5.tgz",
+ "integrity": "sha512-qoQprZvz5wQFJwMDqeseRXWv3rqMvhgpbXFfVyWhbx9X47POIA6i/+dXefEmZKoAgOaTdaIgNSMqMIU61yRyzA==",
"dev": true,
"dependencies": {
"@babel/parser": "^7.20.7",
@@ -1380,18 +1380,18 @@
}
},
"node_modules/@types/babel__generator": {
- "version": "7.6.6",
- "resolved": "https://registry.npmjs.org/@types/babel__generator/-/babel__generator-7.6.6.tgz",
- "integrity": "sha512-66BXMKb/sUWbMdBNdMvajU7i/44RkrA3z/Yt1c7R5xejt8qh84iU54yUWCtm0QwGJlDcf/gg4zd/x4mpLAlb/w==",
+ "version": "7.6.8",
+ "resolved": "https://registry.npmjs.org/@types/babel__generator/-/babel__generator-7.6.8.tgz",
+ "integrity": "sha512-ASsj+tpEDsEiFr1arWrlN6V3mdfjRMZt6LtK/Vp/kreFLnr5QH5+DhvD5nINYZXzwJvXeGq+05iUXcAzVrqWtw==",
"dev": true,
"dependencies": {
"@babel/types": "^7.0.0"
}
},
"node_modules/@types/babel__template": {
- "version": "7.4.3",
- "resolved": "https://registry.npmjs.org/@types/babel__template/-/babel__template-7.4.3.tgz",
- "integrity": "sha512-ciwyCLeuRfxboZ4isgdNZi/tkt06m8Tw6uGbBSBgWrnnZGNXiEyM27xc/PjXGQLqlZ6ylbgHMnm7ccF9tCkOeQ==",
+ "version": "7.4.4",
+ "resolved": "https://registry.npmjs.org/@types/babel__template/-/babel__template-7.4.4.tgz",
+ "integrity": "sha512-h/NUaSyG5EyxBIp8YRxo4RMe2/qQgvyowRwVMzhYhBCONbW8PUsg4lkFMrhgZhUe5z3L3MiLDuvyJ/CaPa2A8A==",
"dev": true,
"dependencies": {
"@babel/parser": "^7.1.0",
@@ -1399,51 +1399,51 @@
}
},
"node_modules/@types/babel__traverse": {
- "version": "7.20.3",
- "resolved": "https://registry.npmjs.org/@types/babel__traverse/-/babel__traverse-7.20.3.tgz",
- "integrity": "sha512-Lsh766rGEFbaxMIDH7Qa+Yha8cMVI3qAK6CHt3OR0YfxOIn5Z54iHiyDRycHrBqeIiqGa20Kpsv1cavfBKkRSw==",
+ "version": "7.20.5",
+ "resolved": "https://registry.npmjs.org/@types/babel__traverse/-/babel__traverse-7.20.5.tgz",
+ "integrity": "sha512-WXCyOcRtH37HAUkpXhUduaxdm82b4GSlyTqajXviN4EfiuPgNYR109xMCKvpl6zPIpua0DGlMEDCq+g8EdoheQ==",
"dev": true,
"dependencies": {
"@babel/types": "^7.20.7"
}
},
"node_modules/@types/graceful-fs": {
- "version": "4.1.8",
- "resolved": "https://registry.npmjs.org/@types/graceful-fs/-/graceful-fs-4.1.8.tgz",
- "integrity": "sha512-NhRH7YzWq8WiNKVavKPBmtLYZHxNY19Hh+az28O/phfp68CF45pMFud+ZzJ8ewnxnC5smIdF3dqFeiSUQ5I+pw==",
+ "version": "4.1.9",
+ "resolved": "https://registry.npmjs.org/@types/graceful-fs/-/graceful-fs-4.1.9.tgz",
+ "integrity": "sha512-olP3sd1qOEe5dXTSaFvQG+02VdRXcdytWLAZsAq1PecU8uqQAhkrnbli7DagjtXKW/Bl7YJbUsa8MPcuc8LHEQ==",
"dev": true,
"dependencies": {
"@types/node": "*"
}
},
"node_modules/@types/istanbul-lib-coverage": {
- "version": "2.0.5",
- "resolved": "https://registry.npmjs.org/@types/istanbul-lib-coverage/-/istanbul-lib-coverage-2.0.5.tgz",
- "integrity": "sha512-zONci81DZYCZjiLe0r6equvZut0b+dBRPBN5kBDjsONnutYNtJMoWQ9uR2RkL1gLG9NMTzvf+29e5RFfPbeKhQ==",
+ "version": "2.0.6",
+ "resolved": "https://registry.npmjs.org/@types/istanbul-lib-coverage/-/istanbul-lib-coverage-2.0.6.tgz",
+ "integrity": "sha512-2QF/t/auWm0lsy8XtKVPG19v3sSOQlJe/YHZgfjb/KBBHOGSV+J2q/S671rcq9uTBrLAXmZpqJiaQbMT+zNU1w==",
"dev": true
},
"node_modules/@types/istanbul-lib-report": {
- "version": "3.0.2",
- "resolved": "https://registry.npmjs.org/@types/istanbul-lib-report/-/istanbul-lib-report-3.0.2.tgz",
- "integrity": "sha512-8toY6FgdltSdONav1XtUHl4LN1yTmLza+EuDazb/fEmRNCwjyqNVIQWs2IfC74IqjHkREs/nQ2FWq5kZU9IC0w==",
+ "version": "3.0.3",
+ "resolved": "https://registry.npmjs.org/@types/istanbul-lib-report/-/istanbul-lib-report-3.0.3.tgz",
+ "integrity": "sha512-NQn7AHQnk/RSLOxrBbGyJM/aVQ+pjj5HCgasFxc0K/KhoATfQ/47AyUl15I2yBUpihjmas+a+VJBOqecrFH+uA==",
"dev": true,
"dependencies": {
"@types/istanbul-lib-coverage": "*"
}
},
"node_modules/@types/istanbul-reports": {
- "version": "3.0.3",
- "resolved": "https://registry.npmjs.org/@types/istanbul-reports/-/istanbul-reports-3.0.3.tgz",
- "integrity": "sha512-1nESsePMBlf0RPRffLZi5ujYh7IH1BWL4y9pr+Bn3cJBdxz+RTP8bUFljLz9HvzhhOSWKdyBZ4DIivdL6rvgZg==",
+ "version": "3.0.4",
+ "resolved": "https://registry.npmjs.org/@types/istanbul-reports/-/istanbul-reports-3.0.4.tgz",
+ "integrity": "sha512-pk2B1NWalF9toCRu6gjBzR69syFjP4Od8WRAX+0mmf9lAjCRicLOWc+ZrxZHx/0XRjotgkF9t6iaMJ+aXcOdZQ==",
"dev": true,
"dependencies": {
"@types/istanbul-lib-report": "*"
}
},
"node_modules/@types/json-schema": {
- "version": "7.0.14",
- "resolved": "https://registry.npmjs.org/@types/json-schema/-/json-schema-7.0.14.tgz",
- "integrity": "sha512-U3PUjAudAdJBeC2pgN8uTIKgxrb4nlDF3SF0++EldXQvQBGkpFZMSnwQiIoDU77tv45VgNkl/L4ouD+rEomujw==",
+ "version": "7.0.15",
+ "resolved": "https://registry.npmjs.org/@types/json-schema/-/json-schema-7.0.15.tgz",
+ "integrity": "sha512-5+fP8P8MFNC+AyZCDxrB2pkZFPGzqQWUzpSeuuVLvm8VMcorNYavBqoFcxK8bQz4Qsbn4oUEEem4wDLfcysGHA==",
"dev": true
},
"node_modules/@types/json5": {
@@ -1453,39 +1453,39 @@
"dev": true
},
"node_modules/@types/node": {
- "version": "20.8.7",
- "resolved": "https://registry.npmjs.org/@types/node/-/node-20.8.7.tgz",
- "integrity": "sha512-21TKHHh3eUHIi2MloeptJWALuCu5H7HQTdTrWIFReA8ad+aggoX+lRes3ex7/FtpC+sVUpFMQ+QTfYr74mruiQ==",
+ "version": "20.11.0",
+ "resolved": "https://registry.npmjs.org/@types/node/-/node-20.11.0.tgz",
+ "integrity": "sha512-o9bjXmDNcF7GbM4CNQpmi+TutCgap/K3w1JyKgxAjqx41zp9qlIAVFi0IhCNsJcXolEqLWhbFbEeL0PvYm4pcQ==",
"dev": true,
"dependencies": {
- "undici-types": "~5.25.1"
+ "undici-types": "~5.26.4"
}
},
"node_modules/@types/semver": {
- "version": "7.5.4",
- "resolved": "https://registry.npmjs.org/@types/semver/-/semver-7.5.4.tgz",
- "integrity": "sha512-MMzuxN3GdFwskAnb6fz0orFvhfqi752yjaXylr0Rp4oDg5H0Zn1IuyRhDVvYOwAXoJirx2xuS16I3WjxnAIHiQ==",
+ "version": "7.5.6",
+ "resolved": "https://registry.npmjs.org/@types/semver/-/semver-7.5.6.tgz",
+ "integrity": "sha512-dn1l8LaMea/IjDoHNd9J52uBbInB796CDffS6VdIxvqYCPSG0V0DzHp76GpaWnlhg88uYyPbXCDIowa86ybd5A==",
"dev": true
},
"node_modules/@types/stack-utils": {
- "version": "2.0.2",
- "resolved": "https://registry.npmjs.org/@types/stack-utils/-/stack-utils-2.0.2.tgz",
- "integrity": "sha512-g7CK9nHdwjK2n0ymT2CW698FuWJRIx+RP6embAzZ2Qi8/ilIrA1Imt2LVSeHUzKvpoi7BhmmQcXz95eS0f2JXw==",
+ "version": "2.0.3",
+ "resolved": "https://registry.npmjs.org/@types/stack-utils/-/stack-utils-2.0.3.tgz",
+ "integrity": "sha512-9aEbYZ3TbYMznPdcdr3SmIrLXwC/AKZXQeCf9Pgao5CKb8CyHuEX5jzWPTkvregvhRJHcpRO6BFoGW9ycaOkYw==",
"dev": true
},
"node_modules/@types/yargs": {
- "version": "17.0.29",
- "resolved": "https://registry.npmjs.org/@types/yargs/-/yargs-17.0.29.tgz",
- "integrity": "sha512-nacjqA3ee9zRF/++a3FUY1suHTFKZeHba2n8WeDw9cCVdmzmHpIxyzOJBcpHvvEmS8E9KqWlSnWHUkOrkhWcvA==",
+ "version": "17.0.32",
+ "resolved": "https://registry.npmjs.org/@types/yargs/-/yargs-17.0.32.tgz",
+ "integrity": "sha512-xQ67Yc/laOG5uMfX/093MRlGGCIBzZMarVa+gfNKJxWAIgykYpVGkBdbqEzGDDfCrVUj6Hiff4mTZ5BA6TmAog==",
"dev": true,
"dependencies": {
"@types/yargs-parser": "*"
}
},
"node_modules/@types/yargs-parser": {
- "version": "21.0.2",
- "resolved": "https://registry.npmjs.org/@types/yargs-parser/-/yargs-parser-21.0.2.tgz",
- "integrity": "sha512-5qcvofLPbfjmBfKaLfj/+f+Sbd6pN4zl7w7VSVI5uz7m9QZTuB2aZAa2uo1wHFBNN2x6g/SoTkXmd8mQnQF2Cw==",
+ "version": "21.0.3",
+ "resolved": "https://registry.npmjs.org/@types/yargs-parser/-/yargs-parser-21.0.3.tgz",
+ "integrity": "sha512-I4q9QU9MQv4oEOz4tAHJtNz1cwuLxn2F3xcc2iV5WdqLPpUnj30aUuxt1mAxYTG+oe8CZMV/+6rU4S4gRDzqtQ==",
"dev": true
},
"node_modules/@typescript-eslint/scope-manager": {
@@ -1676,15 +1676,21 @@
"url": "https://opencollective.com/typescript-eslint"
}
},
+ "node_modules/@ungap/structured-clone": {
+ "version": "1.2.0",
+ "resolved": "https://registry.npmjs.org/@ungap/structured-clone/-/structured-clone-1.2.0.tgz",
+ "integrity": "sha512-zuVdFrMJiuCDQUMCzQaD6KL28MjnqqN8XnAqiEq9PNm/hCPTSGfrXCOfwj1ow4LFb/tNymJPwsNbVePc1xFqrQ==",
+ "dev": true
+ },
"node_modules/abstract-logging": {
"version": "2.0.1",
"resolved": "https://registry.npmjs.org/abstract-logging/-/abstract-logging-2.0.1.tgz",
"integrity": "sha512-2BjRTZxTPvheOvGbBslFSYOUkr+SjPtOnrLP33f+VIWLzezQpZcqVg7ja3L4dBXmzzgwT+a029jRx5PCi3JuiA=="
},
"node_modules/acorn": {
- "version": "8.10.0",
- "resolved": "https://registry.npmjs.org/acorn/-/acorn-8.10.0.tgz",
- "integrity": "sha512-F0SAmZ8iUtS//m8DmCTA0jlh6TDKkHQyK6xc6V4KDTyZKA9dnvX9/3sRTVQrWm79glUAZbnmmNcdYwUIHWVybw==",
+ "version": "8.11.3",
+ "resolved": "https://registry.npmjs.org/acorn/-/acorn-8.11.3.tgz",
+ "integrity": "sha512-Y9rRfJG5jcKOE0CLisYbojUjIrIEE7AGMzA/Sm4BslANhbS+cDMpgBdcPT91oJ7OuJ9hYJBx59RjbhxVnrF8Xg==",
"dev": true,
"bin": {
"acorn": "bin/acorn"
@@ -1942,11 +1948,11 @@
}
},
"node_modules/axios": {
- "version": "1.6.0",
- "resolved": "https://registry.npmjs.org/axios/-/axios-1.6.0.tgz",
- "integrity": "sha512-EZ1DYihju9pwVB+jg67ogm+Tmqc6JmhamRN6I4Zt8DfZu5lbcQGw3ozH9lFejSJgs/ibaef3A9PMXPLeefFGJg==",
+ "version": "1.6.5",
+ "resolved": "https://registry.npmjs.org/axios/-/axios-1.6.5.tgz",
+ "integrity": "sha512-Ii012v05KEVuUoFWmMW/UQv9aRIc3ZwkWDcM+h5Il8izZCtRVpDUfwpoFf7eOtajT3QiGR4yDUx7lPqHJULgbg==",
"dependencies": {
- "follow-redirects": "^1.15.0",
+ "follow-redirects": "^1.15.4",
"form-data": "^4.0.0",
"proxy-from-env": "^1.1.0"
}
@@ -2098,9 +2104,9 @@
}
},
"node_modules/browserslist": {
- "version": "4.22.1",
- "resolved": "https://registry.npmjs.org/browserslist/-/browserslist-4.22.1.tgz",
- "integrity": "sha512-FEVc202+2iuClEhZhrWy6ZiAcRLvNMyYcxZ8raemul1DYVOVdFsbqckWLdsixQZCpJlwe77Z3UTalE7jsjnKfQ==",
+ "version": "4.22.2",
+ "resolved": "https://registry.npmjs.org/browserslist/-/browserslist-4.22.2.tgz",
+ "integrity": "sha512-0UgcrvQmBDvZHFGdYUehrCNIazki7/lUP3kkoi/r3YB2amZbFM9J43ZRkJTXBUZK4gmx56+Sqk9+Vs9mwZx9+A==",
"dev": true,
"funding": [
{
@@ -2117,9 +2123,9 @@
}
],
"dependencies": {
- "caniuse-lite": "^1.0.30001541",
- "electron-to-chromium": "^1.4.535",
- "node-releases": "^2.0.13",
+ "caniuse-lite": "^1.0.30001565",
+ "electron-to-chromium": "^1.4.601",
+ "node-releases": "^2.0.14",
"update-browserslist-db": "^1.0.13"
},
"bin": {
@@ -2149,6 +2155,18 @@
"integrity": "sha512-E+XQCRwSbaaiChtv6k6Dwgc+bx+Bs6vuKJHHl5kox/BaKbhiXzqQOwK4cO22yElGp2OCmjwVhT3HmxgyPGnJfQ==",
"dev": true
},
+ "node_modules/builtin-modules": {
+ "version": "3.3.0",
+ "resolved": "https://registry.npmjs.org/builtin-modules/-/builtin-modules-3.3.0.tgz",
+ "integrity": "sha512-zhaCDicdLuWN5UbN5IMnFqNMhNfo919sH85y2/ea+5Yg9TsTkeZxpL+JLbp6cgYFS4sRLp3YV4S6yDuqVWHYOw==",
+ "dev": true,
+ "engines": {
+ "node": ">=6"
+ },
+ "funding": {
+ "url": "https://github.com/sponsors/sindresorhus"
+ }
+ },
"node_modules/builtins": {
"version": "5.0.1",
"resolved": "https://registry.npmjs.org/builtins/-/builtins-5.0.1.tgz",
@@ -2224,9 +2242,9 @@
}
},
"node_modules/caniuse-lite": {
- "version": "1.0.30001551",
- "resolved": "https://registry.npmjs.org/caniuse-lite/-/caniuse-lite-1.0.30001551.tgz",
- "integrity": "sha512-vtBAez47BoGMMzlbYhfXrMV1kvRF2WP/lqiMuDu1Sb4EE4LKEgjopFDSRtZfdVnslNRpOqV/woE+Xgrwj6VQlg==",
+ "version": "1.0.30001576",
+ "resolved": "https://registry.npmjs.org/caniuse-lite/-/caniuse-lite-1.0.30001576.tgz",
+ "integrity": "sha512-ff5BdakGe2P3SQsMsiqmt1Lc8221NR1VzHj5jXN5vBny9A6fpze94HiVV/n7XRosOlsShJcvMv5mdnpjOGCEgg==",
"dev": true,
"funding": [
{
@@ -2551,9 +2569,9 @@
}
},
"node_modules/electron-to-chromium": {
- "version": "1.4.561",
- "resolved": "https://registry.npmjs.org/electron-to-chromium/-/electron-to-chromium-1.4.561.tgz",
- "integrity": "sha512-eS5t4ulWOBfVHdq9SW2dxEaFarj1lPjvJ8PaYMOjY0DecBaj/t4ARziL2IPpDr4atyWwjLFGQ2vo/VCgQFezVQ==",
+ "version": "1.4.628",
+ "resolved": "https://registry.npmjs.org/electron-to-chromium/-/electron-to-chromium-1.4.628.tgz",
+ "integrity": "sha512-2k7t5PHvLsufpP6Zwk0nof62yLOsCf032wZx7/q0mv8gwlXjhcxI3lz6f0jBr0GrnWKcm3burXzI3t5IrcdUxw==",
"dev": true
},
"node_modules/emittery": {
@@ -2584,26 +2602,26 @@
}
},
"node_modules/es-abstract": {
- "version": "1.22.2",
- "resolved": "https://registry.npmjs.org/es-abstract/-/es-abstract-1.22.2.tgz",
- "integrity": "sha512-YoxfFcDmhjOgWPWsV13+2RNjq1F6UQnfs+8TftwNqtzlmFzEXvlUwdrNrYeaizfjQzRMxkZ6ElWMOJIFKdVqwA==",
+ "version": "1.22.3",
+ "resolved": "https://registry.npmjs.org/es-abstract/-/es-abstract-1.22.3.tgz",
+ "integrity": "sha512-eiiY8HQeYfYH2Con2berK+To6GrK2RxbPawDkGq4UiCQQfZHb6wX9qQqkbpPqaxQFcl8d9QzZqo0tGE0VcrdwA==",
"dev": true,
"dependencies": {
"array-buffer-byte-length": "^1.0.0",
"arraybuffer.prototype.slice": "^1.0.2",
"available-typed-arrays": "^1.0.5",
- "call-bind": "^1.0.2",
+ "call-bind": "^1.0.5",
"es-set-tostringtag": "^2.0.1",
"es-to-primitive": "^1.2.1",
"function.prototype.name": "^1.1.6",
- "get-intrinsic": "^1.2.1",
+ "get-intrinsic": "^1.2.2",
"get-symbol-description": "^1.0.0",
"globalthis": "^1.0.3",
"gopd": "^1.0.1",
- "has": "^1.0.3",
"has-property-descriptors": "^1.0.0",
"has-proto": "^1.0.1",
"has-symbols": "^1.0.3",
+ "hasown": "^2.0.0",
"internal-slot": "^1.0.5",
"is-array-buffer": "^3.0.2",
"is-callable": "^1.2.7",
@@ -2613,7 +2631,7 @@
"is-string": "^1.0.7",
"is-typed-array": "^1.1.12",
"is-weakref": "^1.0.2",
- "object-inspect": "^1.12.3",
+ "object-inspect": "^1.13.1",
"object-keys": "^1.1.1",
"object.assign": "^4.1.4",
"regexp.prototype.flags": "^1.5.1",
@@ -2627,7 +2645,7 @@
"typed-array-byte-offset": "^1.0.0",
"typed-array-length": "^1.0.4",
"unbox-primitive": "^1.0.2",
- "which-typed-array": "^1.1.11"
+ "which-typed-array": "^1.1.13"
},
"engines": {
"node": ">= 0.4"
@@ -2637,26 +2655,26 @@
}
},
"node_modules/es-set-tostringtag": {
- "version": "2.0.1",
- "resolved": "https://registry.npmjs.org/es-set-tostringtag/-/es-set-tostringtag-2.0.1.tgz",
- "integrity": "sha512-g3OMbtlwY3QewlqAiMLI47KywjWZoEytKr8pf6iTC8uJq5bIAH52Z9pnQ8pVL6whrCto53JZDuUIsifGeLorTg==",
+ "version": "2.0.2",
+ "resolved": "https://registry.npmjs.org/es-set-tostringtag/-/es-set-tostringtag-2.0.2.tgz",
+ "integrity": "sha512-BuDyupZt65P9D2D2vA/zqcI3G5xRsklm5N3xCwuiy+/vKy8i0ifdsQP1sLgO4tZDSCaQUSnmC48khknGMV3D2Q==",
"dev": true,
"dependencies": {
- "get-intrinsic": "^1.1.3",
- "has": "^1.0.3",
- "has-tostringtag": "^1.0.0"
+ "get-intrinsic": "^1.2.2",
+ "has-tostringtag": "^1.0.0",
+ "hasown": "^2.0.0"
},
"engines": {
"node": ">= 0.4"
}
},
"node_modules/es-shim-unscopables": {
- "version": "1.0.0",
- "resolved": "https://registry.npmjs.org/es-shim-unscopables/-/es-shim-unscopables-1.0.0.tgz",
- "integrity": "sha512-Jm6GPcCdC30eMLbZ2x8z2WuRwAws3zTBBKuusffYVUrNj/GVSUAZ+xKMaUpfNDR5IbyNA5LJbaecoUVbmUcB1w==",
+ "version": "1.0.2",
+ "resolved": "https://registry.npmjs.org/es-shim-unscopables/-/es-shim-unscopables-1.0.2.tgz",
+ "integrity": "sha512-J3yBRXCzDu4ULnQwxyToo/OjdMx6akgVC7K6few0a7F/0wLtmKKN7I73AH5T2836UuXRqN7Qg+IIUw/+YJksRw==",
"dev": true,
"dependencies": {
- "has": "^1.0.3"
+ "hasown": "^2.0.0"
}
},
"node_modules/es-to-primitive": {
@@ -2698,18 +2716,19 @@
}
},
"node_modules/eslint": {
- "version": "8.51.0",
- "resolved": "https://registry.npmjs.org/eslint/-/eslint-8.51.0.tgz",
- "integrity": "sha512-2WuxRZBrlwnXi+/vFSJyjMqrNjtJqiasMzehF0shoLaW7DzS3/9Yvrmq5JiT66+pNjiX4UBnLDiKHcWAr/OInA==",
+ "version": "8.56.0",
+ "resolved": "https://registry.npmjs.org/eslint/-/eslint-8.56.0.tgz",
+ "integrity": "sha512-Go19xM6T9puCOWntie1/P997aXxFsOi37JIHRWI514Hc6ZnaHGKY9xFhrU65RT6CcBEzZoGG1e6Nq+DT04ZtZQ==",
"dev": true,
"dependencies": {
"@eslint-community/eslint-utils": "^4.2.0",
"@eslint-community/regexpp": "^4.6.1",
- "@eslint/eslintrc": "^2.1.2",
- "@eslint/js": "8.51.0",
- "@humanwhocodes/config-array": "^0.11.11",
+ "@eslint/eslintrc": "^2.1.4",
+ "@eslint/js": "8.56.0",
+ "@humanwhocodes/config-array": "^0.11.13",
"@humanwhocodes/module-importer": "^1.0.1",
"@nodelib/fs.walk": "^1.2.8",
+ "@ungap/structured-clone": "^1.2.0",
"ajv": "^6.12.4",
"chalk": "^4.0.0",
"cross-spawn": "^7.0.2",
@@ -2751,6 +2770,18 @@
"url": "https://opencollective.com/eslint"
}
},
+ "node_modules/eslint-compat-utils": {
+ "version": "0.1.2",
+ "resolved": "https://registry.npmjs.org/eslint-compat-utils/-/eslint-compat-utils-0.1.2.tgz",
+ "integrity": "sha512-Jia4JDldWnFNIru1Ehx1H5s9/yxiRHY/TimCuUc0jNexew3cF1gI6CYZil1ociakfWO3rRqFjl1mskBblB3RYg==",
+ "dev": true,
+ "engines": {
+ "node": ">=12"
+ },
+ "peerDependencies": {
+ "eslint": ">=6.0.0"
+ }
+ },
"node_modules/eslint-config-standard": {
"version": "17.1.0",
"resolved": "https://registry.npmjs.org/eslint-config-standard/-/eslint-config-standard-17.1.0.tgz",
@@ -2846,13 +2877,14 @@
}
},
"node_modules/eslint-plugin-es-x": {
- "version": "7.2.0",
- "resolved": "https://registry.npmjs.org/eslint-plugin-es-x/-/eslint-plugin-es-x-7.2.0.tgz",
- "integrity": "sha512-9dvv5CcvNjSJPqnS5uZkqb3xmbeqRLnvXKK7iI5+oK/yTusyc46zbBZKENGsOfojm/mKfszyZb+wNqNPAPeGXA==",
+ "version": "7.5.0",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-es-x/-/eslint-plugin-es-x-7.5.0.tgz",
+ "integrity": "sha512-ODswlDSO0HJDzXU0XvgZ3lF3lS3XAZEossh15Q2UHjwrJggWeBoKqqEsLTZLXl+dh5eOAozG0zRcYtuE35oTuQ==",
"dev": true,
"dependencies": {
"@eslint-community/eslint-utils": "^4.1.2",
- "@eslint-community/regexpp": "^4.6.0"
+ "@eslint-community/regexpp": "^4.6.0",
+ "eslint-compat-utils": "^0.1.2"
},
"engines": {
"node": "^14.18.0 || >=16.0.0"
@@ -2865,28 +2897,28 @@
}
},
"node_modules/eslint-plugin-import": {
- "version": "2.28.1",
- "resolved": "https://registry.npmjs.org/eslint-plugin-import/-/eslint-plugin-import-2.28.1.tgz",
- "integrity": "sha512-9I9hFlITvOV55alzoKBI+K9q74kv0iKMeY6av5+umsNwayt59fz692daGyjR+oStBQgx6nwR9rXldDev3Clw+A==",
+ "version": "2.29.1",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-import/-/eslint-plugin-import-2.29.1.tgz",
+ "integrity": "sha512-BbPC0cuExzhiMo4Ff1BTVwHpjjv28C5R+btTOGaCRC7UEz801up0JadwkeSk5Ued6TG34uaczuVuH6qyy5YUxw==",
"dev": true,
"dependencies": {
- "array-includes": "^3.1.6",
- "array.prototype.findlastindex": "^1.2.2",
- "array.prototype.flat": "^1.3.1",
- "array.prototype.flatmap": "^1.3.1",
+ "array-includes": "^3.1.7",
+ "array.prototype.findlastindex": "^1.2.3",
+ "array.prototype.flat": "^1.3.2",
+ "array.prototype.flatmap": "^1.3.2",
"debug": "^3.2.7",
"doctrine": "^2.1.0",
- "eslint-import-resolver-node": "^0.3.7",
+ "eslint-import-resolver-node": "^0.3.9",
"eslint-module-utils": "^2.8.0",
- "has": "^1.0.3",
- "is-core-module": "^2.13.0",
+ "hasown": "^2.0.0",
+ "is-core-module": "^2.13.1",
"is-glob": "^4.0.3",
"minimatch": "^3.1.2",
- "object.fromentries": "^2.0.6",
- "object.groupby": "^1.0.0",
- "object.values": "^1.1.6",
+ "object.fromentries": "^2.0.7",
+ "object.groupby": "^1.0.1",
+ "object.values": "^1.1.7",
"semver": "^6.3.1",
- "tsconfig-paths": "^3.14.2"
+ "tsconfig-paths": "^3.15.0"
},
"engines": {
"node": ">=4"
@@ -2917,9 +2949,9 @@
}
},
"node_modules/eslint-plugin-jest": {
- "version": "27.4.2",
- "resolved": "https://registry.npmjs.org/eslint-plugin-jest/-/eslint-plugin-jest-27.4.2.tgz",
- "integrity": "sha512-3Nfvv3wbq2+PZlRTf2oaAWXWwbdBejFRBR2O8tAO67o+P8zno+QGbcDYaAXODlreXVg+9gvWhKKmG2rgfb8GEg==",
+ "version": "27.6.2",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-jest/-/eslint-plugin-jest-27.6.2.tgz",
+ "integrity": "sha512-CI1AlKrsNhYFoP48VU8BVWOi7+qHTq4bRxyUlGjeU8SfFt8abjXhjOuDzUoMp68DoXIx17KpNpIkMrl4s4ZW0g==",
"dev": true,
"dependencies": {
"@typescript-eslint/utils": "^5.10.0"
@@ -2942,16 +2974,18 @@
}
},
"node_modules/eslint-plugin-n": {
- "version": "16.2.0",
- "resolved": "https://registry.npmjs.org/eslint-plugin-n/-/eslint-plugin-n-16.2.0.tgz",
- "integrity": "sha512-AQER2jEyQOt1LG6JkGJCCIFotzmlcCZFur2wdKrp1JX2cNotC7Ae0BcD/4lLv3lUAArM9uNS8z/fsvXTd0L71g==",
+ "version": "16.6.2",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-n/-/eslint-plugin-n-16.6.2.tgz",
+ "integrity": "sha512-6TyDmZ1HXoFQXnhCTUjVFULReoBPOAjpuiKELMkeP40yffI/1ZRO+d9ug/VC6fqISo2WkuIBk3cvuRPALaWlOQ==",
"dev": true,
"dependencies": {
"@eslint-community/eslint-utils": "^4.4.0",
"builtins": "^5.0.1",
- "eslint-plugin-es-x": "^7.1.0",
+ "eslint-plugin-es-x": "^7.5.0",
"get-tsconfig": "^4.7.0",
+ "globals": "^13.24.0",
"ignore": "^5.2.4",
+ "is-builtin-module": "^3.2.1",
"is-core-module": "^2.12.1",
"minimatch": "^3.1.2",
"resolve": "^1.22.2",
@@ -3033,9 +3067,9 @@
}
},
"node_modules/eslint-plugin-security": {
- "version": "1.7.1",
- "resolved": "https://registry.npmjs.org/eslint-plugin-security/-/eslint-plugin-security-1.7.1.tgz",
- "integrity": "sha512-sMStceig8AFglhhT2LqlU5r+/fn9OwsA72O5bBuQVTssPCdQAOQzL+oMn/ZcpeUY6KcNfLJArgcrsSULNjYYdQ==",
+ "version": "2.1.0",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-security/-/eslint-plugin-security-2.1.0.tgz",
+ "integrity": "sha512-ywxclP954bf8d3gr6KOQ/AFc+PRvWuhOxtPOEtiHmVYiZr/mcgQtmSJq6+hTEXC5ylTjHnPPG+PEnzlDiWMXbQ==",
"dev": true,
"dependencies": {
"safe-regex": "^2.1.1"
@@ -3228,9 +3262,9 @@
"dev": true
},
"node_modules/fast-glob": {
- "version": "3.3.1",
- "resolved": "https://registry.npmjs.org/fast-glob/-/fast-glob-3.3.1.tgz",
- "integrity": "sha512-kNFPyjhh5cKjrUltxs+wFx+ZkbRaxxmZ+X0ZU31SOsxCEtP9VPgtq2teZw1DebupL5GmDaNQ6yKMMVcM41iqDg==",
+ "version": "3.3.2",
+ "resolved": "https://registry.npmjs.org/fast-glob/-/fast-glob-3.3.2.tgz",
+ "integrity": "sha512-oX2ruAFQwf/Orj8m737Y5adxDQO0LAB7/S5MnxCdTNDd4p6BsyIVsv9JQsATbTSq8KHRpLwIHbVlUNatxd+1Ow==",
"dev": true,
"dependencies": {
"@nodelib/fs.stat": "^2.0.2",
@@ -3268,9 +3302,9 @@
"dev": true
},
"node_modules/fastq": {
- "version": "1.15.0",
- "resolved": "https://registry.npmjs.org/fastq/-/fastq-1.15.0.tgz",
- "integrity": "sha512-wBrocU2LCXXa+lWBt8RoIRD89Fi8OdABODa/kEnyeyjS5aZO5/GNvI5sEINADqP/h8M29UHTHUb53sUu5Ihqdw==",
+ "version": "1.16.0",
+ "resolved": "https://registry.npmjs.org/fastq/-/fastq-1.16.0.tgz",
+ "integrity": "sha512-ifCoaXsDrsdkWTtiNJX5uzHDsrck5TzfKKDcuFFTIrrc/BS076qgEIfoIy1VeZqViznfKiysPYTh/QeHtnIsYA==",
"dev": true,
"dependencies": {
"reusify": "^1.0.4"
@@ -3326,9 +3360,9 @@
}
},
"node_modules/flat-cache": {
- "version": "3.1.1",
- "resolved": "https://registry.npmjs.org/flat-cache/-/flat-cache-3.1.1.tgz",
- "integrity": "sha512-/qM2b3LUIaIgviBQovTLvijfyOQXPtSRnRK26ksj2J7rzPIecePUIpJsZ4T02Qg+xiAEKIs5K8dsHEd+VaKa/Q==",
+ "version": "3.2.0",
+ "resolved": "https://registry.npmjs.org/flat-cache/-/flat-cache-3.2.0.tgz",
+ "integrity": "sha512-CYcENa+FtcUKLmhhqyctpclsq7QF38pKjZHsGNiSQF5r4FtoKDWabFDl3hzaEQMvT1LHEysw5twgLvpYYb4vbw==",
"dev": true,
"dependencies": {
"flatted": "^3.2.9",
@@ -3336,7 +3370,7 @@
"rimraf": "^3.0.2"
},
"engines": {
- "node": ">=12.0.0"
+ "node": "^10.12.0 || >=12.0.0"
}
},
"node_modules/flatted": {
@@ -3466,15 +3500,15 @@
}
},
"node_modules/get-intrinsic": {
- "version": "1.2.1",
- "resolved": "https://registry.npmjs.org/get-intrinsic/-/get-intrinsic-1.2.1.tgz",
- "integrity": "sha512-2DcsyfABl+gVHEfCOaTrWgyt+tb6MSEGmKq+kI5HwLbIYgjgmMcV8KQ41uaKz1xxUcn9tJtgFbQUEVcEbd0FYw==",
+ "version": "1.2.2",
+ "resolved": "https://registry.npmjs.org/get-intrinsic/-/get-intrinsic-1.2.2.tgz",
+ "integrity": "sha512-0gSo4ml/0j98Y3lngkFEot/zhiCeWsbYIlZ+uZOVgzLyLaUw7wxUL+nCTP0XJvJg1AXulJRI3UJi8GsbDuxdGA==",
"dev": true,
"dependencies": {
- "function-bind": "^1.1.1",
- "has": "^1.0.3",
+ "function-bind": "^1.1.2",
"has-proto": "^1.0.1",
- "has-symbols": "^1.0.3"
+ "has-symbols": "^1.0.3",
+ "hasown": "^2.0.0"
},
"funding": {
"url": "https://github.com/sponsors/ljharb"
@@ -3562,9 +3596,9 @@
}
},
"node_modules/globals": {
- "version": "13.23.0",
- "resolved": "https://registry.npmjs.org/globals/-/globals-13.23.0.tgz",
- "integrity": "sha512-XAmF0RjlrjY23MA51q3HltdlGxUpXPvg0GioKiD9X6HD28iMjo2dKC8Vqwm7lne4GNr78+RHTfliktR6ZH09wA==",
+ "version": "13.24.0",
+ "resolved": "https://registry.npmjs.org/globals/-/globals-13.24.0.tgz",
+ "integrity": "sha512-AhO5QUcj8llrbG09iWhPU2B204J1xnPeL8kQmVorSsy+Sjj1sk8gIyh6cUocGmH4L0UuhAJy+hJMRA4mgA4mFQ==",
"dev": true,
"dependencies": {
"type-fest": "^0.20.2"
@@ -3635,15 +3669,6 @@
"integrity": "sha512-EtKwoO6kxCL9WO5xipiHTZlSzBm7WLT627TqC/uVRd0HKmq8NXyebnNYxDoBi7wt8eTWrUrKXCOVaFq9x1kgag==",
"dev": true
},
- "node_modules/has": {
- "version": "1.0.4",
- "resolved": "https://registry.npmjs.org/has/-/has-1.0.4.tgz",
- "integrity": "sha512-qdSAmqLF6209RFj4VVItywPMbm3vWylknmB3nvNiUIs72xAimcM8nVYxYr7ncvZq5qzk9MKIZR8ijqD/1QuYjQ==",
- "dev": true,
- "engines": {
- "node": ">= 0.4.0"
- }
- },
"node_modules/has-bigints": {
"version": "1.0.2",
"resolved": "https://registry.npmjs.org/has-bigints/-/has-bigints-1.0.2.tgz",
@@ -3663,12 +3688,12 @@
}
},
"node_modules/has-property-descriptors": {
- "version": "1.0.0",
- "resolved": "https://registry.npmjs.org/has-property-descriptors/-/has-property-descriptors-1.0.0.tgz",
- "integrity": "sha512-62DVLZGoiEBDHQyqG4w9xCuZ7eJEwNmJRWw2VY84Oedb7WFcA27fiEVe8oUQx9hAUJ4ekurquucTGwsyO1XGdQ==",
+ "version": "1.0.1",
+ "resolved": "https://registry.npmjs.org/has-property-descriptors/-/has-property-descriptors-1.0.1.tgz",
+ "integrity": "sha512-VsX8eaIewvas0xnvinAe9bw4WfIeODpGYikiWYLH+dma0Jw6KHYqWiWfhQlgOVK8D6PvjubK5Uc4P0iIhIcNVg==",
"dev": true,
"dependencies": {
- "get-intrinsic": "^1.1.1"
+ "get-intrinsic": "^1.2.2"
},
"funding": {
"url": "https://github.com/sponsors/ljharb"
@@ -3718,6 +3743,18 @@
"resolved": "https://registry.npmjs.org/hashcode/-/hashcode-1.0.3.tgz",
"integrity": "sha512-tfCzdiaz69Ii8eIdtYSCEnU0jw5RrYRd0u3sHRvs5Oqu/bQPk+aonT5jgRUT2MIuphjSvjB5lmixhHl7+X4ruw=="
},
+ "node_modules/hasown": {
+ "version": "2.0.0",
+ "resolved": "https://registry.npmjs.org/hasown/-/hasown-2.0.0.tgz",
+ "integrity": "sha512-vUptKVTpIJhcczKBbgnS+RtcuYMB8+oNzPK2/Hp3hanz8JmpATdmmgLgSaadVREkDm+e2giHwY3ZRkyjSIDDFA==",
+ "dev": true,
+ "dependencies": {
+ "function-bind": "^1.1.2"
+ },
+ "engines": {
+ "node": ">= 0.4"
+ }
+ },
"node_modules/html-escaper": {
"version": "2.0.2",
"resolved": "https://registry.npmjs.org/html-escaper/-/html-escaper-2.0.2.tgz",
@@ -3746,9 +3783,9 @@
}
},
"node_modules/ignore": {
- "version": "5.2.4",
- "resolved": "https://registry.npmjs.org/ignore/-/ignore-5.2.4.tgz",
- "integrity": "sha512-MAb38BcSbH0eHNBxn7ql2NH/kX33OkB3lZ1BNdh7ENeRChHTYsTvWrMubiIAMNS2llXEEgZ1MUOBtXChP3kaFQ==",
+ "version": "5.3.0",
+ "resolved": "https://registry.npmjs.org/ignore/-/ignore-5.3.0.tgz",
+ "integrity": "sha512-g7dmpshy+gD7mh88OC9NwSGTKoc3kyLAZQRU1mt53Aw/vnvfXnbC+F/7F7QoYVKbV+KNvJx8wArewKy1vXMtlg==",
"dev": true,
"engines": {
"node": ">= 4"
@@ -3815,13 +3852,13 @@
"dev": true
},
"node_modules/internal-slot": {
- "version": "1.0.5",
- "resolved": "https://registry.npmjs.org/internal-slot/-/internal-slot-1.0.5.tgz",
- "integrity": "sha512-Y+R5hJrzs52QCG2laLn4udYVnxsfny9CpOhNhUvk/SSSVyF6T27FzRbF0sroPidSu3X8oEAkOn2K804mjpt6UQ==",
+ "version": "1.0.6",
+ "resolved": "https://registry.npmjs.org/internal-slot/-/internal-slot-1.0.6.tgz",
+ "integrity": "sha512-Xj6dv+PsbtwyPpEflsejS+oIZxmMlV44zAhG479uYu89MsjcYOhCFnNyKrkJrihbsiasQyY0afoCl/9BLR65bg==",
"dev": true,
"dependencies": {
- "get-intrinsic": "^1.2.0",
- "has": "^1.0.3",
+ "get-intrinsic": "^1.2.2",
+ "hasown": "^2.0.0",
"side-channel": "^1.0.4"
},
"engines": {
@@ -3876,6 +3913,21 @@
"url": "https://github.com/sponsors/ljharb"
}
},
+ "node_modules/is-builtin-module": {
+ "version": "3.2.1",
+ "resolved": "https://registry.npmjs.org/is-builtin-module/-/is-builtin-module-3.2.1.tgz",
+ "integrity": "sha512-BSLE3HnV2syZ0FK0iMA/yUGplUeMmNz4AW5fnTunbCIqZi4vG3WjJT9FHMy5D69xmAYBHXQhJdALdpwVxV501A==",
+ "dev": true,
+ "dependencies": {
+ "builtin-modules": "^3.3.0"
+ },
+ "engines": {
+ "node": ">=6"
+ },
+ "funding": {
+ "url": "https://github.com/sponsors/sindresorhus"
+ }
+ },
"node_modules/is-callable": {
"version": "1.2.7",
"resolved": "https://registry.npmjs.org/is-callable/-/is-callable-1.2.7.tgz",
@@ -3889,12 +3941,12 @@
}
},
"node_modules/is-core-module": {
- "version": "2.13.0",
- "resolved": "https://registry.npmjs.org/is-core-module/-/is-core-module-2.13.0.tgz",
- "integrity": "sha512-Z7dk6Qo8pOCp3l4tsX2C5ZVas4V+UxwQodwZhLopL91TX8UyyHEXafPcyoeeWuLrwzHcr3igO78wNLwHJHsMCQ==",
+ "version": "2.13.1",
+ "resolved": "https://registry.npmjs.org/is-core-module/-/is-core-module-2.13.1.tgz",
+ "integrity": "sha512-hHrIjvZsftOsvKSn2TRYl63zvxsgE0K+0mYMoH6gD4omR5IWB2KynivBQczo3+wF1cCkjzvptnI9Q0sPU66ilw==",
"dev": true,
"dependencies": {
- "has": "^1.0.3"
+ "hasown": "^2.0.0"
},
"funding": {
"url": "https://github.com/sponsors/ljharb"
@@ -4109,9 +4161,9 @@
"dev": true
},
"node_modules/istanbul-lib-coverage": {
- "version": "3.2.0",
- "resolved": "https://registry.npmjs.org/istanbul-lib-coverage/-/istanbul-lib-coverage-3.2.0.tgz",
- "integrity": "sha512-eOeJ5BHCmHYvQK7xt9GkdHuzuCGS1Y6g9Gvnx3Ym33fz/HpLRYxiS0wHNr+m/MBC8B647Xt608vCDEvhl9c6Mw==",
+ "version": "3.2.2",
+ "resolved": "https://registry.npmjs.org/istanbul-lib-coverage/-/istanbul-lib-coverage-3.2.2.tgz",
+ "integrity": "sha512-O8dpsF+r0WV/8MNRKfnmrtCWhuKjxrq2w+jpzBL5UZKTi2LeVWnWOmWRxFlesJONmc+wLAGvKQZEOanko0LFTg==",
"dev": true,
"engines": {
"node": ">=8"
@@ -4950,17 +5002,17 @@
}
},
"node_modules/ldapjs": {
- "version": "3.0.5",
- "resolved": "https://registry.npmjs.org/ldapjs/-/ldapjs-3.0.5.tgz",
- "integrity": "sha512-W1baa/R/i5itkGdteMbz9Mwu/Tvs7DQQ2jy4cirwo6uQo1kpFzaQftNr45kC6xLC6/L24fUPcWf4tZ0cgkAiDQ==",
+ "version": "3.0.7",
+ "resolved": "https://registry.npmjs.org/ldapjs/-/ldapjs-3.0.7.tgz",
+ "integrity": "sha512-1ky+WrN+4CFMuoekUOv7Y1037XWdjKpu0xAPwSP+9KdvmV9PG+qOKlssDV6a+U32apwxdD3is/BZcWOYzN30cg==",
"dependencies": {
"@ldapjs/asn1": "^2.0.0",
"@ldapjs/attribute": "^1.0.0",
"@ldapjs/change": "^1.0.0",
- "@ldapjs/controls": "^2.0.0",
+ "@ldapjs/controls": "^2.1.0",
"@ldapjs/dn": "^1.1.0",
"@ldapjs/filter": "^2.1.1",
- "@ldapjs/messages": "^1.2.1",
+ "@ldapjs/messages": "^1.3.0",
"@ldapjs/protocol": "^1.2.1",
"abstract-logging": "^2.0.1",
"assert-plus": "^1.0.0",
@@ -5215,9 +5267,9 @@
"dev": true
},
"node_modules/node-releases": {
- "version": "2.0.13",
- "resolved": "https://registry.npmjs.org/node-releases/-/node-releases-2.0.13.tgz",
- "integrity": "sha512-uYr7J37ae/ORWdZeQ1xxMJe3NtdmqMC/JZK+geofDrkLUApKRHPd18/TxtBOJ4A0/+uUIliorNrfYV6s1b02eQ==",
+ "version": "2.0.14",
+ "resolved": "https://registry.npmjs.org/node-releases/-/node-releases-2.0.14.tgz",
+ "integrity": "sha512-y10wOWt8yZpqXmOgRo77WaHEmhYQYGNA6y421PKsKYWEK8aW+cqAphborZDhqfyKrbZEN92CN1X2KbafY2s7Yw==",
"dev": true
},
"node_modules/normalize-path": {
@@ -5260,13 +5312,13 @@
}
},
"node_modules/object.assign": {
- "version": "4.1.4",
- "resolved": "https://registry.npmjs.org/object.assign/-/object.assign-4.1.4.tgz",
- "integrity": "sha512-1mxKf0e58bvyjSCtKYY4sRe9itRk3PJpquJOjeIkz885CczcI4IvJJDLPS72oowuSh+pBxUFROpX+TU++hxhZQ==",
+ "version": "4.1.5",
+ "resolved": "https://registry.npmjs.org/object.assign/-/object.assign-4.1.5.tgz",
+ "integrity": "sha512-byy+U7gp+FVwmyzKPYhW2h5l3crpmGsxl7X2s8y43IgxvG4g3QZ6CffDtsNQy1WsmZpQbO+ybo0AlW7TY6DcBQ==",
"dev": true,
"dependencies": {
- "call-bind": "^1.0.2",
- "define-properties": "^1.1.4",
+ "call-bind": "^1.0.5",
+ "define-properties": "^1.2.1",
"has-symbols": "^1.0.3",
"object-keys": "^1.1.1"
},
@@ -5609,9 +5661,9 @@
}
},
"node_modules/process-warning": {
- "version": "2.2.0",
- "resolved": "https://registry.npmjs.org/process-warning/-/process-warning-2.2.0.tgz",
- "integrity": "sha512-/1WZ8+VQjR6avWOgHeEPd7SDQmFQ1B5mC1eRXsCm5TarlNmx/wCsa5GEaxGm05BORRtyG/Ex/3xq3TuRvq57qg=="
+ "version": "2.3.2",
+ "resolved": "https://registry.npmjs.org/process-warning/-/process-warning-2.3.2.tgz",
+ "integrity": "sha512-n9wh8tvBe5sFmsqlg+XQhaQLumwpqoAUruLwjCopgTmUBjJ/fjtBsJzKleCaIGBOMXYEhp1YfKl4d7rJ5ZKJGA=="
},
"node_modules/prompts": {
"version": "2.4.2",
@@ -5632,9 +5684,9 @@
"integrity": "sha512-D+zkORCbA9f1tdWRK0RaCR3GPv50cMxcrz4X8k5LTSUD1Dkw47mKJEZQNunItRTkWwgtaUSo1RVFRIG9ZXiFYg=="
},
"node_modules/punycode": {
- "version": "2.3.0",
- "resolved": "https://registry.npmjs.org/punycode/-/punycode-2.3.0.tgz",
- "integrity": "sha512-rRV+zQD8tVFys26lAGR9WUuS4iUAngJScM+ZRSKtvl5tKeZ2t5bvdNFdNHBW9FWR4guGHlgmsZ1G7BSm2wTbuA==",
+ "version": "2.3.1",
+ "resolved": "https://registry.npmjs.org/punycode/-/punycode-2.3.1.tgz",
+ "integrity": "sha512-vYt7UD1U9Wg6138shLtLOvdAu+8DsC/ilFtEVHcH+wydcSpNE20AfSOduf6MkRFahL5FY7X1oU7nKVZFtfq8Fg==",
"dev": true,
"engines": {
"node": ">=6"
@@ -5889,15 +5941,18 @@
}
},
"node_modules/safe-regex-test": {
- "version": "1.0.0",
- "resolved": "https://registry.npmjs.org/safe-regex-test/-/safe-regex-test-1.0.0.tgz",
- "integrity": "sha512-JBUUzyOgEwXQY1NuPtvcj/qcBDbDmEvWufhlnXZIm75DEHp+afM1r1ujJpJsV/gSM4t59tpDyPi1sd6ZaPFfsA==",
+ "version": "1.0.1",
+ "resolved": "https://registry.npmjs.org/safe-regex-test/-/safe-regex-test-1.0.1.tgz",
+ "integrity": "sha512-Y5NejJTTliTyY4H7sipGqY+RX5P87i3F7c4Rcepy72nq+mNLhIsD0W4c7kEmduMDQCSqtPsXPlSTsFhh2LQv+g==",
"dev": true,
"dependencies": {
- "call-bind": "^1.0.2",
- "get-intrinsic": "^1.1.3",
+ "call-bind": "^1.0.5",
+ "get-intrinsic": "^1.2.2",
"is-regex": "^1.1.4"
},
+ "engines": {
+ "node": ">= 0.4"
+ },
"funding": {
"url": "https://github.com/sponsors/ljharb"
}
@@ -6228,9 +6283,9 @@
}
},
"node_modules/tsconfig-paths": {
- "version": "3.14.2",
- "resolved": "https://registry.npmjs.org/tsconfig-paths/-/tsconfig-paths-3.14.2.tgz",
- "integrity": "sha512-o/9iXgCYc5L/JxCHPe3Hvh8Q/2xm5Z+p18PESBU6Ff33695QnCHBEjcytY2q19ua7Mbl/DavtBOLq+oG0RCL+g==",
+ "version": "3.15.0",
+ "resolved": "https://registry.npmjs.org/tsconfig-paths/-/tsconfig-paths-3.15.0.tgz",
+ "integrity": "sha512-2Ac2RgzDe/cn48GvOe3M+o82pEFewD3UPbyoUHHdKasHwJKjds4fLXWf/Ux5kATBKN20oaFGu+jbElp1pos0mg==",
"dev": true,
"dependencies": {
"@types/json5": "^0.0.29",
@@ -6380,9 +6435,9 @@
}
},
"node_modules/typescript": {
- "version": "5.2.2",
- "resolved": "https://registry.npmjs.org/typescript/-/typescript-5.2.2.tgz",
- "integrity": "sha512-mI4WrpHsbCIcwT9cF4FZvr80QUeKvsUsUvKDoR+X/7XHQH98xYD8YHZg7ANtz2GtZt/CBq2QJ0thkGJMHfqc1w==",
+ "version": "5.3.3",
+ "resolved": "https://registry.npmjs.org/typescript/-/typescript-5.3.3.tgz",
+ "integrity": "sha512-pXWcraxM0uxAS+tN0AG/BF2TyqmHO014Z070UsJ+pFvYuRSq8KH8DmWpnbXe0pEPDHXZV3FcAbJkijJ5oNEnWw==",
"dev": true,
"peer": true,
"bin": {
@@ -6409,9 +6464,9 @@
}
},
"node_modules/undici-types": {
- "version": "5.25.3",
- "resolved": "https://registry.npmjs.org/undici-types/-/undici-types-5.25.3.tgz",
- "integrity": "sha512-Ga1jfYwRn7+cP9v8auvEXN1rX3sWqlayd4HP7OKk4mZWylEmu3KzXDUGrQUN6Ol7qo1gPvB2e5gX6udnyEPgdA==",
+ "version": "5.26.5",
+ "resolved": "https://registry.npmjs.org/undici-types/-/undici-types-5.26.5.tgz",
+ "integrity": "sha512-JlCMO+ehdEIKqlFxk6IfVoAUVmgz7cU7zD/h9XZ0qzeosSHmUJVOzSQvvYSYWXkFXC+IfLKSIffhv0sVZup6pA==",
"dev": true
},
"node_modules/update-browserslist-db": {
@@ -6462,9 +6517,9 @@
}
},
"node_modules/v8-to-istanbul": {
- "version": "9.1.3",
- "resolved": "https://registry.npmjs.org/v8-to-istanbul/-/v8-to-istanbul-9.1.3.tgz",
- "integrity": "sha512-9lDD+EVI2fjFsMWXc6dy5JJzBsVTcQ2fVkfBvncZ6xJWG9wtBhOldG+mHkSL0+V1K/xgZz0JDO5UT5hFwHUghg==",
+ "version": "9.2.0",
+ "resolved": "https://registry.npmjs.org/v8-to-istanbul/-/v8-to-istanbul-9.2.0.tgz",
+ "integrity": "sha512-/EH/sDgxU2eGxajKdwLCDmQ4FWq+kpi3uCmBGpw1xJtnAxEjlD8j8PEiGWpCIMIs3ciNAgH0d3TTJiUkYzyZjA==",
"dev": true,
"dependencies": {
"@jridgewell/trace-mapping": "^0.3.12",
diff --git a/package.json b/package.json
index 3828822..d5937c1 100644
--- a/package.json
+++ b/package.json
@@ -1,6 +1,6 @@
{
"name": "AzureAD-LDAP-wrapper",
- "version": "2.0.1",
+ "version": "2.0.2",
"type": "commonjs",
"engines": {
"node": ">=17"
@@ -20,24 +20,24 @@
"url": "https://github.com/ahaenggli/AzureAD-LDAP-wrapper"
},
"dependencies": {
- "@azure/msal-node": "2.2.0",
- "axios": "~1.6.0",
+ "@azure/msal-node": "2.6.1",
+ "axios": "~1.6.5",
"diacritic": "0.0.2",
"dotenv": "^16.3.1",
"fs": "0.0.1-security",
"hashcode": "1.0.3",
"https-proxy-agent": "7.0.2",
- "ldapjs": "~3.0.5"
+ "ldapjs": "~3.0.7"
},
"devDependencies": {
- "eslint": "^8.51.0",
+ "eslint": "^8.56.0",
"eslint-config-standard": "^17.1.0",
- "eslint-plugin-import": "^2.28.1",
- "eslint-plugin-n": "^16.2.0",
+ "eslint-plugin-import": "^2.29.1",
+ "eslint-plugin-n": "^16.6.2",
"eslint-plugin-node": "~11.1.0",
"eslint-plugin-promise": "^6.1.1",
- "eslint-plugin-jest": "^27.4.2",
- "eslint-plugin-security": "~1.7.1",
+ "eslint-plugin-jest": "^27.6.2",
+ "eslint-plugin-security": "~2.1.0",
"jest": "^29.7.0"
}
}
\ No newline at end of file
-AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from Azure Active Directory to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This enables other applications to connect to the LDAP server and utilize AzureAD login credentials, making it a possible solution for older applications that lack AzureAD support or for scenarios where managing a local AD controller is undesirable.
+LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from `Microsoft Entra ID` (formerly `Azure Active Directory`) to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This allows your other applications to connect to the LDAP server and thus allows your end users to authenticate with a work or school account.
+
+This it a possible workaround for older applications that lack Microsoft Entra ID support or for scenarios where managing a local AD controller is undesirable.
## Table of Contents
@@ -10,7 +12,7 @@ AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://
* [Run the LDAP-wrapper](#run-the-ldap-wrapper)
* [Usage](#usage)
* [Settings](#settings)
-* [Troubleshooting](#troubleshooting)
+* [Troubleshooting / FAQ](#troubleshooting-/-faq)
* [Security](#security)
* [Contributing](#contributing)
* [Support this project](#support-this-project)
@@ -22,49 +24,49 @@ AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://
sequenceDiagram
autonumber
participant LDAP client
- participant AzureAD-LDAP-wrapper
- participant AAD (Graph API)
+ participant LDAP-wrapper
+ participant ME-ID (Graph API)
- Note over AzureAD-LDAP-wrapper: start LDAP server
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups
- Note over AzureAD-LDAP-wrapper: cache users and groups locally
+ Note over LDAP-wrapper: start LDAP server
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups
+ Note over LDAP-wrapper: cache users and groups locally
- LDAP client->>+AzureAD-LDAP-wrapper: Attempt to bind with user credentials
- AzureAD-LDAP-wrapper->>+AAD (Graph API): Check user credentials
- AAD (Graph API)-->>-AzureAD-LDAP-wrapper: Valid credentials
+ LDAP client->>+LDAP-wrapper: Attempt to bind with user credentials
+ LDAP-wrapper->>+ME-ID (Graph API): Check user credentials
+ ME-ID (Graph API)-->>-LDAP-wrapper: Valid credentials
- Note over AzureAD-LDAP-wrapper: save password hash locally in the cache
- AzureAD-LDAP-wrapper->>-LDAP client: Successful bind/authenticate
+ Note over LDAP-wrapper: save password hash locally in the cache
+ LDAP-wrapper->>-LDAP client: Successful bind/authenticate
loop every 30 minutes
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups again
- Note over AzureAD-LDAP-wrapper: merge and cache users and groups locally
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups again
+ Note over LDAP-wrapper: merge and cache users and groups locally
end
```
-The AzureAD-LDAP-wrapper starts an LDAP server and fetches users and groups from the AAD Graph API. These are cached and merged locally.
+The LDAP-wrapper starts an LDAP server and fetches users and groups from the Microsoft Graph API. These are cached and merged locally.
-When an LDAP client attempts to bind with user credentials, the AzureAD-LDAP-wrapper checks these credentials by communicating with the AAD Graph API. If the credentials are valid, the AAD Graph API sends a success response to the AzureAD-LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the AzureAD-LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
+When an LDAP client attempts to bind with user credentials, the LDAP-wrapper checks these credentials by communicating with the Microsoft Graph API. If the credentials are valid, the Microsoft Graph API sends a success response to the LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
-The AzureAD-LDAP-wrapper periodically fetches user and group information from the AAD Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
+The LDAP-wrapper periodically fetches user and group information from the Microsoft Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
## Getting Started
### Requirements
-To use the AzureAD-LDAP-wrapper, you will need:
+To use the LDAP-wrapper, you will need:
-* An Azure Active Directory (AD) tenant with at least one registered user.
-* An Azure AD application registered in your tenant, with the following permissions:
+* A Microsoft Entra tenant with at least one registered user.
+* A Microsoft Entra application registered in your tenant, with the following permissions:
* For type `Application` grant `User.Read.All` and `Group.Read.All`.
* For type `Delegated` grant `User.Read`.
You can follow the instructions in the [installation guide](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/installation/create-azuread-application) to set up your application.
-To run the AzureAD-LDAP-wrapper, you'll need to have your Tenant ID, Application ID, and Application Secret available. These values are required to authenticate and authorize the application to access your Azure AD resources. You can find these values in the Azure portal.
+To run the LDAP-wrapper, you'll need to have your Tenant ID, Application ID, and Application Secret available. These values are required to authenticate and authorize the application to access your resources. You can find these values in the Microsoft Entra ID portal.
-Once you have created your Azure AD application, you can run the LDAP wrapper on your local machine, on a server or even a Synology NAS. Depending on your setup you will either need:
+Once you have created your Microsoft Entra application, you can run the LDAP-wrapper on your local machine, on a server or even a Synology NAS. Depending on your setup you will either need:
* Node.js version 17 or higher, which can be downloaded from the official [Node.js website](https://nodejs.org/en/download/).
@@ -93,7 +95,7 @@ Use "bridge" as your network.
4. Give your container a name and enable auto-restart.

-5. Configure the environment variables in "Advanced Settings". Be sure to double check your Azure values and define at least one binduser. The binduser (superuser like root) does not need to exist in your AzureAD. Replace example.com with your domain. Here is an example of a minimum required configuration:
+5. Configure the environment variables in "Advanced Settings". Be sure to double check your Microsoft Entra values and define at least one binduser. The binduser (superuser like root) does not need to exist in your tenant. Replace example.com with your domain. Here is an example of a minimum required configuration:
```bash
TZ: "Europe/Zurich" # optional
@@ -109,7 +111,7 @@ Use "bridge" as your network.
```

- A full list of all environment variables can be found [here](../../configuration/settings/).
+ A full list of all environment variables can be found [here](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/configuration/settings/).
6. Set local Port 389 to the Container Port 13389. If you receive the error Local port 389 conflicts with other ports used by other services, make sure that Synology Directory Service and Synology LDAP Server are not installed - they also use this port.

@@ -122,7 +124,7 @@ Use "bridge" as your network.
### Usage
-To enable users to log in to Synology NAS with their Azure credentials, you need to connect the NAS to the AzureAD-LDAP-wrapper. Here are the steps:
+To enable end users to log in to Synology NAS with their work or school account, you need to connect the NAS to the LDAP-wrapper. Here are the steps:
1. Go to Control Panel > Domain/LDAP and click "Join".

@@ -136,10 +138,10 @@ To enable users to log in to Synology NAS with their Azure credentials, you need
4. If you see a warning about a local group having the same name as a synchronized group, you can ignore it and skip the warning in "Details".

-5. Your NAS should now be connected successfully to the Azure AD LDAP-wrapper.
+5. Your NAS should now be connected successfully to the LDAP-wrapper.

-6. Check the "LDAP User" and "LDAP Group" tabs to ensure that all entries are fully synced. Assign the desired permissions to your synchronized users and groups. You can now log in with your Azure AD credentials.
+6. Check the "LDAP User" and "LDAP Group" tabs to ensure that all entries are fully synced. Assign the desired permissions to your synchronized users and groups. You can now log in with your Microsoft Entra account (work or school account).

7. Note that before accessing shared folders or files via network or Samba, each user must log in to DSM web GUI or another tool directly connected to the LDAP server. This step is also required after a password change, as the password hash for Samba is only set after a successful login.
@@ -148,19 +150,19 @@ To enable users to log in to Synology NAS with their Azure credentials, you need
To configure the LDAP-wrapper, you can use environment variables as it is intended to be used with Docker. A complete list of available variables can be found in the [configuration settings page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/configuration/settings) of the documentation.
-## Troubleshooting
+## Troubleshooting / FAQ
If you encounter any issues, start by checking the Docker log. Many errors are logged there, and this can help you identify the root cause of the problem. Additionally, the [troubleshooting page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/troubleshooting/) in the documentation provides further guidance on debugging common issues, including Samba-related ones. If you're still stuck, don't hesitate to open an issue, but be sure to attach relevant log files to help others diagnose the issue.
## Security
-It's important to note that the AzureAD-LDAP-wrapper involves transferring sensitive user information, so it's essential to ensure that it's used securely. There are several potential security risks to be aware of when using this wrapper. For more information on these risks and how to mitigate them, please read the [security page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/security/) in the documentation.
+It's important to note that the LDAP-wrapper involves transferring sensitive user information, so it's essential to ensure that it's used securely. There are several potential security risks to be aware of when using this wrapper. For more information on these risks and how to mitigate them, please read the [security page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/security/) in the documentation.
If you discover any security vulnerabilities, please refer to the instructions in [SECURITY.md](SECURITY.md) on how to report them.
## Contributing
-Contributions to the AzureAD-LDAP-wrapper are always welcome! If you have any suggestions, bug reports, or pull requests, please feel free to open an issue or a pull request on the project's GitHub repository.
+Contributions to the LDAP-wrapper are always welcome! If you have any suggestions, bug reports, or pull requests, please feel free to open an issue or a pull request on the project's GitHub repository.
## Support this project
@@ -170,4 +172,4 @@ Your support helps me maintain and improve this project. Thank you!
## License
-The AzureAD-LDAP-wrapper is licensed under the [MIT License](LICENSE).
+The LDAP-wrapper is licensed under the [MIT License](LICENSE).
diff --git a/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js b/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js
new file mode 100644
index 0000000..e8a6d7c
--- /dev/null
+++ b/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js
@@ -0,0 +1,111 @@
+/**
+ * This module contains customizer functions for modifying LDAP and Azure objects.
+ * @module customizer
+ *
+ * Modify the following variables to your needs:
+ * pets - The list of group names to filter the Azure groups by.
+ * Only users within these groups will be synced.
+ */
+
+'use strict';
+
+// keep only users within these groups from Azure
+const pets = ['group-b', 'administrators'];
+
+const config = require('../src/config');
+const helper = require('../src/helper');
+
+var customizer = {};
+
+/**
+ * Modifies the Azure groups by filtering them based on a predefined list of group names.
+ * @param {Array} azuregroups - The array of Azure groups.
+ * @returns {Array} - The modified array of Azure groups.
+ */
+customizer.ModifyAzureGroups = function (azuregroups) {
+ return azuregroups.filter(group => pets.includes(group.displayName.toLowerCase()));
+};
+
+/**
+ * Modifies the LDAP group by converting the gidNumber from string to int.
+ * @param {Object} ldapgroup - The LDAP group object.
+ * @param {Object} azuregroup - The Azure group object.
+ * @returns {Object} - The modified LDAP group object.
+ */
+customizer.ModifyLDAPGroup = function (ldapgroup, azuregroup) {
+ helper.log("customizer", "ModifyLDAPGroup", "called");
+ if (ldapgroup.hasOwnProperty("gidNumber")) {
+ let parsed = parseInt(ldapgroup.gidNumber);
+ if (isNaN(parsed)) parsed = ldapgroup.gidNumber;
+ ldapgroup.gidNumber = parsed;
+ }
+
+ return ldapgroup;
+};
+
+/**
+ * Modifies the LDAP user by converting the gidNumber and uidNumber from string to int.
+ * Sets gidNumber to 0 if the user has no groups.
+ * @param {Object} ldapuser - The LDAP user object.
+ * @param {Object} azureuser - The Azure user object.
+ * @returns {Object} - The modified LDAP user object.
+ */
+customizer.ModifyLDAPUser = function (ldapuser, azureuser) {
+ helper.log("customizer", "ModifyLDAPUser", "called");
+ if (ldapuser.hasOwnProperty("gidNumber")) {
+ let parsed = parseInt(ldapuser.gidNumber);
+ if (isNaN(parsed)) parsed = ldapuser.gidNumber;
+ ldapuser.gidNumber = parsed;
+ }
+ if (ldapuser.hasOwnProperty("uidNumber")) {
+ let parsed = parseInt(ldapuser.uidNumber);
+ if (isNaN(parsed)) parsed = ldapuser.uidNumber;
+ ldapuser.uidNumber = parsed;
+ }
+
+ // no groups for user? set gidNumber to 0
+ ldapuser.memberOf = ldapuser.memberOf.filter(e => e != config.LDAP_USERSGROUPSBASEDN);
+ if (Array.isArray(ldapuser.memberOf) && ldapuser.memberOf.length === 0) ldapuser.gidNumber = 0;
+
+ return ldapuser;
+};
+
+/**
+ * Modifies the LDAP objects globally by setting default values for certain properties.
+ * @param {Object} all - The object containing all LDAP objects.
+ * @returns {Object} - The modified object containing all LDAP objects.
+ */
+customizer.ModifyLDAPGlobal = function (all) {
+ let root = "uid=root," + config.LDAP_USERSDN;
+ for (var key of Object.keys(all)) {
+ all[key].creatorsName = root;
+
+ if (!all[key].hasOwnProperty("createTimestamp"))
+ all[key].createTimestamp = helper.ldap_now() + "Z";
+
+ if (!all[key].hasOwnProperty("entryCSN"))
+ all[key].entryCSN = helper.ldap_now() + ".000000Z#000000#000#000000";
+
+ all[key].modifiersName = root;
+
+ if (!all[key].hasOwnProperty("modifyTimestamp"))
+ all[key].modifyTimestamp = all[key].createTimestamp;
+
+ if (all[key].hasOwnProperty("sambaDomainName")) {
+ all[key].sambaDomainName = all[key].sambaDomainName.toLowerCase();
+ }
+
+ // only users with gidNumber > 0
+ if (all[key].hasOwnProperty("uidNumber")
+ && all[key].hasOwnProperty("gidNumber")
+ && all[key].uidNumber > 0
+ && all[key].gidNumber === 0
+ ) {
+ delete all[key];
+ }
+ }
+
+ return all;
+};
+
+module.exports = customizer;
\ No newline at end of file
diff --git a/docs/content/_index.md b/docs/content/_index.md
index b0e2b34..01f864d 100644
--- a/docs/content/_index.md
+++ b/docs/content/_index.md
@@ -1,12 +1,14 @@
---
-title: AzureAD-LDAP-wrapper
+title: LDAP-wrapper for Microsoft Entra ID
---
-AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from Azure Active Directory to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This enables other applications to connect to the LDAP server and utilize AzureAD login credentials, making it a possible solution for older applications that lack AzureAD support or for scenarios where managing a local AD controller is undesirable.
+LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from `Microsoft Entra ID` (formerly `Azure Active Directory`) to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This allows your other applications to connect to the LDAP server and thus allows your end users to authenticate with a work or school account.
+
+This it a possible workaround for older applications that lack Microsoft Entra ID support or for scenarios where managing a local AD controller is undesirable.
{{< hint type=note title="About the motivation" >}}
-I run the project on my Synology NAS in a Docker container. By connecting the NAS and some intranet web applications to the LDAP server, my users can log in to these services using their AzureAD credentials. Although it is possible to achieve this by [joining the NAS to AADDS](https://kb.synology.com/en-global/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain), I preferred not to maintain such a big setup, which includes a virtual machine, VPN, and AADDS, just to allow my three users to use their credentials almost everywhere.
+I run the project on my Synology NAS in a Docker container. By connecting the NAS and some intranet web applications to the LDAP server, my users can log in to these services using their work accounts. Although it is possible to achieve this by [joining the NAS to AADDS](https://kb.synology.com/en-global/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain), I preferred not to maintain such a big setup, which includes a virtual machine, VPN, and Microsoft Entra Domain Services (formerly AADDS / Azure Active Directory Domain Services), just to allow my three users to use their credentials almost everywhere.
{{< /hint >}}
@@ -16,31 +18,29 @@ I run the project on my Synology NAS in a Docker container. By connecting the NA
sequenceDiagram
autonumber
participant LDAP client
- participant AzureAD-LDAP-wrapper
- participant AAD (Graph API)
-
- Note over AzureAD-LDAP-wrapper: start LDAP server
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups
- Note over AzureAD-LDAP-wrapper: cache users and groups locally
-
- LDAP client->>+AzureAD-LDAP-wrapper: Attempt to bind with user credentials
- AzureAD-LDAP-wrapper->>+AAD (Graph API): Check user credentials
- AAD (Graph API)-->>-AzureAD-LDAP-wrapper: Valid credentials
-
- Note over AzureAD-LDAP-wrapper: save password hash locally in the cache
- AzureAD-LDAP-wrapper->>-LDAP client: Successful bind/authenticate
-
+ participant LDAP-wrapper
+ participant ME-ID (Graph API)
+
+ Note over LDAP-wrapper: start LDAP server
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups
+ Note over LDAP-wrapper: cache users and groups locally
+
+ LDAP client->>+LDAP-wrapper: Attempt to bind with user credentials
+ LDAP-wrapper->>+ME-ID (Graph API): Check user credentials
+ ME-ID (Graph API)-->>-LDAP-wrapper: Valid credentials
+
+ Note over LDAP-wrapper: save password hash locally in the cache
+ LDAP-wrapper->>-LDAP client: Successful bind/authenticate
+
loop every 30 minutes
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups again
- Note over AzureAD-LDAP-wrapper: merge and cache users and groups locally
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups again
+ Note over LDAP-wrapper: merge and cache users and groups locally
end
```
-The diagram shows the flow of communication between an LDAP client, the AzureAD-LDAP-wrapper, and the Azure Active Directory (AAD) via Graph API.
-
-First, the AzureAD-LDAP-wrapper starts an LDAP server and fetches users and groups from the AAD Graph API. These are cached and merged locally.
+The LDAP-wrapper starts an LDAP server and fetches users and groups from the Microsoft Graph API. These are cached and merged locally.
-When an LDAP client attempts to bind with user credentials, the AzureAD-LDAP-wrapper checks these credentials by communicating with the AAD Graph API. If the credentials are valid, the AAD Graph API sends a success response to the AzureAD-LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the AzureAD-LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
+When an LDAP client attempts to bind with user credentials, the LDAP-wrapper checks these credentials by communicating with the Microsoft Graph API. If the credentials are valid, the Microsoft Graph API sends a success response to the LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
-The AzureAD-LDAP-wrapper periodically fetches user and group information from the AAD Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
+The LDAP-wrapper periodically fetches user and group information from the Microsoft Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
diff --git a/docs/content/configuration/bypass-mfa.md b/docs/content/configuration/bypass-mfa.md
index 8a6a4ad..36e875f 100644
--- a/docs/content/configuration/bypass-mfa.md
+++ b/docs/content/configuration/bypass-mfa.md
@@ -2,25 +2,25 @@
title: Bypass MFA
---
-Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
+Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
There is no interactive window to enter another factor, and LDAP does not support this either.
If you need to use this LDAP-wrapper despite of activated MFA, there are two options:
-1. Disable MFA for this application in AzureAD (preferred).\
+1. Disable MFA for this application in your tenant (preferred).\
There are several ways to define MFA, but only some of them allows you to disable MFA.
- Per-user MFA\
- MFA could be [enabled individually](https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates) for each user. A possible workaround seems to be the [trusted IPs feature](https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings#trusted-ips), which allows to disable MFA for some IPs, but this feature requires Azure AD Premium.\
+ MFA could be [enabled individually](https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-userstates) for each user. A possible workaround seems to be the [trusted IPs feature](https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-mfasettings#trusted-ips), which allows to disable MFA for some IPs, but this feature requires Microsoft Entra ID Premium.\
If a login fails due to this MFA method, the error code is AADSTS50079.
- Security defaults\
- [Security defaults](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults) seems to be the only ways for customers using the free Azure AD plan to [enable multi-factor authentication](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-mfa-get-started#free-option) in their whole environment. It looks like there are no workarounds to disable MFA for certain IPs or applications.\
+ [Security defaults](https://learn.microsoft.com/en-us/entra/fundamentals/security-defaults) seems to be the only ways for customers using the free Microsoft Entra ID plan to [enable multi-factor authentication](https://learn.microsoft.com/en-us/entra/identity/authentication/concept-mfa-licensing#free-option) in their whole environment. It looks like there are no workarounds to disable MFA for certain IPs or applications.\
If a login fails due to this MFA method, the error code is AADSTS50076.
- Conditional Access\
- [Conditional Access](https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-all-users-mfa) can be used to require MFA for some or all the users. This is the most flexible way to activate MFA, but it is a premium feature. The settings allows to exclude certain apps. If a login fails due to this MFA method, the error codea are either AADSTS50158 (for external MFA like Duo) or also AADSTS50079. As a simple workaround, the app used by the LDAP-wrapper can be excluded:
- - Add a URL in the app (e.g. "https://localhost")
+ [Conditional Access](https://learn.microsoft.com/en-us/entra/identity/conditional-access/howto-conditional-access-policy-all-users-mfa) can be used to require MFA for some or all the users. This is the most flexible way to activate MFA, but it is a premium feature. The settings allows to exclude certain apps. If a login fails due to this MFA method, the error codea are either AADSTS50158 (for external MFA like Duo) or also AADSTS50079. As a simple workaround, the app used by the LDAP-wrapper can be excluded:
+ - Add a URL in the app (e.g. "")

- The App can now be selected in the exclude list

2. Let the LDAP-wrapper internally treat some MFA/2FA related error codes as a successful login.\
There is an experimental feature to ***bypass*** MFA/2FA. It must be manually enabled by setting the the env var `GRAPH_IGNORE_MFA_ERRORS` to true.\
- Even if the env var is set to true, the login attempt appears as "Failure" in the AzureAD sign-in logs due to MFA/2FA. Only the LDAP wrapper internally treats some MFA/2FA-related error codes as successful logins. Specifically, these are the error codes AADSTS50076, AADSTS50079 and AADSTS50158, as mentioned above.
+ Even if the env var is set to true, the login attempt appears as "Failure" in the Microsoft Entra ID sign-in logs due to MFA/2FA. Only the LDAP wrapper internally treats some MFA/2FA-related error codes as successful logins. Specifically, these are the error codes AADSTS50076, AADSTS50079 and AADSTS50158, as mentioned above.
diff --git a/docs/content/installation/create-azuread-application.md b/docs/content/installation/create-azuread-application.md
index 5251025..2c5986a 100644
--- a/docs/content/installation/create-azuread-application.md
+++ b/docs/content/installation/create-azuread-application.md
@@ -1,21 +1,21 @@
---
-title: 1.1 Create an AzureAD application
+title: 1.1 Register an application with the Microsoft identity platform
---
{{< toc format=raw >}}
## Prerequisites
-To register an application in your Azure AD tenant, you need:
+To register an application with the Microsoft identity platform, you need:
-- An Azure AD user account. If you don't already have one, you can [create an account for free](https://azure.microsoft.com/free/).
+- A Microsoft Entra ID user account. If you don't already have one, you can [create an account for free](https://azure.microsoft.com/free/).
-## Register an application with Azure AD and create a service principal
+## Register an application with the Microsoft identity platform
-Register a new application in your [aad-portal](https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps). More descriptions can be found [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/howto-create-service-principal-portal).
+Register a new application in your [Microsoft Entra Admin Center](https://entra.microsoft.com/#view/Microsoft_AAD_RegisteredApps/ApplicationsListBlade/quickStartType~/null/sourceType/Microsoft_AAD_IAM). More descriptions can be found [here](https://learn.microsoft.com/en-us/entra/identity-platform/howto-create-service-principal-portal).
-- Sign-in to the Azure portal.
-- Select Azure Active Directory and navigateo to [App registrations](https://aad.portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/RegisteredApps).
+- Sign-in to the Microsoft Entra Admin Center.
+- Browse to Identity > Applications > [App registrations](https://entra.microsoft.com/#view/Microsoft_AAD_RegisteredApps/ApplicationsListBlade/quickStartType~/null/sourceType/Microsoft_AAD_IAM)
- Select New registration.
- Name the application, for example "ldap-wrapper".
- Select a supported account type, which determines who can use the application.\
@@ -26,17 +26,17 @@ Register a new application in your [aad-portal](https://aad.portal.azure.com/#bl
## Set permissions
-- Set the following Graph-API Application permissions:
+- Set the following Microsoft Graph API Application permissions:
For type `Application` allow `User.Read.All` and `Group.Read.All`.\
For type `Delegated` allow `User.Read`.\
- 
+ 
- Click "Grant admin consent". The status should be "Granted for".\
If you see en entry with "Not granted for", click again:
- 
+ 
-- Set [Treat application as a public client](https://github.com/AzureAD/microsoft-authentication-library-for-dotnet/wiki/Username-Password-Authentication#application-registration) to `Yes`
-(former "Allow public client flows")
+- Set [Allow public client flows](https://learn.microsoft.com/de-de/entra/msal/dotnet/acquiring-tokens/desktop-mobile/username-password-authentication#application-registration) to `Yes`
+
## Get TenantId, AppId and AppSecret
diff --git a/docs/content/installation/azure_ROPC.png b/docs/content/installation/entra_ROPC.png
similarity index 100%
rename from docs/content/installation/azure_ROPC.png
rename to docs/content/installation/entra_ROPC.png
diff --git a/docs/content/installation/azure_permissions.png b/docs/content/installation/entra_permissions.png
similarity index 100%
rename from docs/content/installation/azure_permissions.png
rename to docs/content/installation/entra_permissions.png
diff --git a/docs/content/installation/azure_permissions_notgranted.png b/docs/content/installation/entra_permissions_notgranted.png
similarity index 100%
rename from docs/content/installation/azure_permissions_notgranted.png
rename to docs/content/installation/entra_permissions_notgranted.png
diff --git a/docs/content/installation/run-ldap-wrapper.md b/docs/content/installation/run-ldap-wrapper.md
index af1f930..3daee9e 100644
--- a/docs/content/installation/run-ldap-wrapper.md
+++ b/docs/content/installation/run-ldap-wrapper.md
@@ -4,7 +4,7 @@ title: Run the LDAP-wrapper
The preferred way to use the LDAP wrapper is with Docker. Alternatively, the source can be downloaded and started manually with npm/node.
-As domain (and basedn, if manually specified) it is recommended to use the same as used in AzureAD tenant (e.g. `@domain.tld`). This way, the spelling of the users (e.g. `username@domain.tld`) will match at the end. Otherwise, your users will have to use `username@example.com` instead of the estimated `username@domain.tld`, for example.
+As domain (and basedn, if manually specified) it is recommended to use the same as used in your Microsoft Entra tenant (e.g. `@domain.tld`). This way, the spelling of the users (e.g. `username@domain.tld`) will match at the end. Otherwise, your users will have to use `username@example.com` instead of the estimated `username@domain.tld`, for example.
{{< hint type=note >}}
The API results and a local copy of the LDAP entries are stored as JSON files inside the container at this path: `/app/.cache`
@@ -35,7 +35,7 @@ Use "bridge" as your network.
4. Give your container a name and enable auto-restart.

-5. Configure the environment variables in "Advanced Settings". Be sure to double check your Azure values and define at least one binduser. The binduser (superuser like root) does not need to exist in your AzureAD. Replace example.com with your domain. Here is an example of a minimum required configuration:
+5. Configure the environment variables in "Advanced Settings". Be sure to double check your AZURE_* values and define at least one binduser. The binduser (superuser like root) does not need to exist in your Microsoft Entra tenant. Replace example.com with your domain. Here is an example of a minimum required configuration:
```bash
TZ: "Europe/Zurich" # optional
@@ -69,6 +69,7 @@ Use "bridge" as your network.
docker run -d `
-p 389:13389 `
--volume /volume1/docker/ldapwrapper:/app/.cache `
+-e TZ="Europe/Zurich" `
-e AZURE_TENANTID="0def2345-ff01-56789-1234-ab9d6dda1e1e" `
-e AZURE_APP_ID="abc12345-ab01-0000-1111-a1e1eab9d6dd" `
-e AZURE_APP_SECRET="iamasecret~yep-reallyreallysecret" `
@@ -141,7 +142,7 @@ You can either set environment variables or create an .env file in the root dire
```env
## .env file or environment variables ##
-# Values of your AzureAD application
+# Values of your Microsoft Entra application
AZURE_APP_ID="abc12345-ab01-0000-1111-a1e1eab9d6dd"
AZURE_TENANTID="0def2345-ff01-56789-1234-ab9d6dda1e1e"
AZURE_APP_SECRET="iamasecret~yep-reallyreallysecret"
diff --git a/docs/content/security/_index.md b/docs/content/security/_index.md
index bf2c799..08eff41 100644
--- a/docs/content/security/_index.md
+++ b/docs/content/security/_index.md
@@ -9,7 +9,7 @@ title: 3. Security
- An LDAP search on the NAS must be possible without any authentication in order to be able to select the domain/baseDN at all.
Therefore, some queries can be run as anonymous by default. Data like domain/baseDN or schema can be fetched without authentication.
- Since this LDAP-wrapper is originally only meant to use the same credentials as in Azure on a NAS, this is the default behaviour.
+ Since this LDAP-wrapper is originally only meant to use my work account (Microsoft Entra Account) on a NAS, this is the default behaviour.
You can change this via the env var `LDAP_ANONYMOUSBIND` if required.
- In order to use samba, the user credentials hashes are cached in the ldap attribute sambaNTPassword.\
@@ -19,13 +19,13 @@ However, if you do not disable the cache, there is a special treatment for these
- Each user has access to his own cached credential hash.
- In all other cases the attribute is returned with XXXX instead of the hash value.
-- In cases such as network/internet issues or Azure not being reachable, the cached hash is used for authentication.\
+- In cases such as network/internet issues or Microsoft Graph API / Entra ID not being reachable, the cached hash is used for authentication.\
This can be a problem if the user has been deactivated in the meantime or the password would be invalid.
The use of the cached password during authentication can be disabled by setting the `LDAP_ALLOWCACHEDLOGINONFAILURE` parameter to false.
- Using the experimental feature to bypass MFA/2FA\
- Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
- There is an experimental feature to **bypass** MFA/2FA. It must be manually enabled by setting the the env var `GRAPH_IGNORE_MFA_ERRORS` to true. Even if the env var is set to true, the login attempt appears as "Failure" in the AzureAD sign-in logs due to MFA/2FA. It is only the LDAP-wrapper that internally treats some MFA/2FA related error codes as a successful login.
+ Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
+ There is an experimental feature to **bypass** MFA/2FA. It must be manually enabled by setting the the env var `GRAPH_IGNORE_MFA_ERRORS` to true. Even if the env var is set to true, the login attempt appears as "Failure" in the Microsoft Entra ID sign-in logs due to MFA/2FA. It is only the LDAP-wrapper that internally treats some MFA/2FA related error codes as a successful login.
- Mapped docker volume\
Be aware that other users with access on your file system may also be able to read the JSON files in the mounted docker path (/app/.cache) and thus get access to the cached sambaNTPassword attribute.
diff --git a/docs/content/troubleshooting/_index.md b/docs/content/troubleshooting/_index.md
index 9bf97bc..b3a8c36 100644
--- a/docs/content/troubleshooting/_index.md
+++ b/docs/content/troubleshooting/_index.md
@@ -9,15 +9,15 @@ The first step is always to look at the Docker log. Many errors are handled ther
- [How do I give some synced users the DSM-Administrator permission on a Synology-NAS?](#how-do-i-give-some-synced-users-the-dsm-administrator-permission-on-a-synology-nas)
- [Can I use LDAPS (LDAP over SSL) instead of LDAP (with no encryption)?](#can-i-use-ldaps-ldap-over-ssl-instead-of-ldap-with-no-encryption)
- [Can I use LDAP over TLS (STARTTLS) instead of LDAP (with no encryption)?](#can-i-use-ldap-over-tls-starttls-instead-of-ldap-with-no-encryption)
-- [Join NAS to Azure AD Domain](#join-nas-to-azure-ad-domain)
+- [Join NAS to Microsoft Entra Domain Services](#join-nas-to-microsoft-entra-domain-services)
- [Why are personal microsoft accounts not supported?](#why-are-personal-microsoft-accounts-not-supported)
- [Samba is not working, what can I do?](#samba-is-not-working-what-can-i-do)
-- [Are deleted users or groups in Azure also removed from the LDAP entries?](#are-deleted-users-or-groups-in-azure-also-removed-from-the-ldap-entries)
+- [Are deleted users or groups in Entra also removed from the LDAP entries?](#are-deleted-users-or-groups-in-entra-also-removed-from-the-ldap-entries)
## Does it support MFA (multi-factor authentication)?
Yes and no... There is an experimental feature to bypass MFA/2FA. It can be enabled by setting the the env var `GRAPH_IGNORE_MFA_ERRORS` to `true`.
-Officially no, because the login simply fails, as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93). Even if the env var is set to true, the login attempt appears as "Failure" in the AzureAD sign-in logs due to MFA/2FA. It is only the LDAP-wrapper that internally treats some MFA/2FA related error codes as a successful login.
+Officially no, because the login simply fails, as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93). Even if the env var is set to true, the login attempt appears as "Failure" in the Microsoft Entra sign-in logs due to MFA/2FA. It is only the LDAP-wrapper that internally treats some MFA/2FA related error codes as a successful login.
## How do I give some synced users the DSM-Administrator permission on a Synology-NAS?
@@ -32,15 +32,15 @@ Sure. Mount your certificate file and private key file to the docker container a
Nope, that's not (yet) possible.
-## Join NAS to Azure AD Domain
+## Join NAS to Microsoft Entra Domain Services
-If you don't need support for older software, the officially Synology solution to [join your NAS to a Azure AD Domain](https://kb.synology.com/en-my/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain) will work fine.
+If you don't need support for older software, the officially Synology solution to [join your NAS to a Microsoft Entra Domain Services](https://kb.synology.com/en-my/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain) will work fine.
My wrapper creates an entire ldap server. So you can use it with several 3rd party (legacy) software in the same network.
## Why are personal microsoft accounts not supported?
-This wrapper uses the ROPC flow for authentication. Microsoft doesn't support that for personal accounts as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc):
-> Personal accounts that are invited to an Azure AD tenant can't use ROPC.
+This wrapper uses the ROPC flow for authentication. Microsoft doesn't support that for personal accounts as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc):
+> Personal accounts that are invited to an Microsoft Entra tenant can't use ROPC.
## Samba is not working, what can I do?
@@ -51,7 +51,7 @@ Check the following points first:
- Look into the docker Log. Are there any errors you should resolve? 
- Did you really connect your device/NAS with a non-existing user from the env var `LDAP_BINDUSER`? Otherwise the required password hash for Samba is not available and access will fail.
- Before accessing files via network/Samba, each user must log in to dsm-web-gui or another tool that is directly connected to the ldap server. This also applies after a password change, since the password hash for Samba is only set after a successful login.
-- Is your (Windows) device connected to Azure? Make sure you log in with username/password over the network, not with your pin code.
+- Is your (Windows) device connected to Microsoft Entra (formerly Azure AD joined devices)? Make sure you log in with username/password over the network, not with your pin code.
- Can you successfully access the shares with a local user?
- Make sure Synology Directory Service and Synology LDAP server are not installed.
- Maybe there is someting in the samba log. Get it to open an issue:
@@ -62,6 +62,6 @@ Check the following points first:
- Run `cat /var/log/samba/log.smbd` and copy the latest error/fail/... messages - please replace sensitive informations like domains, ip addresses or names.
- Don't forget to disable "collect debug logs" before opening an issue
-## Are deleted users or groups in Azure also removed from the LDAP entries?
+## Are deleted users or groups in Entra also removed from the LDAP entries?
-Yes, but with a delay. After a user has been deleted in Azure, it remains available there for about 30 days to undo the deletion. The API stops listing the user a earlier, a few hours after the deletion. In the meantime, the wrapper fetches the user as usual. After this time, the wrapper no longer receives the user. The deletion in the wrapper takes place 7 days later. Why not removing the user immediately? A user could also no longer be in the wrapper due to a misconfigured filter (env var). But just because of such an error, users (and their cached password hashes) should not be deleted immediately. Why not keeping it also 30 days? The user can no longer log in anyway. If the time span is too long (or short), it can be adjusted via the environment variable LDAP_DAYSTOKEEPDELETEDUSERS.
\ No newline at end of file
+Yes, but with a delay. After a user has been deleted in Microsoft Entra, it remains available there for about 30 days to undo the deletion. The API stops listing the user a earlier, a few hours after the deletion. In the meantime, the wrapper fetches the user as usual. After this time, the wrapper no longer receives the user. The deletion in the wrapper takes place 7 days later. Why not removing the user immediately? A user could also no longer be in the wrapper due to a misconfigured filter (env var). But just because of such an error, users (and their cached password hashes) should not be deleted immediately. Why not keeping it also 30 days? The user can no longer log in anyway. If the time span is too long (or short), it can be adjusted via the environment variable LDAP_DAYSTOKEEPDELETEDUSERS.
diff --git a/docs/content/usage/_index.md b/docs/content/usage/_index.md
new file mode 100644
index 0000000..7f87476
--- /dev/null
+++ b/docs/content/usage/_index.md
@@ -0,0 +1,9 @@
+---
+title: Usage examples
+---
+
+{{< hint type=note >}}
+
+Some examples how to use the LDAP-wrapper. This may also help configure similar services/apps.
+
+{{< /hint >}}
diff --git a/docs/content/usage/authelia.md b/docs/content/usage/authelia.md
new file mode 100644
index 0000000..98af88b
--- /dev/null
+++ b/docs/content/usage/authelia.md
@@ -0,0 +1,89 @@
+---
+title: 6.2 Authelia with LDAP-wrapper
+---
+
+Authelia supports LDAP authentication, enabling users to log in by authenticating against your LDAP directory. This guide outlines the steps to set up LDAP authentication with Authelia using LDAP-wrapper.
+
+{{< toc format=raw >}}
+
+## Prerequisites
+
+Before configuring LDAP authentication for Authelia with LDAP-wrapper, ensure the following prerequisites are met:
+
+- **LDAP-wrapper**: Ensure you have a functioning [LDAP-wrapper](https://github.com/ahaenggli/AzureAD-LDAP-wrapper/).
+- **Authelia**: Set up and configure [Authelia](https://www.authelia.com/overview/prologue/introduction/) for your environment.
+
+## Settings for Authelia LDAP Authentication with LDAP-wrapper
+
+To configure LDAP authentication with Authelia using LDAP-wrapper, follow these steps:
+
+1. Open your `configuration.yml` file in the Authelia configuration directory.
+2. Locate the `authentication_backend` section and configure it with the following example, adjusting the `url`,`base_dn`, `user`, and `password` based on your LDAP-wrapper setup:
+
+```yaml
+ ## Authentication Backend Provider Configuration
+ authentication_backend:
+
+ ## Password Reset Options
+ password_reset:
+ ## Disable both the HTML element and the API for reset password functionality.
+ disable: true
+ ## External reset password url for Microsoft
+ custom_url: "https://account.activedirectory.windowsazure.com/ChangePassword.aspx"
+
+ ## The amount of time to wait before we refresh data from the authentication backend. Uses duration notation
+ ## See the below documentation for more information
+ ## Duration Notation docs:
+ ## Refresh Interval docs:
+ refresh_interval: 5m
+
+ ##
+ ## LDAP (Authentication Provider)
+ ##
+ ldap:
+ ## The LDAP implementation, this affects elements like the attribute utilised for resetting a password.
+ implementation: custom
+ ## The url to the ldap server. Format: ://[:].
+ url: ldap://my-nas-name.local:389
+ ## The dial timeout for LDAP.
+ timeout: 5s
+ ## Use StartTLS with the LDAP connection.
+ start_tls: false
+ tls:
+ ## Server Name for certificate validation (in case it's not set correctly in the URL).
+ # server_name: ldap.domain.tld
+ ## Skip verifying the server certificate (to allow a self-signed certificate).
+ skip_verify: false
+ ## Minimum TLS version for either Secure LDAP or LDAP StartTLS.
+ minimum_version: TLS1.2
+ ## The distinguished name of the container searched for objects in the directory information tree.
+ base_dn: dc=domain,dc=tld
+ ## The attribute holding the username of the user. This attribute is used to populate the username in the session
+ username_attribute: uid
+ ## The additional_users_dn is prefixed to base_dn and delimited by a comma when searching for users.
+ additional_users_dn: cn=users
+ ## The users filter used in search queries to find the user profile based on input filled in login form.
+ users_filter: (&(|({username_attribute}={input})({mail_attribute}={input}))(objectClass=person))
+ ## The additional_groups_dn is prefixed to base_dn and delimited by a comma when searching for groups.
+ additional_groups_dn: cn=groups
+ ## The groups filter used in search queries to find the groups based on relevant authenticated user.
+ groups_filter: (&(member={dn})(objectClass=posixGroup))
+ ## The attribute holding the name of the group.
+ group_name_attribute: cn
+ ## The attribute holding the mail address of the user. If multiple email addresses are defined for a user, only the
+ mail_attribute: mail
+ ## The attribute holding the display name of the user. This will be used to greet an authenticated user.
+ display_name_attribute: displayName
+ ## Follow referrals returned by the server.
+ ## This is especially useful for environments where read-only servers exist. Only implemented for write operations.
+ permit_referrals: false
+ ## The username and password of the admin user, matching an entry of your LDAP-wrapper environment variable `LDAP_BINDUSER`.
+ user: uid=root
+ ## Password can also be set using a secret:
+ password: 1234
+```
+
+3. Save the changes to your `configuration.yml` file.
+4. Restart Authelia to apply the new configuration.
+
+Now, Authelia is configured to authenticate users against your LDAP directory through LDAP-wrapper.
diff --git a/docs/content/usage/portainer.md b/docs/content/usage/portainer.md
new file mode 100644
index 0000000..3479749
--- /dev/null
+++ b/docs/content/usage/portainer.md
@@ -0,0 +1,41 @@
+---
+title: 6.1 Portainer
+---
+
+Portainer supports LDAP authentication, allowing users to log in by authenticating against your LDAP directory. This guide outlines the steps to set up LDAP authentication over LDAP-wrapper with Portainer.
+
+{{< toc format=raw >}}
+
+## Prerequisites
+
+Before configuring LDAP authentication for Portainer, ensure the following prerequisites are met:
+
+- **LDAP-wrapper**: Make sure you have a working [LDAP-wrapper](https://github.com/ahaenggli/AzureAD-LDAP-wrapper/).
+- **Portainer**: Install and set up a working instance of [Portainer](https://docs.portainer.io/start/install-ce).
+
+## Settings for Portainer LDAP Authentication with LDAP-wrapper
+
+### LDAP Configuration
+
+- **LDAP Server**: Specify the IP or name of your NAS with Port 389.
+ Example: `192.168.1.2:389` or `my-nas-name.local:389`
+- **Reader DN**: Set it to `uid=root`, matching an entry of your LDAP-wrapper environment variable `LDAP_BINDUSER`.
+- **Password**: Set it to the password corresponding to the entry in your LDAP-wrapper environment variable `LDAP_BINDUSER`.
+
+### LDAP Security
+
+- Ensure that `StartTLS`, `Use TLS`, and `Skip verification` are set to off.
+
+### User Search Configurations
+
+- **Base DN**: Define the base DN as `cn=users,dc=domain,dc=tld`.
+- **Username Attribute**: Specify `mail`.
+- **Filter**: Use the following filter to restrict access:
+
+ ```plaintext
+ (|(&(uid=*)(memberOf=cn=users,cn=groups,dc=domain,dc=tld))(&(cn=administrators)))
+ ```
+
+ This filter ensures that only users within the administrators group can log into Portainer.
+
+Don't forget to save your LDAP-wrapper configuration. Now, users attempting to log into Portainer will be authenticated against your LDAP directory. Only users within the administrators group, as specified in the LDAP filter, will be allowed access to Portainer.
diff --git a/docs/content/usage/radius_settings_certs.png b/docs/content/usage/radius_settings_certs.png
new file mode 100644
index 0000000..c31975e
Binary files /dev/null and b/docs/content/usage/radius_settings_certs.png differ
diff --git a/docs/content/usage/radius_settings_clients.png b/docs/content/usage/radius_settings_clients.png
new file mode 100644
index 0000000..a57b489
Binary files /dev/null and b/docs/content/usage/radius_settings_clients.png differ
diff --git a/docs/content/usage/radius_settings_common.png b/docs/content/usage/radius_settings_common.png
new file mode 100644
index 0000000..7a3caa3
Binary files /dev/null and b/docs/content/usage/radius_settings_common.png differ
diff --git a/docs/content/usage/radius_unifi_profiles_detail.png b/docs/content/usage/radius_unifi_profiles_detail.png
new file mode 100644
index 0000000..0007e0f
Binary files /dev/null and b/docs/content/usage/radius_unifi_profiles_detail.png differ
diff --git a/docs/content/usage/radius_unifi_profiles_find.png b/docs/content/usage/radius_unifi_profiles_find.png
new file mode 100644
index 0000000..89f3d43
Binary files /dev/null and b/docs/content/usage/radius_unifi_profiles_find.png differ
diff --git a/docs/content/usage/radius_unifi_wlan_detail.png b/docs/content/usage/radius_unifi_wlan_detail.png
new file mode 100644
index 0000000..57ca227
Binary files /dev/null and b/docs/content/usage/radius_unifi_wlan_detail.png differ
diff --git a/docs/content/usage/radius_unifi_wlan_new.png b/docs/content/usage/radius_unifi_wlan_new.png
new file mode 100644
index 0000000..2a6c6a2
Binary files /dev/null and b/docs/content/usage/radius_unifi_wlan_new.png differ
diff --git a/docs/content/usage/synology-radius-unifi.md b/docs/content/usage/synology-radius-unifi.md
new file mode 100644
index 0000000..1316779
--- /dev/null
+++ b/docs/content/usage/synology-radius-unifi.md
@@ -0,0 +1,88 @@
+---
+title: 6.3 Synology Radius with UniFi
+---
+
+UniFi allows you to use a custom Radius server like the default package from Synology. Combined with the LDAP-wrapper, this creates a powerful setup for your users.
+
+{{< hint type=tip title="This setup was successfully tested with these versions">}}
+DSM 7.2.1-69057 Update 3
+LDAP-wrapper v2.0.2
+RADIUS Server Package 3.0.25-0515
+UniFi Network Application 8.0.24
+{{< /hint >}}
+
+{{< toc format=raw >}}
+
+## Prerequisites
+
+Before configuring Synology Radius and UniFi, ensure the following prerequisites are met:
+
+- **Synology NAS**: Ensure you are up to date with your DSM, and install the current RADIUS Server package.
+- **LDAP-wrapper**: Ensure you have a functioning [LDAP-wrapper](https://github.com/ahaenggli/AzureAD-LDAP-wrapper/).
+- **UniFi AP**: Ensure you are up to date and have access to your controller settings.
+
+## Settings in Synology RADIUS Server
+
+1. Open the RADIUS Server package on your Synology NAS.
+
+2. Configure the RADIUS `Common Settings` with the following parameters:
+
+ - **Authentication port**: Set the RADIUS Server's port number for interface protocols. The default value is 1812 for authentication.
+ - **Select network interface**: Choose the network interfaces connected to RADIUS client devices (e.g., a router). RADIUS Server provides authentication services only for access requests coming from the specified interface.
+ - **TLS/SSL profile level**: Choose "Intermediate compatibility," which is the default setting. This option is recommended because it is compatible with general-purpose browsers but is not compatible with insecure cipher suites.
+ - **Source for user authentication**: Enable LDAP users.
+
+ 
+
+3. Check your certificates.
+
+ - RADIUS Server requires a valid certificate.
+
+ 
+
+4. Configure the RADIUS `Clients` by adding clients based on the IP address range.
+
+ {{< hint type=warning title="Important Notice">}}
+ Each UniFi AP will directly contact your Synology RADIUS Server. Ensure that your firewall allows all those APs to connect to your NAS with the previously defined port (e.g., 1812).
+ {{< /hint >}}
+
+ To set up clients by IP address range:
+
+ - Click **Add** and choose **Subnet**, then enter the following information:
+
+ - **Name**: Enter a display name for the collection of clients, making it easier to identify.
+ - **IP address**: Enter the base IP addresses of the RADIUS clients (e.g., 192.168.10.1).
+ - **Subnet mask**: Enter a subnet mask, for example, 255.255.255.0.
+ - **Shared secret**: Enter a text string used as a password between the clients and RADIUS Server. This secret will also be needed in your UniFi configuration.
+
+ 
+
+## Settings in UniFi Controller
+
+1. Log in to your UniFi controller.
+2. Navigate to **Settings > Profiles > RADIUS** and create a new entry.
+
+ 
+
+ - Enable **Wired Networks**.
+ - Enable **Wireless Networks**.
+ - Enter the IP address of your Synology NAS in the **IP Address** field.
+ - Specify the RADIUS authentication port (typically 1812) in the **Port** field.
+ - Enter the same shared secret configured in the Synology RADIUS Server in the **Shared Secret** field.
+ - Disable **Accounting**.
+
+ 
+
+3. Navigate to the **Wireless Networks** section (**Settings > WiFi**) and edit your network.
+
+ 
+
+4. Edit the Wireless Network where you want to enable RADIUS authentication.
+ - Enable **WPA Enterprise**.
+ - Select the previously added RADIUS Profile.
+
+ 
+
+5. Save the settings and apply the changes to your UniFi network.
+
+Now, UniFi is configured to use the Synology RADIUS Server for authentication. Users authenticated through UniFi will be verified against your LDAP directory using LDAP-wrapper, creating a robust and secure setup.
diff --git a/docs/data/menu/main.yaml b/docs/data/menu/main.yaml
index 757f90e..965cd03 100644
--- a/docs/data/menu/main.yaml
+++ b/docs/data/menu/main.yaml
@@ -4,24 +4,24 @@ main:
ref: /
- name: 1. Installation
- ref: "/installation"
+ ref: '/installation'
sub:
- name: 1.1 Create an AzureAD application
- ref: "/installation/create-azuread-application"
+ ref: '/installation/create-azuread-application'
- name: 1.2 Run the LDAP-wrapper
- ref: "/installation/run-ldap-wrapper"
+ ref: '/installation/run-ldap-wrapper'
- name: 1.3 Use on a Synology NAS
- ref: "/installation/use-synology-nas"
+ ref: '/installation/use-synology-nas'
- name: 2. Configuration
ref: /configuration
sub:
- name: 2.1 Settings
- ref: "/configuration/settings"
+ ref: '/configuration/settings'
- name: 2.2 Bypass MFA
- ref: "/configuration/bypass-mfa"
+ ref: '/configuration/bypass-mfa'
- name: 2.3 Customize attributes
- ref: "/configuration/customize-attributes"
+ ref: '/configuration/customize-attributes'
- name: 4. Security
ref: /security
@@ -29,3 +29,12 @@ main:
- name: 5. Troubleshooting
ref: /troubleshooting
+ - name: 6. Usage examples
+ ref: /usage
+ sub:
+ - name: 6.1 Portainer
+ ref: '/usage/portainer'
+ - name: 6.2 Authelia
+ ref: '/usage/authelia'
+ - name: 6.3 Synology Radius with UniFi
+ ref: '/usage/synology-radius-unifi'
diff --git a/package-lock.json b/package-lock.json
index 10b73c7..cc3065f 100644
--- a/package-lock.json
+++ b/package-lock.json
@@ -1,32 +1,32 @@
{
"name": "AzureAD-LDAP-wrapper",
- "version": "2.0.1",
+ "version": "2.0.2",
"lockfileVersion": 3,
"requires": true,
"packages": {
"": {
"name": "AzureAD-LDAP-wrapper",
- "version": "2.0.1",
+ "version": "2.0.2",
"license": "MIT",
"dependencies": {
- "@azure/msal-node": "2.2.0",
- "axios": "~1.6.0",
+ "@azure/msal-node": "2.6.1",
+ "axios": "~1.6.5",
"diacritic": "0.0.2",
"dotenv": "^16.3.1",
"fs": "0.0.1-security",
"hashcode": "1.0.3",
"https-proxy-agent": "7.0.2",
- "ldapjs": "~3.0.5"
+ "ldapjs": "~3.0.7"
},
"devDependencies": {
- "eslint": "^8.51.0",
+ "eslint": "^8.56.0",
"eslint-config-standard": "^17.1.0",
- "eslint-plugin-import": "^2.28.1",
- "eslint-plugin-jest": "^27.4.2",
- "eslint-plugin-n": "^16.2.0",
+ "eslint-plugin-import": "^2.29.1",
+ "eslint-plugin-jest": "^27.6.2",
+ "eslint-plugin-n": "^16.6.2",
"eslint-plugin-node": "~11.1.0",
"eslint-plugin-promise": "^6.1.1",
- "eslint-plugin-security": "~1.7.1",
+ "eslint-plugin-security": "~2.1.0",
"jest": "^29.7.0"
},
"engines": {
@@ -56,33 +56,33 @@
}
},
"node_modules/@azure/msal-common": {
- "version": "14.1.0",
- "resolved": "https://registry.npmjs.org/@azure/msal-common/-/msal-common-14.1.0.tgz",
- "integrity": "sha512-xphmhcfl5VL+uq5//VKMwQn+wfEZLMKNpFCcMi8Ur8ej5UT166g6chBsxgMzc9xo9Y24R9FB3m/tjDiV03xMIA==",
+ "version": "14.6.0",
+ "resolved": "https://registry.npmjs.org/@azure/msal-common/-/msal-common-14.6.0.tgz",
+ "integrity": "sha512-AGusT/JvxdzJIYi5u0n97cmhd3pUT6UuI6rEkT5iDeT2FGcV0/EB8pk+dy6GLPpYg9vhDCuyoYrEZGd+2UeCCQ==",
"engines": {
"node": ">=0.8.0"
}
},
"node_modules/@azure/msal-node": {
- "version": "2.2.0",
- "resolved": "https://registry.npmjs.org/@azure/msal-node/-/msal-node-2.2.0.tgz",
- "integrity": "sha512-aZZ1m7OATOR9kz7+/Kl+/LZrNEj+HYaEH84XZfnBtN/9JPRazngk1XTjvAkh7W1u/O/yQrlYiiSwSAKHnNBc8A==",
+ "version": "2.6.1",
+ "resolved": "https://registry.npmjs.org/@azure/msal-node/-/msal-node-2.6.1.tgz",
+ "integrity": "sha512-wYwz83pWatTNWUCkTi3cAOXbchad5FnZz/pbZz7b8Z6FuEqohXcTtg6BLip9SmcjN6FlbwUdJIZYOof2v1Gnrg==",
"dependencies": {
- "@azure/msal-common": "14.1.0",
+ "@azure/msal-common": "14.6.0",
"jsonwebtoken": "^9.0.0",
"uuid": "^8.3.0"
},
"engines": {
- "node": "18 || 20"
+ "node": ">=16"
}
},
"node_modules/@babel/code-frame": {
- "version": "7.22.13",
- "resolved": "https://registry.npmjs.org/@babel/code-frame/-/code-frame-7.22.13.tgz",
- "integrity": "sha512-XktuhWlJ5g+3TJXc5upd9Ks1HutSArik6jf2eAjYFyIOf4ej3RN+184cZbzDvbPnuTJIUhPKKJE3cIsYTiAT3w==",
+ "version": "7.23.5",
+ "resolved": "https://registry.npmjs.org/@babel/code-frame/-/code-frame-7.23.5.tgz",
+ "integrity": "sha512-CgH3s1a96LipHCmSUmYFPwY7MNx8C3avkq7i4Wl3cfa662ldtUe4VM1TPXX70pfmrlWTb6jLqTYrZyT2ZTJBgA==",
"dev": true,
"dependencies": {
- "@babel/highlight": "^7.22.13",
+ "@babel/highlight": "^7.23.4",
"chalk": "^2.4.2"
},
"engines": {
@@ -161,30 +161,30 @@
}
},
"node_modules/@babel/compat-data": {
- "version": "7.23.2",
- "resolved": "https://registry.npmjs.org/@babel/compat-data/-/compat-data-7.23.2.tgz",
- "integrity": "sha512-0S9TQMmDHlqAZ2ITT95irXKfxN9bncq8ZCoJhun3nHL/lLUxd2NKBJYoNGWH7S0hz6fRQwWlAWn/ILM0C70KZQ==",
+ "version": "7.23.5",
+ "resolved": "https://registry.npmjs.org/@babel/compat-data/-/compat-data-7.23.5.tgz",
+ "integrity": "sha512-uU27kfDRlhfKl+w1U6vp16IuvSLtjAxdArVXPa9BvLkrr7CYIsxH5adpHObeAGY/41+syctUWOZ140a2Rvkgjw==",
"dev": true,
"engines": {
"node": ">=6.9.0"
}
},
"node_modules/@babel/core": {
- "version": "7.23.2",
- "resolved": "https://registry.npmjs.org/@babel/core/-/core-7.23.2.tgz",
- "integrity": "sha512-n7s51eWdaWZ3vGT2tD4T7J6eJs3QoBXydv7vkUM06Bf1cbVD2Kc2UrkzhiQwobfV7NwOnQXYL7UBJ5VPU+RGoQ==",
+ "version": "7.23.7",
+ "resolved": "https://registry.npmjs.org/@babel/core/-/core-7.23.7.tgz",
+ "integrity": "sha512-+UpDgowcmqe36d4NwqvKsyPMlOLNGMsfMmQ5WGCu+siCe3t3dfe9njrzGfdN4qq+bcNUt0+Vw6haRxBOycs4dw==",
"dev": true,
"dependencies": {
"@ampproject/remapping": "^2.2.0",
- "@babel/code-frame": "^7.22.13",
- "@babel/generator": "^7.23.0",
- "@babel/helper-compilation-targets": "^7.22.15",
- "@babel/helper-module-transforms": "^7.23.0",
- "@babel/helpers": "^7.23.2",
- "@babel/parser": "^7.23.0",
+ "@babel/code-frame": "^7.23.5",
+ "@babel/generator": "^7.23.6",
+ "@babel/helper-compilation-targets": "^7.23.6",
+ "@babel/helper-module-transforms": "^7.23.3",
+ "@babel/helpers": "^7.23.7",
+ "@babel/parser": "^7.23.6",
"@babel/template": "^7.22.15",
- "@babel/traverse": "^7.23.2",
- "@babel/types": "^7.23.0",
+ "@babel/traverse": "^7.23.7",
+ "@babel/types": "^7.23.6",
"convert-source-map": "^2.0.0",
"debug": "^4.1.0",
"gensync": "^1.0.0-beta.2",
@@ -200,12 +200,12 @@
}
},
"node_modules/@babel/generator": {
- "version": "7.23.0",
- "resolved": "https://registry.npmjs.org/@babel/generator/-/generator-7.23.0.tgz",
- "integrity": "sha512-lN85QRR+5IbYrMWM6Y4pE/noaQtg4pNiqeNGX60eqOfo6gtEj6uw/JagelB8vVztSd7R6M5n1+PQkDbHbBRU4g==",
+ "version": "7.23.6",
+ "resolved": "https://registry.npmjs.org/@babel/generator/-/generator-7.23.6.tgz",
+ "integrity": "sha512-qrSfCYxYQB5owCmGLbl8XRpX1ytXlpueOb0N0UmQwA073KZxejgQTzAmJezxvpwQD9uGtK2shHdi55QT+MbjIw==",
"dev": true,
"dependencies": {
- "@babel/types": "^7.23.0",
+ "@babel/types": "^7.23.6",
"@jridgewell/gen-mapping": "^0.3.2",
"@jridgewell/trace-mapping": "^0.3.17",
"jsesc": "^2.5.1"
@@ -215,14 +215,14 @@
}
},
"node_modules/@babel/helper-compilation-targets": {
- "version": "7.22.15",
- "resolved": "https://registry.npmjs.org/@babel/helper-compilation-targets/-/helper-compilation-targets-7.22.15.tgz",
- "integrity": "sha512-y6EEzULok0Qvz8yyLkCvVX+02ic+By2UdOhylwUOvOn9dvYc9mKICJuuU1n1XBI02YWsNsnrY1kc6DVbjcXbtw==",
+ "version": "7.23.6",
+ "resolved": "https://registry.npmjs.org/@babel/helper-compilation-targets/-/helper-compilation-targets-7.23.6.tgz",
+ "integrity": "sha512-9JB548GZoQVmzrFgp8o7KxdgkTGm6xs9DW0o/Pim72UDjzr5ObUQ6ZzYPqA+g9OTS2bBQoctLJrky0RDCAWRgQ==",
"dev": true,
"dependencies": {
- "@babel/compat-data": "^7.22.9",
- "@babel/helper-validator-option": "^7.22.15",
- "browserslist": "^4.21.9",
+ "@babel/compat-data": "^7.23.5",
+ "@babel/helper-validator-option": "^7.23.5",
+ "browserslist": "^4.22.2",
"lru-cache": "^5.1.1",
"semver": "^6.3.1"
},
@@ -277,9 +277,9 @@
}
},
"node_modules/@babel/helper-module-transforms": {
- "version": "7.23.0",
- "resolved": "https://registry.npmjs.org/@babel/helper-module-transforms/-/helper-module-transforms-7.23.0.tgz",
- "integrity": "sha512-WhDWw1tdrlT0gMgUJSlX0IQvoO1eN279zrAUbVB+KpV2c3Tylz8+GnKOLllCS6Z/iZQEyVYxhZVUdPTqs2YYPw==",
+ "version": "7.23.3",
+ "resolved": "https://registry.npmjs.org/@babel/helper-module-transforms/-/helper-module-transforms-7.23.3.tgz",
+ "integrity": "sha512-7bBs4ED9OmswdfDzpz4MpWgSrV7FXlc3zIagvLFjS5H+Mk7Snr21vQ6QwrsoCGMfNC4e4LQPdoULEt4ykz0SRQ==",
"dev": true,
"dependencies": {
"@babel/helper-environment-visitor": "^7.22.20",
@@ -329,9 +329,9 @@
}
},
"node_modules/@babel/helper-string-parser": {
- "version": "7.22.5",
- "resolved": "https://registry.npmjs.org/@babel/helper-string-parser/-/helper-string-parser-7.22.5.tgz",
- "integrity": "sha512-mM4COjgZox8U+JcXQwPijIZLElkgEpO5rsERVDJTc2qfCDfERyob6k5WegS14SX18IIjv+XD+GrqNumY5JRCDw==",
+ "version": "7.23.4",
+ "resolved": "https://registry.npmjs.org/@babel/helper-string-parser/-/helper-string-parser-7.23.4.tgz",
+ "integrity": "sha512-803gmbQdqwdf4olxrX4AJyFBV/RTr3rSmOj0rKwesmzlfhYNDEs+/iOcznzpNWlJlIlTJC2QfPFcHB6DlzdVLQ==",
"dev": true,
"engines": {
"node": ">=6.9.0"
@@ -347,32 +347,32 @@
}
},
"node_modules/@babel/helper-validator-option": {
- "version": "7.22.15",
- "resolved": "https://registry.npmjs.org/@babel/helper-validator-option/-/helper-validator-option-7.22.15.tgz",
- "integrity": "sha512-bMn7RmyFjY/mdECUbgn9eoSY4vqvacUnS9i9vGAGttgFWesO6B4CYWA7XlpbWgBt71iv/hfbPlynohStqnu5hA==",
+ "version": "7.23.5",
+ "resolved": "https://registry.npmjs.org/@babel/helper-validator-option/-/helper-validator-option-7.23.5.tgz",
+ "integrity": "sha512-85ttAOMLsr53VgXkTbkx8oA6YTfT4q7/HzXSLEYmjcSTJPMPQtvq1BD79Byep5xMUYbGRzEpDsjUf3dyp54IKw==",
"dev": true,
"engines": {
"node": ">=6.9.0"
}
},
"node_modules/@babel/helpers": {
- "version": "7.23.2",
- "resolved": "https://registry.npmjs.org/@babel/helpers/-/helpers-7.23.2.tgz",
- "integrity": "sha512-lzchcp8SjTSVe/fPmLwtWVBFC7+Tbn8LGHDVfDp9JGxpAY5opSaEFgt8UQvrnECWOTdji2mOWMz1rOhkHscmGQ==",
+ "version": "7.23.8",
+ "resolved": "https://registry.npmjs.org/@babel/helpers/-/helpers-7.23.8.tgz",
+ "integrity": "sha512-KDqYz4PiOWvDFrdHLPhKtCThtIcKVy6avWD2oG4GEvyQ+XDZwHD4YQd+H2vNMnq2rkdxsDkU82T+Vk8U/WXHRQ==",
"dev": true,
"dependencies": {
"@babel/template": "^7.22.15",
- "@babel/traverse": "^7.23.2",
- "@babel/types": "^7.23.0"
+ "@babel/traverse": "^7.23.7",
+ "@babel/types": "^7.23.6"
},
"engines": {
"node": ">=6.9.0"
}
},
"node_modules/@babel/highlight": {
- "version": "7.22.20",
- "resolved": "https://registry.npmjs.org/@babel/highlight/-/highlight-7.22.20.tgz",
- "integrity": "sha512-dkdMCN3py0+ksCgYmGG8jKeGA/8Tk+gJwSYYlFGxG5lmhfKNoAy004YpLxpS1W2J8m/EK2Ew+yOs9pVRwO89mg==",
+ "version": "7.23.4",
+ "resolved": "https://registry.npmjs.org/@babel/highlight/-/highlight-7.23.4.tgz",
+ "integrity": "sha512-acGdbYSfp2WheJoJm/EBBBLh/ID8KDc64ISZ9DYtBmC8/Q204PZJLHyzeB5qMzJ5trcOkybd78M4x2KWsUq++A==",
"dev": true,
"dependencies": {
"@babel/helper-validator-identifier": "^7.22.20",
@@ -455,9 +455,9 @@
}
},
"node_modules/@babel/parser": {
- "version": "7.23.0",
- "resolved": "https://registry.npmjs.org/@babel/parser/-/parser-7.23.0.tgz",
- "integrity": "sha512-vvPKKdMemU85V9WE/l5wZEmImpCtLqbnTvqDS2U1fJ96KrxoW7KrXhNsNCblQlg8Ck4b85yxdTyelsMUgFUXiw==",
+ "version": "7.23.6",
+ "resolved": "https://registry.npmjs.org/@babel/parser/-/parser-7.23.6.tgz",
+ "integrity": "sha512-Z2uID7YJ7oNvAI20O9X0bblw7Qqs8Q2hFy0R9tAfnfLkp5MW0UH9eUvnDSnFwKZ0AvgS1ucqR4KzvVHgnke1VQ==",
"dev": true,
"bin": {
"parser": "bin/babel-parser.js"
@@ -527,9 +527,9 @@
}
},
"node_modules/@babel/plugin-syntax-jsx": {
- "version": "7.22.5",
- "resolved": "https://registry.npmjs.org/@babel/plugin-syntax-jsx/-/plugin-syntax-jsx-7.22.5.tgz",
- "integrity": "sha512-gvyP4hZrgrs/wWMaocvxZ44Hw0b3W8Pe+cMxc8V1ULQ07oh8VNbIRaoD1LRZVTvD+0nieDKjfgKg89sD7rrKrg==",
+ "version": "7.23.3",
+ "resolved": "https://registry.npmjs.org/@babel/plugin-syntax-jsx/-/plugin-syntax-jsx-7.23.3.tgz",
+ "integrity": "sha512-EB2MELswq55OHUoRZLGg/zC7QWUKfNLpE57m/S2yr1uEneIgsTgrSzXP3NXEsMkVn76OlaVVnzN+ugObuYGwhg==",
"dev": true,
"dependencies": {
"@babel/helper-plugin-utils": "^7.22.5"
@@ -629,9 +629,9 @@
}
},
"node_modules/@babel/plugin-syntax-typescript": {
- "version": "7.22.5",
- "resolved": "https://registry.npmjs.org/@babel/plugin-syntax-typescript/-/plugin-syntax-typescript-7.22.5.tgz",
- "integrity": "sha512-1mS2o03i7t1c6VzH6fdQ3OA8tcEIxwG18zIPRp+UY1Ihv6W+XZzBCVxExF9upussPXJ0xE9XRHwMoNs1ep/nRQ==",
+ "version": "7.23.3",
+ "resolved": "https://registry.npmjs.org/@babel/plugin-syntax-typescript/-/plugin-syntax-typescript-7.23.3.tgz",
+ "integrity": "sha512-9EiNjVJOMwCO+43TqoTrgQ8jMwcAd0sWyXi9RPfIsLTj4R2MADDDQXELhffaUx/uJv2AYcxBgPwH6j4TIA4ytQ==",
"dev": true,
"dependencies": {
"@babel/helper-plugin-utils": "^7.22.5"
@@ -658,20 +658,20 @@
}
},
"node_modules/@babel/traverse": {
- "version": "7.23.2",
- "resolved": "https://registry.npmjs.org/@babel/traverse/-/traverse-7.23.2.tgz",
- "integrity": "sha512-azpe59SQ48qG6nu2CzcMLbxUudtN+dOM9kDbUqGq3HXUJRlo7i8fvPoxQUzYgLZ4cMVmuZgm8vvBpNeRhd6XSw==",
+ "version": "7.23.7",
+ "resolved": "https://registry.npmjs.org/@babel/traverse/-/traverse-7.23.7.tgz",
+ "integrity": "sha512-tY3mM8rH9jM0YHFGyfC0/xf+SB5eKUu7HPj7/k3fpi9dAlsMc5YbQvDi0Sh2QTPXqMhyaAtzAr807TIyfQrmyg==",
"dev": true,
"dependencies": {
- "@babel/code-frame": "^7.22.13",
- "@babel/generator": "^7.23.0",
+ "@babel/code-frame": "^7.23.5",
+ "@babel/generator": "^7.23.6",
"@babel/helper-environment-visitor": "^7.22.20",
"@babel/helper-function-name": "^7.23.0",
"@babel/helper-hoist-variables": "^7.22.5",
"@babel/helper-split-export-declaration": "^7.22.6",
- "@babel/parser": "^7.23.0",
- "@babel/types": "^7.23.0",
- "debug": "^4.1.0",
+ "@babel/parser": "^7.23.6",
+ "@babel/types": "^7.23.6",
+ "debug": "^4.3.1",
"globals": "^11.1.0"
},
"engines": {
@@ -688,12 +688,12 @@
}
},
"node_modules/@babel/types": {
- "version": "7.23.0",
- "resolved": "https://registry.npmjs.org/@babel/types/-/types-7.23.0.tgz",
- "integrity": "sha512-0oIyUfKoI3mSqMvsxBdclDwxXKXAUA8v/apZbc+iSyARYou1o8ZGDxbUYyLFoW2arqS2jDGqJuZvv1d/io1axg==",
+ "version": "7.23.6",
+ "resolved": "https://registry.npmjs.org/@babel/types/-/types-7.23.6.tgz",
+ "integrity": "sha512-+uarb83brBzPKN38NX1MkB6vb6+mwvR6amUulqAE7ccQw1pEl+bCia9TbdG1lsnFP7lZySvUn37CHyXQdfTwzg==",
"dev": true,
"dependencies": {
- "@babel/helper-string-parser": "^7.22.5",
+ "@babel/helper-string-parser": "^7.23.4",
"@babel/helper-validator-identifier": "^7.22.20",
"to-fast-properties": "^2.0.0"
},
@@ -723,18 +723,18 @@
}
},
"node_modules/@eslint-community/regexpp": {
- "version": "4.9.1",
- "resolved": "https://registry.npmjs.org/@eslint-community/regexpp/-/regexpp-4.9.1.tgz",
- "integrity": "sha512-Y27x+MBLjXa+0JWDhykM3+JE+il3kHKAEqabfEWq3SDhZjLYb6/BHL/JKFnH3fe207JaXkyDo685Oc2Glt6ifA==",
+ "version": "4.10.0",
+ "resolved": "https://registry.npmjs.org/@eslint-community/regexpp/-/regexpp-4.10.0.tgz",
+ "integrity": "sha512-Cu96Sd2By9mCNTx2iyKOmq10v22jUVQv0lQnlGNy16oE9589yE+QADPbrMGCkA51cKZSg3Pu/aTJVTGfL/qjUA==",
"dev": true,
"engines": {
"node": "^12.0.0 || ^14.0.0 || >=16.0.0"
}
},
"node_modules/@eslint/eslintrc": {
- "version": "2.1.2",
- "resolved": "https://registry.npmjs.org/@eslint/eslintrc/-/eslintrc-2.1.2.tgz",
- "integrity": "sha512-+wvgpDsrB1YqAMdEUCcnTlpfVBH7Vqn6A/NT3D8WVXFIaKMlErPIZT3oCIAVCOtarRpMtelZLqJeU3t7WY6X6g==",
+ "version": "2.1.4",
+ "resolved": "https://registry.npmjs.org/@eslint/eslintrc/-/eslintrc-2.1.4.tgz",
+ "integrity": "sha512-269Z39MS6wVJtsoUl10L60WdkhJVdPG24Q4eZTH3nnF6lpvSShEK3wQjDX9JRWAUPvPh7COouPpU9IrqaZFvtQ==",
"dev": true,
"dependencies": {
"ajv": "^6.12.4",
@@ -755,22 +755,22 @@
}
},
"node_modules/@eslint/js": {
- "version": "8.51.0",
- "resolved": "https://registry.npmjs.org/@eslint/js/-/js-8.51.0.tgz",
- "integrity": "sha512-HxjQ8Qn+4SI3/AFv6sOrDB+g6PpUTDwSJiQqOrnneEk8L71161srI9gjzzZvYVbzHiVg/BvcH95+cK/zfIt4pg==",
+ "version": "8.56.0",
+ "resolved": "https://registry.npmjs.org/@eslint/js/-/js-8.56.0.tgz",
+ "integrity": "sha512-gMsVel9D7f2HLkBma9VbtzZRehRogVRfbr++f06nL2vnCGCNlzOD+/MUov/F4p8myyAHspEhVobgjpX64q5m6A==",
"dev": true,
"engines": {
"node": "^12.22.0 || ^14.17.0 || >=16.0.0"
}
},
"node_modules/@humanwhocodes/config-array": {
- "version": "0.11.12",
- "resolved": "https://registry.npmjs.org/@humanwhocodes/config-array/-/config-array-0.11.12.tgz",
- "integrity": "sha512-NlGesA1usRNn6ctHCZ21M4/dKPgW9Nn1FypRdIKKgZOKzkVV4T1FlK5mBiLhHBCDmEbdQG0idrcXlbZfksJ+RA==",
+ "version": "0.11.14",
+ "resolved": "https://registry.npmjs.org/@humanwhocodes/config-array/-/config-array-0.11.14.tgz",
+ "integrity": "sha512-3T8LkOmg45BV5FICb15QQMsyUSWrQ8AygVfC7ZG32zOalnqrilm018ZVCw0eapXux8FtA33q8PSRSstjee3jSg==",
"dev": true,
"dependencies": {
- "@humanwhocodes/object-schema": "^2.0.0",
- "debug": "^4.1.1",
+ "@humanwhocodes/object-schema": "^2.0.2",
+ "debug": "^4.3.1",
"minimatch": "^3.0.5"
},
"engines": {
@@ -791,9 +791,9 @@
}
},
"node_modules/@humanwhocodes/object-schema": {
- "version": "2.0.0",
- "resolved": "https://registry.npmjs.org/@humanwhocodes/object-schema/-/object-schema-2.0.0.tgz",
- "integrity": "sha512-9S9QrXY2K0L4AGDcSgTi9vgiCcG8VcBv4Mp7/1hDPYoswIy6Z6KO5blYto82BT8M0MZNRWmCFLpCs3HlpYGGdw==",
+ "version": "2.0.2",
+ "resolved": "https://registry.npmjs.org/@humanwhocodes/object-schema/-/object-schema-2.0.2.tgz",
+ "integrity": "sha512-6EwiSjwWYP7pTckG6I5eyFANjPhmPjUX9JRLUSfNPC7FX7zK9gyZAfUEaECL6ALTpGX5AjnBq3C9XmVWPitNpw==",
"dev": true
},
"node_modules/@istanbuljs/load-nyc-config": {
@@ -1255,9 +1255,9 @@
}
},
"node_modules/@ldapjs/controls": {
- "version": "2.0.0",
- "resolved": "https://registry.npmjs.org/@ldapjs/controls/-/controls-2.0.0.tgz",
- "integrity": "sha512-NpFmdIc2q83tYRGR2a3NDulKgU1e4YOgqjQmmMezCoN4Xz0tju4yB4eibQNC+Zg8YRW06KPwFPKbebDaCqFF0w==",
+ "version": "2.1.0",
+ "resolved": "https://registry.npmjs.org/@ldapjs/controls/-/controls-2.1.0.tgz",
+ "integrity": "sha512-2pFdD1yRC9V9hXfAWvCCO2RRWK9OdIEcJIos/9cCVP9O4k72BY1bLDQQ4KpUoJnl4y/JoD4iFgM+YWT3IfITWw==",
"dependencies": {
"@ldapjs/asn1": "^1.2.0",
"@ldapjs/protocol": "^1.2.1"
@@ -1288,17 +1288,17 @@
}
},
"node_modules/@ldapjs/messages": {
- "version": "1.2.1",
- "resolved": "https://registry.npmjs.org/@ldapjs/messages/-/messages-1.2.1.tgz",
- "integrity": "sha512-QPeDcwEJmYou6QxPZqr2VibJlrZkb+qSjwxmFJgfss2Hz9wTncgs27CDloD5vOQlE65fUnhEKlzuzMi1a4oxUQ==",
+ "version": "1.3.0",
+ "resolved": "https://registry.npmjs.org/@ldapjs/messages/-/messages-1.3.0.tgz",
+ "integrity": "sha512-K7xZpXJ21bj92jS35wtRbdcNrwmxAtPwy4myeh9duy/eR3xQKvikVycbdWVzkYEAVE5Ce520VXNOwCHjomjCZw==",
"dependencies": {
- "@ldapjs/asn1": "2.0.0",
- "@ldapjs/attribute": "1.0.0",
- "@ldapjs/change": "1.0.0",
- "@ldapjs/controls": "2.0.0",
+ "@ldapjs/asn1": "^2.0.0",
+ "@ldapjs/attribute": "^1.0.0",
+ "@ldapjs/change": "^1.0.0",
+ "@ldapjs/controls": "^2.1.0",
"@ldapjs/dn": "^1.1.0",
"@ldapjs/filter": "^2.1.1",
- "@ldapjs/protocol": "1.2.1",
+ "@ldapjs/protocol": "^1.2.1",
"process-warning": "^2.2.0"
}
},
@@ -1367,9 +1367,9 @@
}
},
"node_modules/@types/babel__core": {
- "version": "7.20.3",
- "resolved": "https://registry.npmjs.org/@types/babel__core/-/babel__core-7.20.3.tgz",
- "integrity": "sha512-54fjTSeSHwfan8AyHWrKbfBWiEUrNTZsUwPTDSNaaP1QDQIZbeNUg3a59E9D+375MzUw/x1vx2/0F5LBz+AeYA==",
+ "version": "7.20.5",
+ "resolved": "https://registry.npmjs.org/@types/babel__core/-/babel__core-7.20.5.tgz",
+ "integrity": "sha512-qoQprZvz5wQFJwMDqeseRXWv3rqMvhgpbXFfVyWhbx9X47POIA6i/+dXefEmZKoAgOaTdaIgNSMqMIU61yRyzA==",
"dev": true,
"dependencies": {
"@babel/parser": "^7.20.7",
@@ -1380,18 +1380,18 @@
}
},
"node_modules/@types/babel__generator": {
- "version": "7.6.6",
- "resolved": "https://registry.npmjs.org/@types/babel__generator/-/babel__generator-7.6.6.tgz",
- "integrity": "sha512-66BXMKb/sUWbMdBNdMvajU7i/44RkrA3z/Yt1c7R5xejt8qh84iU54yUWCtm0QwGJlDcf/gg4zd/x4mpLAlb/w==",
+ "version": "7.6.8",
+ "resolved": "https://registry.npmjs.org/@types/babel__generator/-/babel__generator-7.6.8.tgz",
+ "integrity": "sha512-ASsj+tpEDsEiFr1arWrlN6V3mdfjRMZt6LtK/Vp/kreFLnr5QH5+DhvD5nINYZXzwJvXeGq+05iUXcAzVrqWtw==",
"dev": true,
"dependencies": {
"@babel/types": "^7.0.0"
}
},
"node_modules/@types/babel__template": {
- "version": "7.4.3",
- "resolved": "https://registry.npmjs.org/@types/babel__template/-/babel__template-7.4.3.tgz",
- "integrity": "sha512-ciwyCLeuRfxboZ4isgdNZi/tkt06m8Tw6uGbBSBgWrnnZGNXiEyM27xc/PjXGQLqlZ6ylbgHMnm7ccF9tCkOeQ==",
+ "version": "7.4.4",
+ "resolved": "https://registry.npmjs.org/@types/babel__template/-/babel__template-7.4.4.tgz",
+ "integrity": "sha512-h/NUaSyG5EyxBIp8YRxo4RMe2/qQgvyowRwVMzhYhBCONbW8PUsg4lkFMrhgZhUe5z3L3MiLDuvyJ/CaPa2A8A==",
"dev": true,
"dependencies": {
"@babel/parser": "^7.1.0",
@@ -1399,51 +1399,51 @@
}
},
"node_modules/@types/babel__traverse": {
- "version": "7.20.3",
- "resolved": "https://registry.npmjs.org/@types/babel__traverse/-/babel__traverse-7.20.3.tgz",
- "integrity": "sha512-Lsh766rGEFbaxMIDH7Qa+Yha8cMVI3qAK6CHt3OR0YfxOIn5Z54iHiyDRycHrBqeIiqGa20Kpsv1cavfBKkRSw==",
+ "version": "7.20.5",
+ "resolved": "https://registry.npmjs.org/@types/babel__traverse/-/babel__traverse-7.20.5.tgz",
+ "integrity": "sha512-WXCyOcRtH37HAUkpXhUduaxdm82b4GSlyTqajXviN4EfiuPgNYR109xMCKvpl6zPIpua0DGlMEDCq+g8EdoheQ==",
"dev": true,
"dependencies": {
"@babel/types": "^7.20.7"
}
},
"node_modules/@types/graceful-fs": {
- "version": "4.1.8",
- "resolved": "https://registry.npmjs.org/@types/graceful-fs/-/graceful-fs-4.1.8.tgz",
- "integrity": "sha512-NhRH7YzWq8WiNKVavKPBmtLYZHxNY19Hh+az28O/phfp68CF45pMFud+ZzJ8ewnxnC5smIdF3dqFeiSUQ5I+pw==",
+ "version": "4.1.9",
+ "resolved": "https://registry.npmjs.org/@types/graceful-fs/-/graceful-fs-4.1.9.tgz",
+ "integrity": "sha512-olP3sd1qOEe5dXTSaFvQG+02VdRXcdytWLAZsAq1PecU8uqQAhkrnbli7DagjtXKW/Bl7YJbUsa8MPcuc8LHEQ==",
"dev": true,
"dependencies": {
"@types/node": "*"
}
},
"node_modules/@types/istanbul-lib-coverage": {
- "version": "2.0.5",
- "resolved": "https://registry.npmjs.org/@types/istanbul-lib-coverage/-/istanbul-lib-coverage-2.0.5.tgz",
- "integrity": "sha512-zONci81DZYCZjiLe0r6equvZut0b+dBRPBN5kBDjsONnutYNtJMoWQ9uR2RkL1gLG9NMTzvf+29e5RFfPbeKhQ==",
+ "version": "2.0.6",
+ "resolved": "https://registry.npmjs.org/@types/istanbul-lib-coverage/-/istanbul-lib-coverage-2.0.6.tgz",
+ "integrity": "sha512-2QF/t/auWm0lsy8XtKVPG19v3sSOQlJe/YHZgfjb/KBBHOGSV+J2q/S671rcq9uTBrLAXmZpqJiaQbMT+zNU1w==",
"dev": true
},
"node_modules/@types/istanbul-lib-report": {
- "version": "3.0.2",
- "resolved": "https://registry.npmjs.org/@types/istanbul-lib-report/-/istanbul-lib-report-3.0.2.tgz",
- "integrity": "sha512-8toY6FgdltSdONav1XtUHl4LN1yTmLza+EuDazb/fEmRNCwjyqNVIQWs2IfC74IqjHkREs/nQ2FWq5kZU9IC0w==",
+ "version": "3.0.3",
+ "resolved": "https://registry.npmjs.org/@types/istanbul-lib-report/-/istanbul-lib-report-3.0.3.tgz",
+ "integrity": "sha512-NQn7AHQnk/RSLOxrBbGyJM/aVQ+pjj5HCgasFxc0K/KhoATfQ/47AyUl15I2yBUpihjmas+a+VJBOqecrFH+uA==",
"dev": true,
"dependencies": {
"@types/istanbul-lib-coverage": "*"
}
},
"node_modules/@types/istanbul-reports": {
- "version": "3.0.3",
- "resolved": "https://registry.npmjs.org/@types/istanbul-reports/-/istanbul-reports-3.0.3.tgz",
- "integrity": "sha512-1nESsePMBlf0RPRffLZi5ujYh7IH1BWL4y9pr+Bn3cJBdxz+RTP8bUFljLz9HvzhhOSWKdyBZ4DIivdL6rvgZg==",
+ "version": "3.0.4",
+ "resolved": "https://registry.npmjs.org/@types/istanbul-reports/-/istanbul-reports-3.0.4.tgz",
+ "integrity": "sha512-pk2B1NWalF9toCRu6gjBzR69syFjP4Od8WRAX+0mmf9lAjCRicLOWc+ZrxZHx/0XRjotgkF9t6iaMJ+aXcOdZQ==",
"dev": true,
"dependencies": {
"@types/istanbul-lib-report": "*"
}
},
"node_modules/@types/json-schema": {
- "version": "7.0.14",
- "resolved": "https://registry.npmjs.org/@types/json-schema/-/json-schema-7.0.14.tgz",
- "integrity": "sha512-U3PUjAudAdJBeC2pgN8uTIKgxrb4nlDF3SF0++EldXQvQBGkpFZMSnwQiIoDU77tv45VgNkl/L4ouD+rEomujw==",
+ "version": "7.0.15",
+ "resolved": "https://registry.npmjs.org/@types/json-schema/-/json-schema-7.0.15.tgz",
+ "integrity": "sha512-5+fP8P8MFNC+AyZCDxrB2pkZFPGzqQWUzpSeuuVLvm8VMcorNYavBqoFcxK8bQz4Qsbn4oUEEem4wDLfcysGHA==",
"dev": true
},
"node_modules/@types/json5": {
@@ -1453,39 +1453,39 @@
"dev": true
},
"node_modules/@types/node": {
- "version": "20.8.7",
- "resolved": "https://registry.npmjs.org/@types/node/-/node-20.8.7.tgz",
- "integrity": "sha512-21TKHHh3eUHIi2MloeptJWALuCu5H7HQTdTrWIFReA8ad+aggoX+lRes3ex7/FtpC+sVUpFMQ+QTfYr74mruiQ==",
+ "version": "20.11.0",
+ "resolved": "https://registry.npmjs.org/@types/node/-/node-20.11.0.tgz",
+ "integrity": "sha512-o9bjXmDNcF7GbM4CNQpmi+TutCgap/K3w1JyKgxAjqx41zp9qlIAVFi0IhCNsJcXolEqLWhbFbEeL0PvYm4pcQ==",
"dev": true,
"dependencies": {
- "undici-types": "~5.25.1"
+ "undici-types": "~5.26.4"
}
},
"node_modules/@types/semver": {
- "version": "7.5.4",
- "resolved": "https://registry.npmjs.org/@types/semver/-/semver-7.5.4.tgz",
- "integrity": "sha512-MMzuxN3GdFwskAnb6fz0orFvhfqi752yjaXylr0Rp4oDg5H0Zn1IuyRhDVvYOwAXoJirx2xuS16I3WjxnAIHiQ==",
+ "version": "7.5.6",
+ "resolved": "https://registry.npmjs.org/@types/semver/-/semver-7.5.6.tgz",
+ "integrity": "sha512-dn1l8LaMea/IjDoHNd9J52uBbInB796CDffS6VdIxvqYCPSG0V0DzHp76GpaWnlhg88uYyPbXCDIowa86ybd5A==",
"dev": true
},
"node_modules/@types/stack-utils": {
- "version": "2.0.2",
- "resolved": "https://registry.npmjs.org/@types/stack-utils/-/stack-utils-2.0.2.tgz",
- "integrity": "sha512-g7CK9nHdwjK2n0ymT2CW698FuWJRIx+RP6embAzZ2Qi8/ilIrA1Imt2LVSeHUzKvpoi7BhmmQcXz95eS0f2JXw==",
+ "version": "2.0.3",
+ "resolved": "https://registry.npmjs.org/@types/stack-utils/-/stack-utils-2.0.3.tgz",
+ "integrity": "sha512-9aEbYZ3TbYMznPdcdr3SmIrLXwC/AKZXQeCf9Pgao5CKb8CyHuEX5jzWPTkvregvhRJHcpRO6BFoGW9ycaOkYw==",
"dev": true
},
"node_modules/@types/yargs": {
- "version": "17.0.29",
- "resolved": "https://registry.npmjs.org/@types/yargs/-/yargs-17.0.29.tgz",
- "integrity": "sha512-nacjqA3ee9zRF/++a3FUY1suHTFKZeHba2n8WeDw9cCVdmzmHpIxyzOJBcpHvvEmS8E9KqWlSnWHUkOrkhWcvA==",
+ "version": "17.0.32",
+ "resolved": "https://registry.npmjs.org/@types/yargs/-/yargs-17.0.32.tgz",
+ "integrity": "sha512-xQ67Yc/laOG5uMfX/093MRlGGCIBzZMarVa+gfNKJxWAIgykYpVGkBdbqEzGDDfCrVUj6Hiff4mTZ5BA6TmAog==",
"dev": true,
"dependencies": {
"@types/yargs-parser": "*"
}
},
"node_modules/@types/yargs-parser": {
- "version": "21.0.2",
- "resolved": "https://registry.npmjs.org/@types/yargs-parser/-/yargs-parser-21.0.2.tgz",
- "integrity": "sha512-5qcvofLPbfjmBfKaLfj/+f+Sbd6pN4zl7w7VSVI5uz7m9QZTuB2aZAa2uo1wHFBNN2x6g/SoTkXmd8mQnQF2Cw==",
+ "version": "21.0.3",
+ "resolved": "https://registry.npmjs.org/@types/yargs-parser/-/yargs-parser-21.0.3.tgz",
+ "integrity": "sha512-I4q9QU9MQv4oEOz4tAHJtNz1cwuLxn2F3xcc2iV5WdqLPpUnj30aUuxt1mAxYTG+oe8CZMV/+6rU4S4gRDzqtQ==",
"dev": true
},
"node_modules/@typescript-eslint/scope-manager": {
@@ -1676,15 +1676,21 @@
"url": "https://opencollective.com/typescript-eslint"
}
},
+ "node_modules/@ungap/structured-clone": {
+ "version": "1.2.0",
+ "resolved": "https://registry.npmjs.org/@ungap/structured-clone/-/structured-clone-1.2.0.tgz",
+ "integrity": "sha512-zuVdFrMJiuCDQUMCzQaD6KL28MjnqqN8XnAqiEq9PNm/hCPTSGfrXCOfwj1ow4LFb/tNymJPwsNbVePc1xFqrQ==",
+ "dev": true
+ },
"node_modules/abstract-logging": {
"version": "2.0.1",
"resolved": "https://registry.npmjs.org/abstract-logging/-/abstract-logging-2.0.1.tgz",
"integrity": "sha512-2BjRTZxTPvheOvGbBslFSYOUkr+SjPtOnrLP33f+VIWLzezQpZcqVg7ja3L4dBXmzzgwT+a029jRx5PCi3JuiA=="
},
"node_modules/acorn": {
- "version": "8.10.0",
- "resolved": "https://registry.npmjs.org/acorn/-/acorn-8.10.0.tgz",
- "integrity": "sha512-F0SAmZ8iUtS//m8DmCTA0jlh6TDKkHQyK6xc6V4KDTyZKA9dnvX9/3sRTVQrWm79glUAZbnmmNcdYwUIHWVybw==",
+ "version": "8.11.3",
+ "resolved": "https://registry.npmjs.org/acorn/-/acorn-8.11.3.tgz",
+ "integrity": "sha512-Y9rRfJG5jcKOE0CLisYbojUjIrIEE7AGMzA/Sm4BslANhbS+cDMpgBdcPT91oJ7OuJ9hYJBx59RjbhxVnrF8Xg==",
"dev": true,
"bin": {
"acorn": "bin/acorn"
@@ -1942,11 +1948,11 @@
}
},
"node_modules/axios": {
- "version": "1.6.0",
- "resolved": "https://registry.npmjs.org/axios/-/axios-1.6.0.tgz",
- "integrity": "sha512-EZ1DYihju9pwVB+jg67ogm+Tmqc6JmhamRN6I4Zt8DfZu5lbcQGw3ozH9lFejSJgs/ibaef3A9PMXPLeefFGJg==",
+ "version": "1.6.5",
+ "resolved": "https://registry.npmjs.org/axios/-/axios-1.6.5.tgz",
+ "integrity": "sha512-Ii012v05KEVuUoFWmMW/UQv9aRIc3ZwkWDcM+h5Il8izZCtRVpDUfwpoFf7eOtajT3QiGR4yDUx7lPqHJULgbg==",
"dependencies": {
- "follow-redirects": "^1.15.0",
+ "follow-redirects": "^1.15.4",
"form-data": "^4.0.0",
"proxy-from-env": "^1.1.0"
}
@@ -2098,9 +2104,9 @@
}
},
"node_modules/browserslist": {
- "version": "4.22.1",
- "resolved": "https://registry.npmjs.org/browserslist/-/browserslist-4.22.1.tgz",
- "integrity": "sha512-FEVc202+2iuClEhZhrWy6ZiAcRLvNMyYcxZ8raemul1DYVOVdFsbqckWLdsixQZCpJlwe77Z3UTalE7jsjnKfQ==",
+ "version": "4.22.2",
+ "resolved": "https://registry.npmjs.org/browserslist/-/browserslist-4.22.2.tgz",
+ "integrity": "sha512-0UgcrvQmBDvZHFGdYUehrCNIazki7/lUP3kkoi/r3YB2amZbFM9J43ZRkJTXBUZK4gmx56+Sqk9+Vs9mwZx9+A==",
"dev": true,
"funding": [
{
@@ -2117,9 +2123,9 @@
}
],
"dependencies": {
- "caniuse-lite": "^1.0.30001541",
- "electron-to-chromium": "^1.4.535",
- "node-releases": "^2.0.13",
+ "caniuse-lite": "^1.0.30001565",
+ "electron-to-chromium": "^1.4.601",
+ "node-releases": "^2.0.14",
"update-browserslist-db": "^1.0.13"
},
"bin": {
@@ -2149,6 +2155,18 @@
"integrity": "sha512-E+XQCRwSbaaiChtv6k6Dwgc+bx+Bs6vuKJHHl5kox/BaKbhiXzqQOwK4cO22yElGp2OCmjwVhT3HmxgyPGnJfQ==",
"dev": true
},
+ "node_modules/builtin-modules": {
+ "version": "3.3.0",
+ "resolved": "https://registry.npmjs.org/builtin-modules/-/builtin-modules-3.3.0.tgz",
+ "integrity": "sha512-zhaCDicdLuWN5UbN5IMnFqNMhNfo919sH85y2/ea+5Yg9TsTkeZxpL+JLbp6cgYFS4sRLp3YV4S6yDuqVWHYOw==",
+ "dev": true,
+ "engines": {
+ "node": ">=6"
+ },
+ "funding": {
+ "url": "https://github.com/sponsors/sindresorhus"
+ }
+ },
"node_modules/builtins": {
"version": "5.0.1",
"resolved": "https://registry.npmjs.org/builtins/-/builtins-5.0.1.tgz",
@@ -2224,9 +2242,9 @@
}
},
"node_modules/caniuse-lite": {
- "version": "1.0.30001551",
- "resolved": "https://registry.npmjs.org/caniuse-lite/-/caniuse-lite-1.0.30001551.tgz",
- "integrity": "sha512-vtBAez47BoGMMzlbYhfXrMV1kvRF2WP/lqiMuDu1Sb4EE4LKEgjopFDSRtZfdVnslNRpOqV/woE+Xgrwj6VQlg==",
+ "version": "1.0.30001576",
+ "resolved": "https://registry.npmjs.org/caniuse-lite/-/caniuse-lite-1.0.30001576.tgz",
+ "integrity": "sha512-ff5BdakGe2P3SQsMsiqmt1Lc8221NR1VzHj5jXN5vBny9A6fpze94HiVV/n7XRosOlsShJcvMv5mdnpjOGCEgg==",
"dev": true,
"funding": [
{
@@ -2551,9 +2569,9 @@
}
},
"node_modules/electron-to-chromium": {
- "version": "1.4.561",
- "resolved": "https://registry.npmjs.org/electron-to-chromium/-/electron-to-chromium-1.4.561.tgz",
- "integrity": "sha512-eS5t4ulWOBfVHdq9SW2dxEaFarj1lPjvJ8PaYMOjY0DecBaj/t4ARziL2IPpDr4atyWwjLFGQ2vo/VCgQFezVQ==",
+ "version": "1.4.628",
+ "resolved": "https://registry.npmjs.org/electron-to-chromium/-/electron-to-chromium-1.4.628.tgz",
+ "integrity": "sha512-2k7t5PHvLsufpP6Zwk0nof62yLOsCf032wZx7/q0mv8gwlXjhcxI3lz6f0jBr0GrnWKcm3burXzI3t5IrcdUxw==",
"dev": true
},
"node_modules/emittery": {
@@ -2584,26 +2602,26 @@
}
},
"node_modules/es-abstract": {
- "version": "1.22.2",
- "resolved": "https://registry.npmjs.org/es-abstract/-/es-abstract-1.22.2.tgz",
- "integrity": "sha512-YoxfFcDmhjOgWPWsV13+2RNjq1F6UQnfs+8TftwNqtzlmFzEXvlUwdrNrYeaizfjQzRMxkZ6ElWMOJIFKdVqwA==",
+ "version": "1.22.3",
+ "resolved": "https://registry.npmjs.org/es-abstract/-/es-abstract-1.22.3.tgz",
+ "integrity": "sha512-eiiY8HQeYfYH2Con2berK+To6GrK2RxbPawDkGq4UiCQQfZHb6wX9qQqkbpPqaxQFcl8d9QzZqo0tGE0VcrdwA==",
"dev": true,
"dependencies": {
"array-buffer-byte-length": "^1.0.0",
"arraybuffer.prototype.slice": "^1.0.2",
"available-typed-arrays": "^1.0.5",
- "call-bind": "^1.0.2",
+ "call-bind": "^1.0.5",
"es-set-tostringtag": "^2.0.1",
"es-to-primitive": "^1.2.1",
"function.prototype.name": "^1.1.6",
- "get-intrinsic": "^1.2.1",
+ "get-intrinsic": "^1.2.2",
"get-symbol-description": "^1.0.0",
"globalthis": "^1.0.3",
"gopd": "^1.0.1",
- "has": "^1.0.3",
"has-property-descriptors": "^1.0.0",
"has-proto": "^1.0.1",
"has-symbols": "^1.0.3",
+ "hasown": "^2.0.0",
"internal-slot": "^1.0.5",
"is-array-buffer": "^3.0.2",
"is-callable": "^1.2.7",
@@ -2613,7 +2631,7 @@
"is-string": "^1.0.7",
"is-typed-array": "^1.1.12",
"is-weakref": "^1.0.2",
- "object-inspect": "^1.12.3",
+ "object-inspect": "^1.13.1",
"object-keys": "^1.1.1",
"object.assign": "^4.1.4",
"regexp.prototype.flags": "^1.5.1",
@@ -2627,7 +2645,7 @@
"typed-array-byte-offset": "^1.0.0",
"typed-array-length": "^1.0.4",
"unbox-primitive": "^1.0.2",
- "which-typed-array": "^1.1.11"
+ "which-typed-array": "^1.1.13"
},
"engines": {
"node": ">= 0.4"
@@ -2637,26 +2655,26 @@
}
},
"node_modules/es-set-tostringtag": {
- "version": "2.0.1",
- "resolved": "https://registry.npmjs.org/es-set-tostringtag/-/es-set-tostringtag-2.0.1.tgz",
- "integrity": "sha512-g3OMbtlwY3QewlqAiMLI47KywjWZoEytKr8pf6iTC8uJq5bIAH52Z9pnQ8pVL6whrCto53JZDuUIsifGeLorTg==",
+ "version": "2.0.2",
+ "resolved": "https://registry.npmjs.org/es-set-tostringtag/-/es-set-tostringtag-2.0.2.tgz",
+ "integrity": "sha512-BuDyupZt65P9D2D2vA/zqcI3G5xRsklm5N3xCwuiy+/vKy8i0ifdsQP1sLgO4tZDSCaQUSnmC48khknGMV3D2Q==",
"dev": true,
"dependencies": {
- "get-intrinsic": "^1.1.3",
- "has": "^1.0.3",
- "has-tostringtag": "^1.0.0"
+ "get-intrinsic": "^1.2.2",
+ "has-tostringtag": "^1.0.0",
+ "hasown": "^2.0.0"
},
"engines": {
"node": ">= 0.4"
}
},
"node_modules/es-shim-unscopables": {
- "version": "1.0.0",
- "resolved": "https://registry.npmjs.org/es-shim-unscopables/-/es-shim-unscopables-1.0.0.tgz",
- "integrity": "sha512-Jm6GPcCdC30eMLbZ2x8z2WuRwAws3zTBBKuusffYVUrNj/GVSUAZ+xKMaUpfNDR5IbyNA5LJbaecoUVbmUcB1w==",
+ "version": "1.0.2",
+ "resolved": "https://registry.npmjs.org/es-shim-unscopables/-/es-shim-unscopables-1.0.2.tgz",
+ "integrity": "sha512-J3yBRXCzDu4ULnQwxyToo/OjdMx6akgVC7K6few0a7F/0wLtmKKN7I73AH5T2836UuXRqN7Qg+IIUw/+YJksRw==",
"dev": true,
"dependencies": {
- "has": "^1.0.3"
+ "hasown": "^2.0.0"
}
},
"node_modules/es-to-primitive": {
@@ -2698,18 +2716,19 @@
}
},
"node_modules/eslint": {
- "version": "8.51.0",
- "resolved": "https://registry.npmjs.org/eslint/-/eslint-8.51.0.tgz",
- "integrity": "sha512-2WuxRZBrlwnXi+/vFSJyjMqrNjtJqiasMzehF0shoLaW7DzS3/9Yvrmq5JiT66+pNjiX4UBnLDiKHcWAr/OInA==",
+ "version": "8.56.0",
+ "resolved": "https://registry.npmjs.org/eslint/-/eslint-8.56.0.tgz",
+ "integrity": "sha512-Go19xM6T9puCOWntie1/P997aXxFsOi37JIHRWI514Hc6ZnaHGKY9xFhrU65RT6CcBEzZoGG1e6Nq+DT04ZtZQ==",
"dev": true,
"dependencies": {
"@eslint-community/eslint-utils": "^4.2.0",
"@eslint-community/regexpp": "^4.6.1",
- "@eslint/eslintrc": "^2.1.2",
- "@eslint/js": "8.51.0",
- "@humanwhocodes/config-array": "^0.11.11",
+ "@eslint/eslintrc": "^2.1.4",
+ "@eslint/js": "8.56.0",
+ "@humanwhocodes/config-array": "^0.11.13",
"@humanwhocodes/module-importer": "^1.0.1",
"@nodelib/fs.walk": "^1.2.8",
+ "@ungap/structured-clone": "^1.2.0",
"ajv": "^6.12.4",
"chalk": "^4.0.0",
"cross-spawn": "^7.0.2",
@@ -2751,6 +2770,18 @@
"url": "https://opencollective.com/eslint"
}
},
+ "node_modules/eslint-compat-utils": {
+ "version": "0.1.2",
+ "resolved": "https://registry.npmjs.org/eslint-compat-utils/-/eslint-compat-utils-0.1.2.tgz",
+ "integrity": "sha512-Jia4JDldWnFNIru1Ehx1H5s9/yxiRHY/TimCuUc0jNexew3cF1gI6CYZil1ociakfWO3rRqFjl1mskBblB3RYg==",
+ "dev": true,
+ "engines": {
+ "node": ">=12"
+ },
+ "peerDependencies": {
+ "eslint": ">=6.0.0"
+ }
+ },
"node_modules/eslint-config-standard": {
"version": "17.1.0",
"resolved": "https://registry.npmjs.org/eslint-config-standard/-/eslint-config-standard-17.1.0.tgz",
@@ -2846,13 +2877,14 @@
}
},
"node_modules/eslint-plugin-es-x": {
- "version": "7.2.0",
- "resolved": "https://registry.npmjs.org/eslint-plugin-es-x/-/eslint-plugin-es-x-7.2.0.tgz",
- "integrity": "sha512-9dvv5CcvNjSJPqnS5uZkqb3xmbeqRLnvXKK7iI5+oK/yTusyc46zbBZKENGsOfojm/mKfszyZb+wNqNPAPeGXA==",
+ "version": "7.5.0",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-es-x/-/eslint-plugin-es-x-7.5.0.tgz",
+ "integrity": "sha512-ODswlDSO0HJDzXU0XvgZ3lF3lS3XAZEossh15Q2UHjwrJggWeBoKqqEsLTZLXl+dh5eOAozG0zRcYtuE35oTuQ==",
"dev": true,
"dependencies": {
"@eslint-community/eslint-utils": "^4.1.2",
- "@eslint-community/regexpp": "^4.6.0"
+ "@eslint-community/regexpp": "^4.6.0",
+ "eslint-compat-utils": "^0.1.2"
},
"engines": {
"node": "^14.18.0 || >=16.0.0"
@@ -2865,28 +2897,28 @@
}
},
"node_modules/eslint-plugin-import": {
- "version": "2.28.1",
- "resolved": "https://registry.npmjs.org/eslint-plugin-import/-/eslint-plugin-import-2.28.1.tgz",
- "integrity": "sha512-9I9hFlITvOV55alzoKBI+K9q74kv0iKMeY6av5+umsNwayt59fz692daGyjR+oStBQgx6nwR9rXldDev3Clw+A==",
+ "version": "2.29.1",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-import/-/eslint-plugin-import-2.29.1.tgz",
+ "integrity": "sha512-BbPC0cuExzhiMo4Ff1BTVwHpjjv28C5R+btTOGaCRC7UEz801up0JadwkeSk5Ued6TG34uaczuVuH6qyy5YUxw==",
"dev": true,
"dependencies": {
- "array-includes": "^3.1.6",
- "array.prototype.findlastindex": "^1.2.2",
- "array.prototype.flat": "^1.3.1",
- "array.prototype.flatmap": "^1.3.1",
+ "array-includes": "^3.1.7",
+ "array.prototype.findlastindex": "^1.2.3",
+ "array.prototype.flat": "^1.3.2",
+ "array.prototype.flatmap": "^1.3.2",
"debug": "^3.2.7",
"doctrine": "^2.1.0",
- "eslint-import-resolver-node": "^0.3.7",
+ "eslint-import-resolver-node": "^0.3.9",
"eslint-module-utils": "^2.8.0",
- "has": "^1.0.3",
- "is-core-module": "^2.13.0",
+ "hasown": "^2.0.0",
+ "is-core-module": "^2.13.1",
"is-glob": "^4.0.3",
"minimatch": "^3.1.2",
- "object.fromentries": "^2.0.6",
- "object.groupby": "^1.0.0",
- "object.values": "^1.1.6",
+ "object.fromentries": "^2.0.7",
+ "object.groupby": "^1.0.1",
+ "object.values": "^1.1.7",
"semver": "^6.3.1",
- "tsconfig-paths": "^3.14.2"
+ "tsconfig-paths": "^3.15.0"
},
"engines": {
"node": ">=4"
@@ -2917,9 +2949,9 @@
}
},
"node_modules/eslint-plugin-jest": {
- "version": "27.4.2",
- "resolved": "https://registry.npmjs.org/eslint-plugin-jest/-/eslint-plugin-jest-27.4.2.tgz",
- "integrity": "sha512-3Nfvv3wbq2+PZlRTf2oaAWXWwbdBejFRBR2O8tAO67o+P8zno+QGbcDYaAXODlreXVg+9gvWhKKmG2rgfb8GEg==",
+ "version": "27.6.2",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-jest/-/eslint-plugin-jest-27.6.2.tgz",
+ "integrity": "sha512-CI1AlKrsNhYFoP48VU8BVWOi7+qHTq4bRxyUlGjeU8SfFt8abjXhjOuDzUoMp68DoXIx17KpNpIkMrl4s4ZW0g==",
"dev": true,
"dependencies": {
"@typescript-eslint/utils": "^5.10.0"
@@ -2942,16 +2974,18 @@
}
},
"node_modules/eslint-plugin-n": {
- "version": "16.2.0",
- "resolved": "https://registry.npmjs.org/eslint-plugin-n/-/eslint-plugin-n-16.2.0.tgz",
- "integrity": "sha512-AQER2jEyQOt1LG6JkGJCCIFotzmlcCZFur2wdKrp1JX2cNotC7Ae0BcD/4lLv3lUAArM9uNS8z/fsvXTd0L71g==",
+ "version": "16.6.2",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-n/-/eslint-plugin-n-16.6.2.tgz",
+ "integrity": "sha512-6TyDmZ1HXoFQXnhCTUjVFULReoBPOAjpuiKELMkeP40yffI/1ZRO+d9ug/VC6fqISo2WkuIBk3cvuRPALaWlOQ==",
"dev": true,
"dependencies": {
"@eslint-community/eslint-utils": "^4.4.0",
"builtins": "^5.0.1",
- "eslint-plugin-es-x": "^7.1.0",
+ "eslint-plugin-es-x": "^7.5.0",
"get-tsconfig": "^4.7.0",
+ "globals": "^13.24.0",
"ignore": "^5.2.4",
+ "is-builtin-module": "^3.2.1",
"is-core-module": "^2.12.1",
"minimatch": "^3.1.2",
"resolve": "^1.22.2",
@@ -3033,9 +3067,9 @@
}
},
"node_modules/eslint-plugin-security": {
- "version": "1.7.1",
- "resolved": "https://registry.npmjs.org/eslint-plugin-security/-/eslint-plugin-security-1.7.1.tgz",
- "integrity": "sha512-sMStceig8AFglhhT2LqlU5r+/fn9OwsA72O5bBuQVTssPCdQAOQzL+oMn/ZcpeUY6KcNfLJArgcrsSULNjYYdQ==",
+ "version": "2.1.0",
+ "resolved": "https://registry.npmjs.org/eslint-plugin-security/-/eslint-plugin-security-2.1.0.tgz",
+ "integrity": "sha512-ywxclP954bf8d3gr6KOQ/AFc+PRvWuhOxtPOEtiHmVYiZr/mcgQtmSJq6+hTEXC5ylTjHnPPG+PEnzlDiWMXbQ==",
"dev": true,
"dependencies": {
"safe-regex": "^2.1.1"
@@ -3228,9 +3262,9 @@
"dev": true
},
"node_modules/fast-glob": {
- "version": "3.3.1",
- "resolved": "https://registry.npmjs.org/fast-glob/-/fast-glob-3.3.1.tgz",
- "integrity": "sha512-kNFPyjhh5cKjrUltxs+wFx+ZkbRaxxmZ+X0ZU31SOsxCEtP9VPgtq2teZw1DebupL5GmDaNQ6yKMMVcM41iqDg==",
+ "version": "3.3.2",
+ "resolved": "https://registry.npmjs.org/fast-glob/-/fast-glob-3.3.2.tgz",
+ "integrity": "sha512-oX2ruAFQwf/Orj8m737Y5adxDQO0LAB7/S5MnxCdTNDd4p6BsyIVsv9JQsATbTSq8KHRpLwIHbVlUNatxd+1Ow==",
"dev": true,
"dependencies": {
"@nodelib/fs.stat": "^2.0.2",
@@ -3268,9 +3302,9 @@
"dev": true
},
"node_modules/fastq": {
- "version": "1.15.0",
- "resolved": "https://registry.npmjs.org/fastq/-/fastq-1.15.0.tgz",
- "integrity": "sha512-wBrocU2LCXXa+lWBt8RoIRD89Fi8OdABODa/kEnyeyjS5aZO5/GNvI5sEINADqP/h8M29UHTHUb53sUu5Ihqdw==",
+ "version": "1.16.0",
+ "resolved": "https://registry.npmjs.org/fastq/-/fastq-1.16.0.tgz",
+ "integrity": "sha512-ifCoaXsDrsdkWTtiNJX5uzHDsrck5TzfKKDcuFFTIrrc/BS076qgEIfoIy1VeZqViznfKiysPYTh/QeHtnIsYA==",
"dev": true,
"dependencies": {
"reusify": "^1.0.4"
@@ -3326,9 +3360,9 @@
}
},
"node_modules/flat-cache": {
- "version": "3.1.1",
- "resolved": "https://registry.npmjs.org/flat-cache/-/flat-cache-3.1.1.tgz",
- "integrity": "sha512-/qM2b3LUIaIgviBQovTLvijfyOQXPtSRnRK26ksj2J7rzPIecePUIpJsZ4T02Qg+xiAEKIs5K8dsHEd+VaKa/Q==",
+ "version": "3.2.0",
+ "resolved": "https://registry.npmjs.org/flat-cache/-/flat-cache-3.2.0.tgz",
+ "integrity": "sha512-CYcENa+FtcUKLmhhqyctpclsq7QF38pKjZHsGNiSQF5r4FtoKDWabFDl3hzaEQMvT1LHEysw5twgLvpYYb4vbw==",
"dev": true,
"dependencies": {
"flatted": "^3.2.9",
@@ -3336,7 +3370,7 @@
"rimraf": "^3.0.2"
},
"engines": {
- "node": ">=12.0.0"
+ "node": "^10.12.0 || >=12.0.0"
}
},
"node_modules/flatted": {
@@ -3466,15 +3500,15 @@
}
},
"node_modules/get-intrinsic": {
- "version": "1.2.1",
- "resolved": "https://registry.npmjs.org/get-intrinsic/-/get-intrinsic-1.2.1.tgz",
- "integrity": "sha512-2DcsyfABl+gVHEfCOaTrWgyt+tb6MSEGmKq+kI5HwLbIYgjgmMcV8KQ41uaKz1xxUcn9tJtgFbQUEVcEbd0FYw==",
+ "version": "1.2.2",
+ "resolved": "https://registry.npmjs.org/get-intrinsic/-/get-intrinsic-1.2.2.tgz",
+ "integrity": "sha512-0gSo4ml/0j98Y3lngkFEot/zhiCeWsbYIlZ+uZOVgzLyLaUw7wxUL+nCTP0XJvJg1AXulJRI3UJi8GsbDuxdGA==",
"dev": true,
"dependencies": {
- "function-bind": "^1.1.1",
- "has": "^1.0.3",
+ "function-bind": "^1.1.2",
"has-proto": "^1.0.1",
- "has-symbols": "^1.0.3"
+ "has-symbols": "^1.0.3",
+ "hasown": "^2.0.0"
},
"funding": {
"url": "https://github.com/sponsors/ljharb"
@@ -3562,9 +3596,9 @@
}
},
"node_modules/globals": {
- "version": "13.23.0",
- "resolved": "https://registry.npmjs.org/globals/-/globals-13.23.0.tgz",
- "integrity": "sha512-XAmF0RjlrjY23MA51q3HltdlGxUpXPvg0GioKiD9X6HD28iMjo2dKC8Vqwm7lne4GNr78+RHTfliktR6ZH09wA==",
+ "version": "13.24.0",
+ "resolved": "https://registry.npmjs.org/globals/-/globals-13.24.0.tgz",
+ "integrity": "sha512-AhO5QUcj8llrbG09iWhPU2B204J1xnPeL8kQmVorSsy+Sjj1sk8gIyh6cUocGmH4L0UuhAJy+hJMRA4mgA4mFQ==",
"dev": true,
"dependencies": {
"type-fest": "^0.20.2"
@@ -3635,15 +3669,6 @@
"integrity": "sha512-EtKwoO6kxCL9WO5xipiHTZlSzBm7WLT627TqC/uVRd0HKmq8NXyebnNYxDoBi7wt8eTWrUrKXCOVaFq9x1kgag==",
"dev": true
},
- "node_modules/has": {
- "version": "1.0.4",
- "resolved": "https://registry.npmjs.org/has/-/has-1.0.4.tgz",
- "integrity": "sha512-qdSAmqLF6209RFj4VVItywPMbm3vWylknmB3nvNiUIs72xAimcM8nVYxYr7ncvZq5qzk9MKIZR8ijqD/1QuYjQ==",
- "dev": true,
- "engines": {
- "node": ">= 0.4.0"
- }
- },
"node_modules/has-bigints": {
"version": "1.0.2",
"resolved": "https://registry.npmjs.org/has-bigints/-/has-bigints-1.0.2.tgz",
@@ -3663,12 +3688,12 @@
}
},
"node_modules/has-property-descriptors": {
- "version": "1.0.0",
- "resolved": "https://registry.npmjs.org/has-property-descriptors/-/has-property-descriptors-1.0.0.tgz",
- "integrity": "sha512-62DVLZGoiEBDHQyqG4w9xCuZ7eJEwNmJRWw2VY84Oedb7WFcA27fiEVe8oUQx9hAUJ4ekurquucTGwsyO1XGdQ==",
+ "version": "1.0.1",
+ "resolved": "https://registry.npmjs.org/has-property-descriptors/-/has-property-descriptors-1.0.1.tgz",
+ "integrity": "sha512-VsX8eaIewvas0xnvinAe9bw4WfIeODpGYikiWYLH+dma0Jw6KHYqWiWfhQlgOVK8D6PvjubK5Uc4P0iIhIcNVg==",
"dev": true,
"dependencies": {
- "get-intrinsic": "^1.1.1"
+ "get-intrinsic": "^1.2.2"
},
"funding": {
"url": "https://github.com/sponsors/ljharb"
@@ -3718,6 +3743,18 @@
"resolved": "https://registry.npmjs.org/hashcode/-/hashcode-1.0.3.tgz",
"integrity": "sha512-tfCzdiaz69Ii8eIdtYSCEnU0jw5RrYRd0u3sHRvs5Oqu/bQPk+aonT5jgRUT2MIuphjSvjB5lmixhHl7+X4ruw=="
},
+ "node_modules/hasown": {
+ "version": "2.0.0",
+ "resolved": "https://registry.npmjs.org/hasown/-/hasown-2.0.0.tgz",
+ "integrity": "sha512-vUptKVTpIJhcczKBbgnS+RtcuYMB8+oNzPK2/Hp3hanz8JmpATdmmgLgSaadVREkDm+e2giHwY3ZRkyjSIDDFA==",
+ "dev": true,
+ "dependencies": {
+ "function-bind": "^1.1.2"
+ },
+ "engines": {
+ "node": ">= 0.4"
+ }
+ },
"node_modules/html-escaper": {
"version": "2.0.2",
"resolved": "https://registry.npmjs.org/html-escaper/-/html-escaper-2.0.2.tgz",
@@ -3746,9 +3783,9 @@
}
},
"node_modules/ignore": {
- "version": "5.2.4",
- "resolved": "https://registry.npmjs.org/ignore/-/ignore-5.2.4.tgz",
- "integrity": "sha512-MAb38BcSbH0eHNBxn7ql2NH/kX33OkB3lZ1BNdh7ENeRChHTYsTvWrMubiIAMNS2llXEEgZ1MUOBtXChP3kaFQ==",
+ "version": "5.3.0",
+ "resolved": "https://registry.npmjs.org/ignore/-/ignore-5.3.0.tgz",
+ "integrity": "sha512-g7dmpshy+gD7mh88OC9NwSGTKoc3kyLAZQRU1mt53Aw/vnvfXnbC+F/7F7QoYVKbV+KNvJx8wArewKy1vXMtlg==",
"dev": true,
"engines": {
"node": ">= 4"
@@ -3815,13 +3852,13 @@
"dev": true
},
"node_modules/internal-slot": {
- "version": "1.0.5",
- "resolved": "https://registry.npmjs.org/internal-slot/-/internal-slot-1.0.5.tgz",
- "integrity": "sha512-Y+R5hJrzs52QCG2laLn4udYVnxsfny9CpOhNhUvk/SSSVyF6T27FzRbF0sroPidSu3X8oEAkOn2K804mjpt6UQ==",
+ "version": "1.0.6",
+ "resolved": "https://registry.npmjs.org/internal-slot/-/internal-slot-1.0.6.tgz",
+ "integrity": "sha512-Xj6dv+PsbtwyPpEflsejS+oIZxmMlV44zAhG479uYu89MsjcYOhCFnNyKrkJrihbsiasQyY0afoCl/9BLR65bg==",
"dev": true,
"dependencies": {
- "get-intrinsic": "^1.2.0",
- "has": "^1.0.3",
+ "get-intrinsic": "^1.2.2",
+ "hasown": "^2.0.0",
"side-channel": "^1.0.4"
},
"engines": {
@@ -3876,6 +3913,21 @@
"url": "https://github.com/sponsors/ljharb"
}
},
+ "node_modules/is-builtin-module": {
+ "version": "3.2.1",
+ "resolved": "https://registry.npmjs.org/is-builtin-module/-/is-builtin-module-3.2.1.tgz",
+ "integrity": "sha512-BSLE3HnV2syZ0FK0iMA/yUGplUeMmNz4AW5fnTunbCIqZi4vG3WjJT9FHMy5D69xmAYBHXQhJdALdpwVxV501A==",
+ "dev": true,
+ "dependencies": {
+ "builtin-modules": "^3.3.0"
+ },
+ "engines": {
+ "node": ">=6"
+ },
+ "funding": {
+ "url": "https://github.com/sponsors/sindresorhus"
+ }
+ },
"node_modules/is-callable": {
"version": "1.2.7",
"resolved": "https://registry.npmjs.org/is-callable/-/is-callable-1.2.7.tgz",
@@ -3889,12 +3941,12 @@
}
},
"node_modules/is-core-module": {
- "version": "2.13.0",
- "resolved": "https://registry.npmjs.org/is-core-module/-/is-core-module-2.13.0.tgz",
- "integrity": "sha512-Z7dk6Qo8pOCp3l4tsX2C5ZVas4V+UxwQodwZhLopL91TX8UyyHEXafPcyoeeWuLrwzHcr3igO78wNLwHJHsMCQ==",
+ "version": "2.13.1",
+ "resolved": "https://registry.npmjs.org/is-core-module/-/is-core-module-2.13.1.tgz",
+ "integrity": "sha512-hHrIjvZsftOsvKSn2TRYl63zvxsgE0K+0mYMoH6gD4omR5IWB2KynivBQczo3+wF1cCkjzvptnI9Q0sPU66ilw==",
"dev": true,
"dependencies": {
- "has": "^1.0.3"
+ "hasown": "^2.0.0"
},
"funding": {
"url": "https://github.com/sponsors/ljharb"
@@ -4109,9 +4161,9 @@
"dev": true
},
"node_modules/istanbul-lib-coverage": {
- "version": "3.2.0",
- "resolved": "https://registry.npmjs.org/istanbul-lib-coverage/-/istanbul-lib-coverage-3.2.0.tgz",
- "integrity": "sha512-eOeJ5BHCmHYvQK7xt9GkdHuzuCGS1Y6g9Gvnx3Ym33fz/HpLRYxiS0wHNr+m/MBC8B647Xt608vCDEvhl9c6Mw==",
+ "version": "3.2.2",
+ "resolved": "https://registry.npmjs.org/istanbul-lib-coverage/-/istanbul-lib-coverage-3.2.2.tgz",
+ "integrity": "sha512-O8dpsF+r0WV/8MNRKfnmrtCWhuKjxrq2w+jpzBL5UZKTi2LeVWnWOmWRxFlesJONmc+wLAGvKQZEOanko0LFTg==",
"dev": true,
"engines": {
"node": ">=8"
@@ -4950,17 +5002,17 @@
}
},
"node_modules/ldapjs": {
- "version": "3.0.5",
- "resolved": "https://registry.npmjs.org/ldapjs/-/ldapjs-3.0.5.tgz",
- "integrity": "sha512-W1baa/R/i5itkGdteMbz9Mwu/Tvs7DQQ2jy4cirwo6uQo1kpFzaQftNr45kC6xLC6/L24fUPcWf4tZ0cgkAiDQ==",
+ "version": "3.0.7",
+ "resolved": "https://registry.npmjs.org/ldapjs/-/ldapjs-3.0.7.tgz",
+ "integrity": "sha512-1ky+WrN+4CFMuoekUOv7Y1037XWdjKpu0xAPwSP+9KdvmV9PG+qOKlssDV6a+U32apwxdD3is/BZcWOYzN30cg==",
"dependencies": {
"@ldapjs/asn1": "^2.0.0",
"@ldapjs/attribute": "^1.0.0",
"@ldapjs/change": "^1.0.0",
- "@ldapjs/controls": "^2.0.0",
+ "@ldapjs/controls": "^2.1.0",
"@ldapjs/dn": "^1.1.0",
"@ldapjs/filter": "^2.1.1",
- "@ldapjs/messages": "^1.2.1",
+ "@ldapjs/messages": "^1.3.0",
"@ldapjs/protocol": "^1.2.1",
"abstract-logging": "^2.0.1",
"assert-plus": "^1.0.0",
@@ -5215,9 +5267,9 @@
"dev": true
},
"node_modules/node-releases": {
- "version": "2.0.13",
- "resolved": "https://registry.npmjs.org/node-releases/-/node-releases-2.0.13.tgz",
- "integrity": "sha512-uYr7J37ae/ORWdZeQ1xxMJe3NtdmqMC/JZK+geofDrkLUApKRHPd18/TxtBOJ4A0/+uUIliorNrfYV6s1b02eQ==",
+ "version": "2.0.14",
+ "resolved": "https://registry.npmjs.org/node-releases/-/node-releases-2.0.14.tgz",
+ "integrity": "sha512-y10wOWt8yZpqXmOgRo77WaHEmhYQYGNA6y421PKsKYWEK8aW+cqAphborZDhqfyKrbZEN92CN1X2KbafY2s7Yw==",
"dev": true
},
"node_modules/normalize-path": {
@@ -5260,13 +5312,13 @@
}
},
"node_modules/object.assign": {
- "version": "4.1.4",
- "resolved": "https://registry.npmjs.org/object.assign/-/object.assign-4.1.4.tgz",
- "integrity": "sha512-1mxKf0e58bvyjSCtKYY4sRe9itRk3PJpquJOjeIkz885CczcI4IvJJDLPS72oowuSh+pBxUFROpX+TU++hxhZQ==",
+ "version": "4.1.5",
+ "resolved": "https://registry.npmjs.org/object.assign/-/object.assign-4.1.5.tgz",
+ "integrity": "sha512-byy+U7gp+FVwmyzKPYhW2h5l3crpmGsxl7X2s8y43IgxvG4g3QZ6CffDtsNQy1WsmZpQbO+ybo0AlW7TY6DcBQ==",
"dev": true,
"dependencies": {
- "call-bind": "^1.0.2",
- "define-properties": "^1.1.4",
+ "call-bind": "^1.0.5",
+ "define-properties": "^1.2.1",
"has-symbols": "^1.0.3",
"object-keys": "^1.1.1"
},
@@ -5609,9 +5661,9 @@
}
},
"node_modules/process-warning": {
- "version": "2.2.0",
- "resolved": "https://registry.npmjs.org/process-warning/-/process-warning-2.2.0.tgz",
- "integrity": "sha512-/1WZ8+VQjR6avWOgHeEPd7SDQmFQ1B5mC1eRXsCm5TarlNmx/wCsa5GEaxGm05BORRtyG/Ex/3xq3TuRvq57qg=="
+ "version": "2.3.2",
+ "resolved": "https://registry.npmjs.org/process-warning/-/process-warning-2.3.2.tgz",
+ "integrity": "sha512-n9wh8tvBe5sFmsqlg+XQhaQLumwpqoAUruLwjCopgTmUBjJ/fjtBsJzKleCaIGBOMXYEhp1YfKl4d7rJ5ZKJGA=="
},
"node_modules/prompts": {
"version": "2.4.2",
@@ -5632,9 +5684,9 @@
"integrity": "sha512-D+zkORCbA9f1tdWRK0RaCR3GPv50cMxcrz4X8k5LTSUD1Dkw47mKJEZQNunItRTkWwgtaUSo1RVFRIG9ZXiFYg=="
},
"node_modules/punycode": {
- "version": "2.3.0",
- "resolved": "https://registry.npmjs.org/punycode/-/punycode-2.3.0.tgz",
- "integrity": "sha512-rRV+zQD8tVFys26lAGR9WUuS4iUAngJScM+ZRSKtvl5tKeZ2t5bvdNFdNHBW9FWR4guGHlgmsZ1G7BSm2wTbuA==",
+ "version": "2.3.1",
+ "resolved": "https://registry.npmjs.org/punycode/-/punycode-2.3.1.tgz",
+ "integrity": "sha512-vYt7UD1U9Wg6138shLtLOvdAu+8DsC/ilFtEVHcH+wydcSpNE20AfSOduf6MkRFahL5FY7X1oU7nKVZFtfq8Fg==",
"dev": true,
"engines": {
"node": ">=6"
@@ -5889,15 +5941,18 @@
}
},
"node_modules/safe-regex-test": {
- "version": "1.0.0",
- "resolved": "https://registry.npmjs.org/safe-regex-test/-/safe-regex-test-1.0.0.tgz",
- "integrity": "sha512-JBUUzyOgEwXQY1NuPtvcj/qcBDbDmEvWufhlnXZIm75DEHp+afM1r1ujJpJsV/gSM4t59tpDyPi1sd6ZaPFfsA==",
+ "version": "1.0.1",
+ "resolved": "https://registry.npmjs.org/safe-regex-test/-/safe-regex-test-1.0.1.tgz",
+ "integrity": "sha512-Y5NejJTTliTyY4H7sipGqY+RX5P87i3F7c4Rcepy72nq+mNLhIsD0W4c7kEmduMDQCSqtPsXPlSTsFhh2LQv+g==",
"dev": true,
"dependencies": {
- "call-bind": "^1.0.2",
- "get-intrinsic": "^1.1.3",
+ "call-bind": "^1.0.5",
+ "get-intrinsic": "^1.2.2",
"is-regex": "^1.1.4"
},
+ "engines": {
+ "node": ">= 0.4"
+ },
"funding": {
"url": "https://github.com/sponsors/ljharb"
}
@@ -6228,9 +6283,9 @@
}
},
"node_modules/tsconfig-paths": {
- "version": "3.14.2",
- "resolved": "https://registry.npmjs.org/tsconfig-paths/-/tsconfig-paths-3.14.2.tgz",
- "integrity": "sha512-o/9iXgCYc5L/JxCHPe3Hvh8Q/2xm5Z+p18PESBU6Ff33695QnCHBEjcytY2q19ua7Mbl/DavtBOLq+oG0RCL+g==",
+ "version": "3.15.0",
+ "resolved": "https://registry.npmjs.org/tsconfig-paths/-/tsconfig-paths-3.15.0.tgz",
+ "integrity": "sha512-2Ac2RgzDe/cn48GvOe3M+o82pEFewD3UPbyoUHHdKasHwJKjds4fLXWf/Ux5kATBKN20oaFGu+jbElp1pos0mg==",
"dev": true,
"dependencies": {
"@types/json5": "^0.0.29",
@@ -6380,9 +6435,9 @@
}
},
"node_modules/typescript": {
- "version": "5.2.2",
- "resolved": "https://registry.npmjs.org/typescript/-/typescript-5.2.2.tgz",
- "integrity": "sha512-mI4WrpHsbCIcwT9cF4FZvr80QUeKvsUsUvKDoR+X/7XHQH98xYD8YHZg7ANtz2GtZt/CBq2QJ0thkGJMHfqc1w==",
+ "version": "5.3.3",
+ "resolved": "https://registry.npmjs.org/typescript/-/typescript-5.3.3.tgz",
+ "integrity": "sha512-pXWcraxM0uxAS+tN0AG/BF2TyqmHO014Z070UsJ+pFvYuRSq8KH8DmWpnbXe0pEPDHXZV3FcAbJkijJ5oNEnWw==",
"dev": true,
"peer": true,
"bin": {
@@ -6409,9 +6464,9 @@
}
},
"node_modules/undici-types": {
- "version": "5.25.3",
- "resolved": "https://registry.npmjs.org/undici-types/-/undici-types-5.25.3.tgz",
- "integrity": "sha512-Ga1jfYwRn7+cP9v8auvEXN1rX3sWqlayd4HP7OKk4mZWylEmu3KzXDUGrQUN6Ol7qo1gPvB2e5gX6udnyEPgdA==",
+ "version": "5.26.5",
+ "resolved": "https://registry.npmjs.org/undici-types/-/undici-types-5.26.5.tgz",
+ "integrity": "sha512-JlCMO+ehdEIKqlFxk6IfVoAUVmgz7cU7zD/h9XZ0qzeosSHmUJVOzSQvvYSYWXkFXC+IfLKSIffhv0sVZup6pA==",
"dev": true
},
"node_modules/update-browserslist-db": {
@@ -6462,9 +6517,9 @@
}
},
"node_modules/v8-to-istanbul": {
- "version": "9.1.3",
- "resolved": "https://registry.npmjs.org/v8-to-istanbul/-/v8-to-istanbul-9.1.3.tgz",
- "integrity": "sha512-9lDD+EVI2fjFsMWXc6dy5JJzBsVTcQ2fVkfBvncZ6xJWG9wtBhOldG+mHkSL0+V1K/xgZz0JDO5UT5hFwHUghg==",
+ "version": "9.2.0",
+ "resolved": "https://registry.npmjs.org/v8-to-istanbul/-/v8-to-istanbul-9.2.0.tgz",
+ "integrity": "sha512-/EH/sDgxU2eGxajKdwLCDmQ4FWq+kpi3uCmBGpw1xJtnAxEjlD8j8PEiGWpCIMIs3ciNAgH0d3TTJiUkYzyZjA==",
"dev": true,
"dependencies": {
"@jridgewell/trace-mapping": "^0.3.12",
diff --git a/package.json b/package.json
index 3828822..d5937c1 100644
--- a/package.json
+++ b/package.json
@@ -1,6 +1,6 @@
{
"name": "AzureAD-LDAP-wrapper",
- "version": "2.0.1",
+ "version": "2.0.2",
"type": "commonjs",
"engines": {
"node": ">=17"
@@ -20,24 +20,24 @@
"url": "https://github.com/ahaenggli/AzureAD-LDAP-wrapper"
},
"dependencies": {
- "@azure/msal-node": "2.2.0",
- "axios": "~1.6.0",
+ "@azure/msal-node": "2.6.1",
+ "axios": "~1.6.5",
"diacritic": "0.0.2",
"dotenv": "^16.3.1",
"fs": "0.0.1-security",
"hashcode": "1.0.3",
"https-proxy-agent": "7.0.2",
- "ldapjs": "~3.0.5"
+ "ldapjs": "~3.0.7"
},
"devDependencies": {
- "eslint": "^8.51.0",
+ "eslint": "^8.56.0",
"eslint-config-standard": "^17.1.0",
- "eslint-plugin-import": "^2.28.1",
- "eslint-plugin-n": "^16.2.0",
+ "eslint-plugin-import": "^2.29.1",
+ "eslint-plugin-n": "^16.6.2",
"eslint-plugin-node": "~11.1.0",
"eslint-plugin-promise": "^6.1.1",
- "eslint-plugin-jest": "^27.4.2",
- "eslint-plugin-security": "~1.7.1",
+ "eslint-plugin-jest": "^27.6.2",
+ "eslint-plugin-security": "~2.1.0",
"jest": "^29.7.0"
}
}
\ No newline at end of file
 +# LDAP-wrapper for Microsoft Entra ID users/groups [](https://github.com/ahaenggli/AzureAD-LDAP-wrapper)
+# LDAP-wrapper for Microsoft Entra ID users/groups [](https://github.com/ahaenggli/AzureAD-LDAP-wrapper)  -AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from Azure Active Directory to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This enables other applications to connect to the LDAP server and utilize AzureAD login credentials, making it a possible solution for older applications that lack AzureAD support or for scenarios where managing a local AD controller is undesirable.
+LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from `Microsoft Entra ID` (formerly `Azure Active Directory`) to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This allows your other applications to connect to the LDAP server and thus allows your end users to authenticate with a work or school account.
+
+This it a possible workaround for older applications that lack Microsoft Entra ID support or for scenarios where managing a local AD controller is undesirable.
## Table of Contents
@@ -10,7 +12,7 @@ AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://
* [Run the LDAP-wrapper](#run-the-ldap-wrapper)
* [Usage](#usage)
* [Settings](#settings)
-* [Troubleshooting](#troubleshooting)
+* [Troubleshooting / FAQ](#troubleshooting-/-faq)
* [Security](#security)
* [Contributing](#contributing)
* [Support this project](#support-this-project)
@@ -22,49 +24,49 @@ AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://
sequenceDiagram
autonumber
participant LDAP client
- participant AzureAD-LDAP-wrapper
- participant AAD (Graph API)
+ participant LDAP-wrapper
+ participant ME-ID (Graph API)
- Note over AzureAD-LDAP-wrapper: start LDAP server
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups
- Note over AzureAD-LDAP-wrapper: cache users and groups locally
+ Note over LDAP-wrapper: start LDAP server
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups
+ Note over LDAP-wrapper: cache users and groups locally
- LDAP client->>+AzureAD-LDAP-wrapper: Attempt to bind with user credentials
- AzureAD-LDAP-wrapper->>+AAD (Graph API): Check user credentials
- AAD (Graph API)-->>-AzureAD-LDAP-wrapper: Valid credentials
+ LDAP client->>+LDAP-wrapper: Attempt to bind with user credentials
+ LDAP-wrapper->>+ME-ID (Graph API): Check user credentials
+ ME-ID (Graph API)-->>-LDAP-wrapper: Valid credentials
- Note over AzureAD-LDAP-wrapper: save password hash locally in the cache
- AzureAD-LDAP-wrapper->>-LDAP client: Successful bind/authenticate
+ Note over LDAP-wrapper: save password hash locally in the cache
+ LDAP-wrapper->>-LDAP client: Successful bind/authenticate
loop every 30 minutes
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups again
- Note over AzureAD-LDAP-wrapper: merge and cache users and groups locally
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups again
+ Note over LDAP-wrapper: merge and cache users and groups locally
end
```
-The AzureAD-LDAP-wrapper starts an LDAP server and fetches users and groups from the AAD Graph API. These are cached and merged locally.
+The LDAP-wrapper starts an LDAP server and fetches users and groups from the Microsoft Graph API. These are cached and merged locally.
-When an LDAP client attempts to bind with user credentials, the AzureAD-LDAP-wrapper checks these credentials by communicating with the AAD Graph API. If the credentials are valid, the AAD Graph API sends a success response to the AzureAD-LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the AzureAD-LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
+When an LDAP client attempts to bind with user credentials, the LDAP-wrapper checks these credentials by communicating with the Microsoft Graph API. If the credentials are valid, the Microsoft Graph API sends a success response to the LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
-The AzureAD-LDAP-wrapper periodically fetches user and group information from the AAD Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
+The LDAP-wrapper periodically fetches user and group information from the Microsoft Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
## Getting Started
### Requirements
-To use the AzureAD-LDAP-wrapper, you will need:
+To use the LDAP-wrapper, you will need:
-* An Azure Active Directory (AD) tenant with at least one registered user.
-* An Azure AD application registered in your tenant, with the following permissions:
+* A Microsoft Entra tenant with at least one registered user.
+* A Microsoft Entra application registered in your tenant, with the following permissions:
* For type `Application` grant `User.Read.All` and `Group.Read.All`.
* For type `Delegated` grant `User.Read`.
You can follow the instructions in the [installation guide](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/installation/create-azuread-application) to set up your application.
-To run the AzureAD-LDAP-wrapper, you'll need to have your Tenant ID, Application ID, and Application Secret available. These values are required to authenticate and authorize the application to access your Azure AD resources. You can find these values in the Azure portal.
+To run the LDAP-wrapper, you'll need to have your Tenant ID, Application ID, and Application Secret available. These values are required to authenticate and authorize the application to access your resources. You can find these values in the Microsoft Entra ID portal.
-Once you have created your Azure AD application, you can run the LDAP wrapper on your local machine, on a server or even a Synology NAS. Depending on your setup you will either need:
+Once you have created your Microsoft Entra application, you can run the LDAP-wrapper on your local machine, on a server or even a Synology NAS. Depending on your setup you will either need:
* Node.js version 17 or higher, which can be downloaded from the official [Node.js website](https://nodejs.org/en/download/).
@@ -93,7 +95,7 @@ Use "bridge" as your network.
4. Give your container a name and enable auto-restart.

-5. Configure the environment variables in "Advanced Settings". Be sure to double check your Azure values and define at least one binduser. The binduser (superuser like root) does not need to exist in your AzureAD. Replace example.com with your domain. Here is an example of a minimum required configuration:
+5. Configure the environment variables in "Advanced Settings". Be sure to double check your Microsoft Entra values and define at least one binduser. The binduser (superuser like root) does not need to exist in your tenant. Replace example.com with your domain. Here is an example of a minimum required configuration:
```bash
TZ: "Europe/Zurich" # optional
@@ -109,7 +111,7 @@ Use "bridge" as your network.
```

- A full list of all environment variables can be found [here](../../configuration/settings/).
+ A full list of all environment variables can be found [here](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/configuration/settings/).
6. Set local Port 389 to the Container Port 13389. If you receive the error Local port 389 conflicts with other ports used by other services, make sure that Synology Directory Service and Synology LDAP Server are not installed - they also use this port.

@@ -122,7 +124,7 @@ Use "bridge" as your network.
### Usage
-To enable users to log in to Synology NAS with their Azure credentials, you need to connect the NAS to the AzureAD-LDAP-wrapper. Here are the steps:
+To enable end users to log in to Synology NAS with their work or school account, you need to connect the NAS to the LDAP-wrapper. Here are the steps:
1. Go to Control Panel > Domain/LDAP and click "Join".

@@ -136,10 +138,10 @@ To enable users to log in to Synology NAS with their Azure credentials, you need
4. If you see a warning about a local group having the same name as a synchronized group, you can ignore it and skip the warning in "Details".

-5. Your NAS should now be connected successfully to the Azure AD LDAP-wrapper.
+5. Your NAS should now be connected successfully to the LDAP-wrapper.

-6. Check the "LDAP User" and "LDAP Group" tabs to ensure that all entries are fully synced. Assign the desired permissions to your synchronized users and groups. You can now log in with your Azure AD credentials.
+6. Check the "LDAP User" and "LDAP Group" tabs to ensure that all entries are fully synced. Assign the desired permissions to your synchronized users and groups. You can now log in with your Microsoft Entra account (work or school account).

7. Note that before accessing shared folders or files via network or Samba, each user must log in to DSM web GUI or another tool directly connected to the LDAP server. This step is also required after a password change, as the password hash for Samba is only set after a successful login.
@@ -148,19 +150,19 @@ To enable users to log in to Synology NAS with their Azure credentials, you need
To configure the LDAP-wrapper, you can use environment variables as it is intended to be used with Docker. A complete list of available variables can be found in the [configuration settings page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/configuration/settings) of the documentation.
-## Troubleshooting
+## Troubleshooting / FAQ
If you encounter any issues, start by checking the Docker log. Many errors are logged there, and this can help you identify the root cause of the problem. Additionally, the [troubleshooting page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/troubleshooting/) in the documentation provides further guidance on debugging common issues, including Samba-related ones. If you're still stuck, don't hesitate to open an issue, but be sure to attach relevant log files to help others diagnose the issue.
## Security
-It's important to note that the AzureAD-LDAP-wrapper involves transferring sensitive user information, so it's essential to ensure that it's used securely. There are several potential security risks to be aware of when using this wrapper. For more information on these risks and how to mitigate them, please read the [security page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/security/) in the documentation.
+It's important to note that the LDAP-wrapper involves transferring sensitive user information, so it's essential to ensure that it's used securely. There are several potential security risks to be aware of when using this wrapper. For more information on these risks and how to mitigate them, please read the [security page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/security/) in the documentation.
If you discover any security vulnerabilities, please refer to the instructions in [SECURITY.md](SECURITY.md) on how to report them.
## Contributing
-Contributions to the AzureAD-LDAP-wrapper are always welcome! If you have any suggestions, bug reports, or pull requests, please feel free to open an issue or a pull request on the project's GitHub repository.
+Contributions to the LDAP-wrapper are always welcome! If you have any suggestions, bug reports, or pull requests, please feel free to open an issue or a pull request on the project's GitHub repository.
## Support this project
@@ -170,4 +172,4 @@ Your support helps me maintain and improve this project. Thank you!
## License
-The AzureAD-LDAP-wrapper is licensed under the [MIT License](LICENSE).
+The LDAP-wrapper is licensed under the [MIT License](LICENSE).
diff --git a/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js b/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js
new file mode 100644
index 0000000..e8a6d7c
--- /dev/null
+++ b/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js
@@ -0,0 +1,111 @@
+/**
+ * This module contains customizer functions for modifying LDAP and Azure objects.
+ * @module customizer
+ *
+ * Modify the following variables to your needs:
+ * pets - The list of group names to filter the Azure groups by.
+ * Only users within these groups will be synced.
+ */
+
+'use strict';
+
+// keep only users within these groups from Azure
+const pets = ['group-b', 'administrators'];
+
+const config = require('../src/config');
+const helper = require('../src/helper');
+
+var customizer = {};
+
+/**
+ * Modifies the Azure groups by filtering them based on a predefined list of group names.
+ * @param {Array} azuregroups - The array of Azure groups.
+ * @returns {Array} - The modified array of Azure groups.
+ */
+customizer.ModifyAzureGroups = function (azuregroups) {
+ return azuregroups.filter(group => pets.includes(group.displayName.toLowerCase()));
+};
+
+/**
+ * Modifies the LDAP group by converting the gidNumber from string to int.
+ * @param {Object} ldapgroup - The LDAP group object.
+ * @param {Object} azuregroup - The Azure group object.
+ * @returns {Object} - The modified LDAP group object.
+ */
+customizer.ModifyLDAPGroup = function (ldapgroup, azuregroup) {
+ helper.log("customizer", "ModifyLDAPGroup", "called");
+ if (ldapgroup.hasOwnProperty("gidNumber")) {
+ let parsed = parseInt(ldapgroup.gidNumber);
+ if (isNaN(parsed)) parsed = ldapgroup.gidNumber;
+ ldapgroup.gidNumber = parsed;
+ }
+
+ return ldapgroup;
+};
+
+/**
+ * Modifies the LDAP user by converting the gidNumber and uidNumber from string to int.
+ * Sets gidNumber to 0 if the user has no groups.
+ * @param {Object} ldapuser - The LDAP user object.
+ * @param {Object} azureuser - The Azure user object.
+ * @returns {Object} - The modified LDAP user object.
+ */
+customizer.ModifyLDAPUser = function (ldapuser, azureuser) {
+ helper.log("customizer", "ModifyLDAPUser", "called");
+ if (ldapuser.hasOwnProperty("gidNumber")) {
+ let parsed = parseInt(ldapuser.gidNumber);
+ if (isNaN(parsed)) parsed = ldapuser.gidNumber;
+ ldapuser.gidNumber = parsed;
+ }
+ if (ldapuser.hasOwnProperty("uidNumber")) {
+ let parsed = parseInt(ldapuser.uidNumber);
+ if (isNaN(parsed)) parsed = ldapuser.uidNumber;
+ ldapuser.uidNumber = parsed;
+ }
+
+ // no groups for user? set gidNumber to 0
+ ldapuser.memberOf = ldapuser.memberOf.filter(e => e != config.LDAP_USERSGROUPSBASEDN);
+ if (Array.isArray(ldapuser.memberOf) && ldapuser.memberOf.length === 0) ldapuser.gidNumber = 0;
+
+ return ldapuser;
+};
+
+/**
+ * Modifies the LDAP objects globally by setting default values for certain properties.
+ * @param {Object} all - The object containing all LDAP objects.
+ * @returns {Object} - The modified object containing all LDAP objects.
+ */
+customizer.ModifyLDAPGlobal = function (all) {
+ let root = "uid=root," + config.LDAP_USERSDN;
+ for (var key of Object.keys(all)) {
+ all[key].creatorsName = root;
+
+ if (!all[key].hasOwnProperty("createTimestamp"))
+ all[key].createTimestamp = helper.ldap_now() + "Z";
+
+ if (!all[key].hasOwnProperty("entryCSN"))
+ all[key].entryCSN = helper.ldap_now() + ".000000Z#000000#000#000000";
+
+ all[key].modifiersName = root;
+
+ if (!all[key].hasOwnProperty("modifyTimestamp"))
+ all[key].modifyTimestamp = all[key].createTimestamp;
+
+ if (all[key].hasOwnProperty("sambaDomainName")) {
+ all[key].sambaDomainName = all[key].sambaDomainName.toLowerCase();
+ }
+
+ // only users with gidNumber > 0
+ if (all[key].hasOwnProperty("uidNumber")
+ && all[key].hasOwnProperty("gidNumber")
+ && all[key].uidNumber > 0
+ && all[key].gidNumber === 0
+ ) {
+ delete all[key];
+ }
+ }
+
+ return all;
+};
+
+module.exports = customizer;
\ No newline at end of file
diff --git a/docs/content/_index.md b/docs/content/_index.md
index b0e2b34..01f864d 100644
--- a/docs/content/_index.md
+++ b/docs/content/_index.md
@@ -1,12 +1,14 @@
---
-title: AzureAD-LDAP-wrapper
+title: LDAP-wrapper for Microsoft Entra ID
---
-AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from Azure Active Directory to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This enables other applications to connect to the LDAP server and utilize AzureAD login credentials, making it a possible solution for older applications that lack AzureAD support or for scenarios where managing a local AD controller is undesirable.
+LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from `Microsoft Entra ID` (formerly `Azure Active Directory`) to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This allows your other applications to connect to the LDAP server and thus allows your end users to authenticate with a work or school account.
+
+This it a possible workaround for older applications that lack Microsoft Entra ID support or for scenarios where managing a local AD controller is undesirable.
{{< hint type=note title="About the motivation" >}}
-I run the project on my Synology NAS in a Docker container. By connecting the NAS and some intranet web applications to the LDAP server, my users can log in to these services using their AzureAD credentials. Although it is possible to achieve this by [joining the NAS to AADDS](https://kb.synology.com/en-global/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain), I preferred not to maintain such a big setup, which includes a virtual machine, VPN, and AADDS, just to allow my three users to use their credentials almost everywhere.
+I run the project on my Synology NAS in a Docker container. By connecting the NAS and some intranet web applications to the LDAP server, my users can log in to these services using their work accounts. Although it is possible to achieve this by [joining the NAS to AADDS](https://kb.synology.com/en-global/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain), I preferred not to maintain such a big setup, which includes a virtual machine, VPN, and Microsoft Entra Domain Services (formerly AADDS / Azure Active Directory Domain Services), just to allow my three users to use their credentials almost everywhere.
{{< /hint >}}
@@ -16,31 +18,29 @@ I run the project on my Synology NAS in a Docker container. By connecting the NA
sequenceDiagram
autonumber
participant LDAP client
- participant AzureAD-LDAP-wrapper
- participant AAD (Graph API)
-
- Note over AzureAD-LDAP-wrapper: start LDAP server
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups
- Note over AzureAD-LDAP-wrapper: cache users and groups locally
-
- LDAP client->>+AzureAD-LDAP-wrapper: Attempt to bind with user credentials
- AzureAD-LDAP-wrapper->>+AAD (Graph API): Check user credentials
- AAD (Graph API)-->>-AzureAD-LDAP-wrapper: Valid credentials
-
- Note over AzureAD-LDAP-wrapper: save password hash locally in the cache
- AzureAD-LDAP-wrapper->>-LDAP client: Successful bind/authenticate
-
+ participant LDAP-wrapper
+ participant ME-ID (Graph API)
+
+ Note over LDAP-wrapper: start LDAP server
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups
+ Note over LDAP-wrapper: cache users and groups locally
+
+ LDAP client->>+LDAP-wrapper: Attempt to bind with user credentials
+ LDAP-wrapper->>+ME-ID (Graph API): Check user credentials
+ ME-ID (Graph API)-->>-LDAP-wrapper: Valid credentials
+
+ Note over LDAP-wrapper: save password hash locally in the cache
+ LDAP-wrapper->>-LDAP client: Successful bind/authenticate
+
loop every 30 minutes
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups again
- Note over AzureAD-LDAP-wrapper: merge and cache users and groups locally
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups again
+ Note over LDAP-wrapper: merge and cache users and groups locally
end
```
-The diagram shows the flow of communication between an LDAP client, the AzureAD-LDAP-wrapper, and the Azure Active Directory (AAD) via Graph API.
-
-First, the AzureAD-LDAP-wrapper starts an LDAP server and fetches users and groups from the AAD Graph API. These are cached and merged locally.
+The LDAP-wrapper starts an LDAP server and fetches users and groups from the Microsoft Graph API. These are cached and merged locally.
-When an LDAP client attempts to bind with user credentials, the AzureAD-LDAP-wrapper checks these credentials by communicating with the AAD Graph API. If the credentials are valid, the AAD Graph API sends a success response to the AzureAD-LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the AzureAD-LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
+When an LDAP client attempts to bind with user credentials, the LDAP-wrapper checks these credentials by communicating with the Microsoft Graph API. If the credentials are valid, the Microsoft Graph API sends a success response to the LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
-The AzureAD-LDAP-wrapper periodically fetches user and group information from the AAD Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
+The LDAP-wrapper periodically fetches user and group information from the Microsoft Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
diff --git a/docs/content/configuration/bypass-mfa.md b/docs/content/configuration/bypass-mfa.md
index 8a6a4ad..36e875f 100644
--- a/docs/content/configuration/bypass-mfa.md
+++ b/docs/content/configuration/bypass-mfa.md
@@ -2,25 +2,25 @@
title: Bypass MFA
---
-Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
+Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
There is no interactive window to enter another factor, and LDAP does not support this either.
If you need to use this LDAP-wrapper despite of activated MFA, there are two options:
-1. Disable MFA for this application in AzureAD (preferred).\
+1. Disable MFA for this application in your tenant (preferred).\
There are several ways to define MFA, but only some of them allows you to disable MFA.
- Per-user MFA\
- MFA could be [enabled individually](https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates) for each user. A possible workaround seems to be the [trusted IPs feature](https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings#trusted-ips), which allows to disable MFA for some IPs, but this feature requires Azure AD Premium.\
+ MFA could be [enabled individually](https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-userstates) for each user. A possible workaround seems to be the [trusted IPs feature](https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-mfasettings#trusted-ips), which allows to disable MFA for some IPs, but this feature requires Microsoft Entra ID Premium.\
If a login fails due to this MFA method, the error code is AADSTS50079.
- Security defaults\
- [Security defaults](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults) seems to be the only ways for customers using the free Azure AD plan to [enable multi-factor authentication](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-mfa-get-started#free-option) in their whole environment. It looks like there are no workarounds to disable MFA for certain IPs or applications.\
+ [Security defaults](https://learn.microsoft.com/en-us/entra/fundamentals/security-defaults) seems to be the only ways for customers using the free Microsoft Entra ID plan to [enable multi-factor authentication](https://learn.microsoft.com/en-us/entra/identity/authentication/concept-mfa-licensing#free-option) in their whole environment. It looks like there are no workarounds to disable MFA for certain IPs or applications.\
If a login fails due to this MFA method, the error code is AADSTS50076.
- Conditional Access\
- [Conditional Access](https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-all-users-mfa) can be used to require MFA for some or all the users. This is the most flexible way to activate MFA, but it is a premium feature. The settings allows to exclude certain apps. If a login fails due to this MFA method, the error codea are either AADSTS50158 (for external MFA like Duo) or also AADSTS50079. As a simple workaround, the app used by the LDAP-wrapper can be excluded:
- - Add a URL in the app (e.g. "https://localhost")
+ [Conditional Access](https://learn.microsoft.com/en-us/entra/identity/conditional-access/howto-conditional-access-policy-all-users-mfa) can be used to require MFA for some or all the users. This is the most flexible way to activate MFA, but it is a premium feature. The settings allows to exclude certain apps. If a login fails due to this MFA method, the error codea are either AADSTS50158 (for external MFA like Duo) or also AADSTS50079. As a simple workaround, the app used by the LDAP-wrapper can be excluded:
+ - Add a URL in the app (e.g. "
-AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from Azure Active Directory to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This enables other applications to connect to the LDAP server and utilize AzureAD login credentials, making it a possible solution for older applications that lack AzureAD support or for scenarios where managing a local AD controller is undesirable.
+LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from `Microsoft Entra ID` (formerly `Azure Active Directory`) to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This allows your other applications to connect to the LDAP server and thus allows your end users to authenticate with a work or school account.
+
+This it a possible workaround for older applications that lack Microsoft Entra ID support or for scenarios where managing a local AD controller is undesirable.
## Table of Contents
@@ -10,7 +12,7 @@ AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://
* [Run the LDAP-wrapper](#run-the-ldap-wrapper)
* [Usage](#usage)
* [Settings](#settings)
-* [Troubleshooting](#troubleshooting)
+* [Troubleshooting / FAQ](#troubleshooting-/-faq)
* [Security](#security)
* [Contributing](#contributing)
* [Support this project](#support-this-project)
@@ -22,49 +24,49 @@ AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://
sequenceDiagram
autonumber
participant LDAP client
- participant AzureAD-LDAP-wrapper
- participant AAD (Graph API)
+ participant LDAP-wrapper
+ participant ME-ID (Graph API)
- Note over AzureAD-LDAP-wrapper: start LDAP server
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups
- Note over AzureAD-LDAP-wrapper: cache users and groups locally
+ Note over LDAP-wrapper: start LDAP server
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups
+ Note over LDAP-wrapper: cache users and groups locally
- LDAP client->>+AzureAD-LDAP-wrapper: Attempt to bind with user credentials
- AzureAD-LDAP-wrapper->>+AAD (Graph API): Check user credentials
- AAD (Graph API)-->>-AzureAD-LDAP-wrapper: Valid credentials
+ LDAP client->>+LDAP-wrapper: Attempt to bind with user credentials
+ LDAP-wrapper->>+ME-ID (Graph API): Check user credentials
+ ME-ID (Graph API)-->>-LDAP-wrapper: Valid credentials
- Note over AzureAD-LDAP-wrapper: save password hash locally in the cache
- AzureAD-LDAP-wrapper->>-LDAP client: Successful bind/authenticate
+ Note over LDAP-wrapper: save password hash locally in the cache
+ LDAP-wrapper->>-LDAP client: Successful bind/authenticate
loop every 30 minutes
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups again
- Note over AzureAD-LDAP-wrapper: merge and cache users and groups locally
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups again
+ Note over LDAP-wrapper: merge and cache users and groups locally
end
```
-The AzureAD-LDAP-wrapper starts an LDAP server and fetches users and groups from the AAD Graph API. These are cached and merged locally.
+The LDAP-wrapper starts an LDAP server and fetches users and groups from the Microsoft Graph API. These are cached and merged locally.
-When an LDAP client attempts to bind with user credentials, the AzureAD-LDAP-wrapper checks these credentials by communicating with the AAD Graph API. If the credentials are valid, the AAD Graph API sends a success response to the AzureAD-LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the AzureAD-LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
+When an LDAP client attempts to bind with user credentials, the LDAP-wrapper checks these credentials by communicating with the Microsoft Graph API. If the credentials are valid, the Microsoft Graph API sends a success response to the LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
-The AzureAD-LDAP-wrapper periodically fetches user and group information from the AAD Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
+The LDAP-wrapper periodically fetches user and group information from the Microsoft Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
## Getting Started
### Requirements
-To use the AzureAD-LDAP-wrapper, you will need:
+To use the LDAP-wrapper, you will need:
-* An Azure Active Directory (AD) tenant with at least one registered user.
-* An Azure AD application registered in your tenant, with the following permissions:
+* A Microsoft Entra tenant with at least one registered user.
+* A Microsoft Entra application registered in your tenant, with the following permissions:
* For type `Application` grant `User.Read.All` and `Group.Read.All`.
* For type `Delegated` grant `User.Read`.
You can follow the instructions in the [installation guide](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/installation/create-azuread-application) to set up your application.
-To run the AzureAD-LDAP-wrapper, you'll need to have your Tenant ID, Application ID, and Application Secret available. These values are required to authenticate and authorize the application to access your Azure AD resources. You can find these values in the Azure portal.
+To run the LDAP-wrapper, you'll need to have your Tenant ID, Application ID, and Application Secret available. These values are required to authenticate and authorize the application to access your resources. You can find these values in the Microsoft Entra ID portal.
-Once you have created your Azure AD application, you can run the LDAP wrapper on your local machine, on a server or even a Synology NAS. Depending on your setup you will either need:
+Once you have created your Microsoft Entra application, you can run the LDAP-wrapper on your local machine, on a server or even a Synology NAS. Depending on your setup you will either need:
* Node.js version 17 or higher, which can be downloaded from the official [Node.js website](https://nodejs.org/en/download/).
@@ -93,7 +95,7 @@ Use "bridge" as your network.
4. Give your container a name and enable auto-restart.

-5. Configure the environment variables in "Advanced Settings". Be sure to double check your Azure values and define at least one binduser. The binduser (superuser like root) does not need to exist in your AzureAD. Replace example.com with your domain. Here is an example of a minimum required configuration:
+5. Configure the environment variables in "Advanced Settings". Be sure to double check your Microsoft Entra values and define at least one binduser. The binduser (superuser like root) does not need to exist in your tenant. Replace example.com with your domain. Here is an example of a minimum required configuration:
```bash
TZ: "Europe/Zurich" # optional
@@ -109,7 +111,7 @@ Use "bridge" as your network.
```

- A full list of all environment variables can be found [here](../../configuration/settings/).
+ A full list of all environment variables can be found [here](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/configuration/settings/).
6. Set local Port 389 to the Container Port 13389. If you receive the error Local port 389 conflicts with other ports used by other services, make sure that Synology Directory Service and Synology LDAP Server are not installed - they also use this port.

@@ -122,7 +124,7 @@ Use "bridge" as your network.
### Usage
-To enable users to log in to Synology NAS with their Azure credentials, you need to connect the NAS to the AzureAD-LDAP-wrapper. Here are the steps:
+To enable end users to log in to Synology NAS with their work or school account, you need to connect the NAS to the LDAP-wrapper. Here are the steps:
1. Go to Control Panel > Domain/LDAP and click "Join".

@@ -136,10 +138,10 @@ To enable users to log in to Synology NAS with their Azure credentials, you need
4. If you see a warning about a local group having the same name as a synchronized group, you can ignore it and skip the warning in "Details".

-5. Your NAS should now be connected successfully to the Azure AD LDAP-wrapper.
+5. Your NAS should now be connected successfully to the LDAP-wrapper.

-6. Check the "LDAP User" and "LDAP Group" tabs to ensure that all entries are fully synced. Assign the desired permissions to your synchronized users and groups. You can now log in with your Azure AD credentials.
+6. Check the "LDAP User" and "LDAP Group" tabs to ensure that all entries are fully synced. Assign the desired permissions to your synchronized users and groups. You can now log in with your Microsoft Entra account (work or school account).

7. Note that before accessing shared folders or files via network or Samba, each user must log in to DSM web GUI or another tool directly connected to the LDAP server. This step is also required after a password change, as the password hash for Samba is only set after a successful login.
@@ -148,19 +150,19 @@ To enable users to log in to Synology NAS with their Azure credentials, you need
To configure the LDAP-wrapper, you can use environment variables as it is intended to be used with Docker. A complete list of available variables can be found in the [configuration settings page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/configuration/settings) of the documentation.
-## Troubleshooting
+## Troubleshooting / FAQ
If you encounter any issues, start by checking the Docker log. Many errors are logged there, and this can help you identify the root cause of the problem. Additionally, the [troubleshooting page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/troubleshooting/) in the documentation provides further guidance on debugging common issues, including Samba-related ones. If you're still stuck, don't hesitate to open an issue, but be sure to attach relevant log files to help others diagnose the issue.
## Security
-It's important to note that the AzureAD-LDAP-wrapper involves transferring sensitive user information, so it's essential to ensure that it's used securely. There are several potential security risks to be aware of when using this wrapper. For more information on these risks and how to mitigate them, please read the [security page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/security/) in the documentation.
+It's important to note that the LDAP-wrapper involves transferring sensitive user information, so it's essential to ensure that it's used securely. There are several potential security risks to be aware of when using this wrapper. For more information on these risks and how to mitigate them, please read the [security page](https://ahaenggli.github.io/AzureAD-LDAP-wrapper/security/) in the documentation.
If you discover any security vulnerabilities, please refer to the instructions in [SECURITY.md](SECURITY.md) on how to report them.
## Contributing
-Contributions to the AzureAD-LDAP-wrapper are always welcome! If you have any suggestions, bug reports, or pull requests, please feel free to open an issue or a pull request on the project's GitHub repository.
+Contributions to the LDAP-wrapper are always welcome! If you have any suggestions, bug reports, or pull requests, please feel free to open an issue or a pull request on the project's GitHub repository.
## Support this project
@@ -170,4 +172,4 @@ Your support helps me maintain and improve this project. Thank you!
## License
-The AzureAD-LDAP-wrapper is licensed under the [MIT License](LICENSE).
+The LDAP-wrapper is licensed under the [MIT License](LICENSE).
diff --git a/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js b/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js
new file mode 100644
index 0000000..e8a6d7c
--- /dev/null
+++ b/customizer/customizer_DSM7_IDs_string2int_filterUserByGroups.js
@@ -0,0 +1,111 @@
+/**
+ * This module contains customizer functions for modifying LDAP and Azure objects.
+ * @module customizer
+ *
+ * Modify the following variables to your needs:
+ * pets - The list of group names to filter the Azure groups by.
+ * Only users within these groups will be synced.
+ */
+
+'use strict';
+
+// keep only users within these groups from Azure
+const pets = ['group-b', 'administrators'];
+
+const config = require('../src/config');
+const helper = require('../src/helper');
+
+var customizer = {};
+
+/**
+ * Modifies the Azure groups by filtering them based on a predefined list of group names.
+ * @param {Array} azuregroups - The array of Azure groups.
+ * @returns {Array} - The modified array of Azure groups.
+ */
+customizer.ModifyAzureGroups = function (azuregroups) {
+ return azuregroups.filter(group => pets.includes(group.displayName.toLowerCase()));
+};
+
+/**
+ * Modifies the LDAP group by converting the gidNumber from string to int.
+ * @param {Object} ldapgroup - The LDAP group object.
+ * @param {Object} azuregroup - The Azure group object.
+ * @returns {Object} - The modified LDAP group object.
+ */
+customizer.ModifyLDAPGroup = function (ldapgroup, azuregroup) {
+ helper.log("customizer", "ModifyLDAPGroup", "called");
+ if (ldapgroup.hasOwnProperty("gidNumber")) {
+ let parsed = parseInt(ldapgroup.gidNumber);
+ if (isNaN(parsed)) parsed = ldapgroup.gidNumber;
+ ldapgroup.gidNumber = parsed;
+ }
+
+ return ldapgroup;
+};
+
+/**
+ * Modifies the LDAP user by converting the gidNumber and uidNumber from string to int.
+ * Sets gidNumber to 0 if the user has no groups.
+ * @param {Object} ldapuser - The LDAP user object.
+ * @param {Object} azureuser - The Azure user object.
+ * @returns {Object} - The modified LDAP user object.
+ */
+customizer.ModifyLDAPUser = function (ldapuser, azureuser) {
+ helper.log("customizer", "ModifyLDAPUser", "called");
+ if (ldapuser.hasOwnProperty("gidNumber")) {
+ let parsed = parseInt(ldapuser.gidNumber);
+ if (isNaN(parsed)) parsed = ldapuser.gidNumber;
+ ldapuser.gidNumber = parsed;
+ }
+ if (ldapuser.hasOwnProperty("uidNumber")) {
+ let parsed = parseInt(ldapuser.uidNumber);
+ if (isNaN(parsed)) parsed = ldapuser.uidNumber;
+ ldapuser.uidNumber = parsed;
+ }
+
+ // no groups for user? set gidNumber to 0
+ ldapuser.memberOf = ldapuser.memberOf.filter(e => e != config.LDAP_USERSGROUPSBASEDN);
+ if (Array.isArray(ldapuser.memberOf) && ldapuser.memberOf.length === 0) ldapuser.gidNumber = 0;
+
+ return ldapuser;
+};
+
+/**
+ * Modifies the LDAP objects globally by setting default values for certain properties.
+ * @param {Object} all - The object containing all LDAP objects.
+ * @returns {Object} - The modified object containing all LDAP objects.
+ */
+customizer.ModifyLDAPGlobal = function (all) {
+ let root = "uid=root," + config.LDAP_USERSDN;
+ for (var key of Object.keys(all)) {
+ all[key].creatorsName = root;
+
+ if (!all[key].hasOwnProperty("createTimestamp"))
+ all[key].createTimestamp = helper.ldap_now() + "Z";
+
+ if (!all[key].hasOwnProperty("entryCSN"))
+ all[key].entryCSN = helper.ldap_now() + ".000000Z#000000#000#000000";
+
+ all[key].modifiersName = root;
+
+ if (!all[key].hasOwnProperty("modifyTimestamp"))
+ all[key].modifyTimestamp = all[key].createTimestamp;
+
+ if (all[key].hasOwnProperty("sambaDomainName")) {
+ all[key].sambaDomainName = all[key].sambaDomainName.toLowerCase();
+ }
+
+ // only users with gidNumber > 0
+ if (all[key].hasOwnProperty("uidNumber")
+ && all[key].hasOwnProperty("gidNumber")
+ && all[key].uidNumber > 0
+ && all[key].gidNumber === 0
+ ) {
+ delete all[key];
+ }
+ }
+
+ return all;
+};
+
+module.exports = customizer;
\ No newline at end of file
diff --git a/docs/content/_index.md b/docs/content/_index.md
index b0e2b34..01f864d 100644
--- a/docs/content/_index.md
+++ b/docs/content/_index.md
@@ -1,12 +1,14 @@
---
-title: AzureAD-LDAP-wrapper
+title: LDAP-wrapper for Microsoft Entra ID
---
-AzureAD-LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from Azure Active Directory to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This enables other applications to connect to the LDAP server and utilize AzureAD login credentials, making it a possible solution for older applications that lack AzureAD support or for scenarios where managing a local AD controller is undesirable.
+LDAP-wrapper is a Node.js LDAP server built on top of ([ldapjs](https://github.com/ldapjs/node-ldapjs)) that allows users and groups from `Microsoft Entra ID` (formerly `Azure Active Directory`) to be accessed through the LDAP protocol. User authentication is performed using Microsoft Graph API on every login attempt. This allows your other applications to connect to the LDAP server and thus allows your end users to authenticate with a work or school account.
+
+This it a possible workaround for older applications that lack Microsoft Entra ID support or for scenarios where managing a local AD controller is undesirable.
{{< hint type=note title="About the motivation" >}}
-I run the project on my Synology NAS in a Docker container. By connecting the NAS and some intranet web applications to the LDAP server, my users can log in to these services using their AzureAD credentials. Although it is possible to achieve this by [joining the NAS to AADDS](https://kb.synology.com/en-global/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain), I preferred not to maintain such a big setup, which includes a virtual machine, VPN, and AADDS, just to allow my three users to use their credentials almost everywhere.
+I run the project on my Synology NAS in a Docker container. By connecting the NAS and some intranet web applications to the LDAP server, my users can log in to these services using their work accounts. Although it is possible to achieve this by [joining the NAS to AADDS](https://kb.synology.com/en-global/DSM/tutorial/How_to_join_NAS_to_Azure_AD_Domain), I preferred not to maintain such a big setup, which includes a virtual machine, VPN, and Microsoft Entra Domain Services (formerly AADDS / Azure Active Directory Domain Services), just to allow my three users to use their credentials almost everywhere.
{{< /hint >}}
@@ -16,31 +18,29 @@ I run the project on my Synology NAS in a Docker container. By connecting the NA
sequenceDiagram
autonumber
participant LDAP client
- participant AzureAD-LDAP-wrapper
- participant AAD (Graph API)
-
- Note over AzureAD-LDAP-wrapper: start LDAP server
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups
- Note over AzureAD-LDAP-wrapper: cache users and groups locally
-
- LDAP client->>+AzureAD-LDAP-wrapper: Attempt to bind with user credentials
- AzureAD-LDAP-wrapper->>+AAD (Graph API): Check user credentials
- AAD (Graph API)-->>-AzureAD-LDAP-wrapper: Valid credentials
-
- Note over AzureAD-LDAP-wrapper: save password hash locally in the cache
- AzureAD-LDAP-wrapper->>-LDAP client: Successful bind/authenticate
-
+ participant LDAP-wrapper
+ participant ME-ID (Graph API)
+
+ Note over LDAP-wrapper: start LDAP server
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups
+ Note over LDAP-wrapper: cache users and groups locally
+
+ LDAP client->>+LDAP-wrapper: Attempt to bind with user credentials
+ LDAP-wrapper->>+ME-ID (Graph API): Check user credentials
+ ME-ID (Graph API)-->>-LDAP-wrapper: Valid credentials
+
+ Note over LDAP-wrapper: save password hash locally in the cache
+ LDAP-wrapper->>-LDAP client: Successful bind/authenticate
+
loop every 30 minutes
- AzureAD-LDAP-wrapper->>AAD (Graph API): Fetch users and groups again
- Note over AzureAD-LDAP-wrapper: merge and cache users and groups locally
+ LDAP-wrapper->>ME-ID (Graph API): Fetch users and groups again
+ Note over LDAP-wrapper: merge and cache users and groups locally
end
```
-The diagram shows the flow of communication between an LDAP client, the AzureAD-LDAP-wrapper, and the Azure Active Directory (AAD) via Graph API.
-
-First, the AzureAD-LDAP-wrapper starts an LDAP server and fetches users and groups from the AAD Graph API. These are cached and merged locally.
+The LDAP-wrapper starts an LDAP server and fetches users and groups from the Microsoft Graph API. These are cached and merged locally.
-When an LDAP client attempts to bind with user credentials, the AzureAD-LDAP-wrapper checks these credentials by communicating with the AAD Graph API. If the credentials are valid, the AAD Graph API sends a success response to the AzureAD-LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the AzureAD-LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
+When an LDAP client attempts to bind with user credentials, the LDAP-wrapper checks these credentials by communicating with the Microsoft Graph API. If the credentials are valid, the Microsoft Graph API sends a success response to the LDAP-wrapper, which then sends a successful bind message to the user's LDAP client. Additionally, the LDAP-wrapper saves the user's password hash in the sambaNTPassword attribute and sets the sambaPwdLastSet attribute to "now". This allows the user to access samba shares, such as those on a NAS, from Windows PCs.
-The AzureAD-LDAP-wrapper periodically fetches user and group information from the AAD Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
+The LDAP-wrapper periodically fetches user and group information from the Microsoft Graph API every 30 minutes, merging and caching the results locally. This process preserves attributes like uid, gid, sambaNTPassword, and sambaPwdLastSet.
diff --git a/docs/content/configuration/bypass-mfa.md b/docs/content/configuration/bypass-mfa.md
index 8a6a4ad..36e875f 100644
--- a/docs/content/configuration/bypass-mfa.md
+++ b/docs/content/configuration/bypass-mfa.md
@@ -2,25 +2,25 @@
title: Bypass MFA
---
-Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
+Officially MFA is not supported by this LDAP-wrapper. The login for users with activated MFA simply fails, as mentioned [here](https://learn.microsoft.com/en-us/entra/identity-platform/v2-oauth-ropc) and [here](https://github.com/Azure/ms-rest-nodeauth/issues/93).
There is no interactive window to enter another factor, and LDAP does not support this either.
If you need to use this LDAP-wrapper despite of activated MFA, there are two options:
-1. Disable MFA for this application in AzureAD (preferred).\
+1. Disable MFA for this application in your tenant (preferred).\
There are several ways to define MFA, but only some of them allows you to disable MFA.
- Per-user MFA\
- MFA could be [enabled individually](https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-userstates) for each user. A possible workaround seems to be the [trusted IPs feature](https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings#trusted-ips), which allows to disable MFA for some IPs, but this feature requires Azure AD Premium.\
+ MFA could be [enabled individually](https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-userstates) for each user. A possible workaround seems to be the [trusted IPs feature](https://learn.microsoft.com/en-us/entra/identity/authentication/howto-mfa-mfasettings#trusted-ips), which allows to disable MFA for some IPs, but this feature requires Microsoft Entra ID Premium.\
If a login fails due to this MFA method, the error code is AADSTS50079.
- Security defaults\
- [Security defaults](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults) seems to be the only ways for customers using the free Azure AD plan to [enable multi-factor authentication](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-mfa-get-started#free-option) in their whole environment. It looks like there are no workarounds to disable MFA for certain IPs or applications.\
+ [Security defaults](https://learn.microsoft.com/en-us/entra/fundamentals/security-defaults) seems to be the only ways for customers using the free Microsoft Entra ID plan to [enable multi-factor authentication](https://learn.microsoft.com/en-us/entra/identity/authentication/concept-mfa-licensing#free-option) in their whole environment. It looks like there are no workarounds to disable MFA for certain IPs or applications.\
If a login fails due to this MFA method, the error code is AADSTS50076.
- Conditional Access\
- [Conditional Access](https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-all-users-mfa) can be used to require MFA for some or all the users. This is the most flexible way to activate MFA, but it is a premium feature. The settings allows to exclude certain apps. If a login fails due to this MFA method, the error codea are either AADSTS50158 (for external MFA like Duo) or also AADSTS50079. As a simple workaround, the app used by the LDAP-wrapper can be excluded:
- - Add a URL in the app (e.g. "https://localhost")
+ [Conditional Access](https://learn.microsoft.com/en-us/entra/identity/conditional-access/howto-conditional-access-policy-all-users-mfa) can be used to require MFA for some or all the users. This is the most flexible way to activate MFA, but it is a premium feature. The settings allows to exclude certain apps. If a login fails due to this MFA method, the error codea are either AADSTS50158 (for external MFA like Duo) or also AADSTS50079. As a simple workaround, the app used by the LDAP-wrapper can be excluded:
+ - Add a URL in the app (e.g. "