-
Notifications
You must be signed in to change notification settings - Fork 32
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
CVE-2023-29827 #56
Comments
|
Dear Maintainer's/Project Team, I am writing to inform you about a security vulnerability in the EJS template engine (version 3.1.10) that affects your project via transitive dependencies. Specifically, the vulnerability is present in Given the potential security risks associated with this vulnerability, I would like to request an update to your project that removes or replaces the vulnerable dependency. A possible solution could be updating to a non-vulnerable version of EJS (3.1.11 or later) or switching to an alternative templating engine if feasible. Addressing this issue would help ensure that projects depending on your library can maintain security best practices. Please let me know if there are any plans to release an update or if there are workarounds that can be implemented in the meantime. Thank you for your attention to this matter and for your continued work on this important project. Best regards, |
|
@Prozect2024 There is no version EJS 3.1.11, so this won't help. |
|
Dear maintainers, it would really help if you could take a look at that CVE-2023-29827 issue (or rather, its update CVE-2024-33883), whether rollup-plugin-off-main-thread is affected or not. We especially like to know if it passes unsanitized input to the ejs |
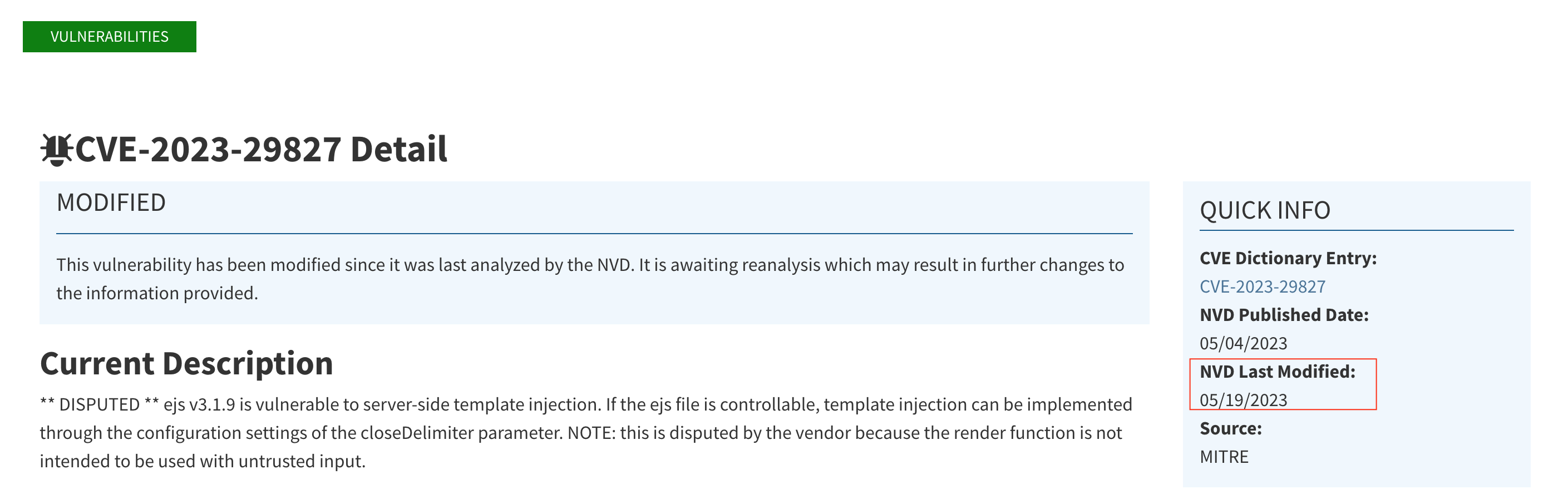
Ref nvd: https://nvd.nist.gov/vuln/detail/CVE-2023-29827
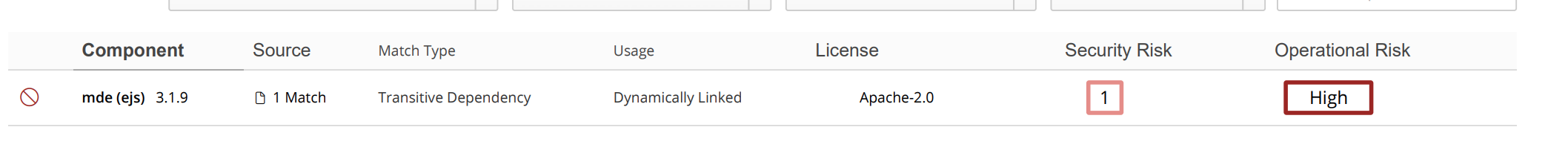
Dependency Path: react-scripts (5.0.1) -> workbox-build (6.6.0) -> @surma/rollup-plugin-off-main-thread (2.2.3) -> ejs(3.1.9)
Img nvd
Img black duck
The text was updated successfully, but these errors were encountered: