-
Notifications
You must be signed in to change notification settings - Fork 1
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
jq magic to create contacts for SimpleLogin aliases
1 parent
dfa5aef
commit 6a19bdc
Showing
3 changed files
with
64 additions
and
3 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
22 changes: 22 additions & 0 deletions
22
content/blog/dnsmasq: Custom DNS resolvers for specific domains.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,22 @@ | ||
| --- | ||
| external: false | ||
| notion: b86aaac5-f487-4d84-8ec1-d3cc4eaa7fda | ||
| title: dnsmasq: Custom DNS resolvers for specific domains | ||
| slug: dnsmasq:-custom-dns-resolvers-for-specific-domains | ||
| description: It's possible to setup custom DNS resolvers for certain domains using a dnsmasq config file. Requests still pass through pihole, for ad-blocking capabilities. | ||
| date: 2021-10-30 | ||
| --- | ||
|
|
||
| Learned a neat thing today -- [it's possible to set custom DNS resolvers for certain domains](https://news.ycombinator.com/item?id=29026068). I can create a custom config file for dnsmasq and specify the DNS resolvers to use for those domains. I don't have a need for it today, but may be handy in cases like archive.is not loading on Cloudflare DNS. | ||
|
|
||
| These requests still go through pihole, so ad-blocking capabilities are available. It's just the upstream that changes. My test below confirms so: I have set `dnsleaktest.com` to be queried using Google DNS but requests still pass through pihole. | ||
|
|
||
| ```text | ||
| /etc/dnsmasq.d/02-test.conf | ||
| server=/dnsleaktest.com/8.8.8.8 | ||
| server=/dnsleaktest.com/8.8.4.4 | ||
| ``` | ||
|
|
||
| 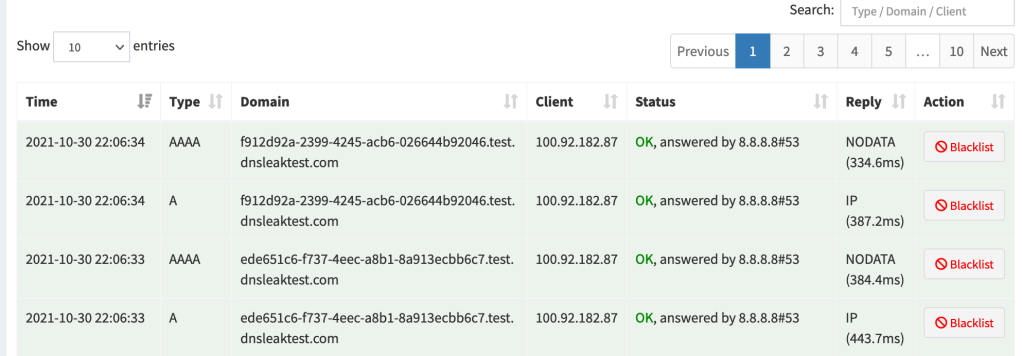 | ||
|
|
||
| I use two Raspberry Pi devices at home, both running pihole with Unbound as a recursive DNS resolver. These devices are connected to my [Tailscale network, so all of my devices (and my friends) can enjoy Unbound and pihole's ad-blocking capabilities](https://blogarunsathiya.wordpress.com/2021/03/30/pi-hole-on-tailscale/). |
36 changes: 36 additions & 0 deletions
36
content/blog/jq magic to create contacts for SimpleLogin aliases.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,36 @@ | ||
| --- | ||
| external: false | ||
| notion: fe3dd800-d59c-4887-96cd-179e64177a33 | ||
| title: jq magic to create contacts for SimpleLogin aliases | ||
| slug: jq-magic-to-create-contacts-for-simplelogin-aliases | ||
| description: If you are using SimpleLogin to create unique email aliases, here's a hacky workaround using jq to create contact reverse alias from your terminal application. | ||
| date: 2021-10-11 | ||
| --- | ||
|
|
||
| One thing that I found lacking in the [SimpleLogin API](https://github.com/simple-login/app/blob/master/docs/api.md) is that, it doesn't expose an API endpoint to create a contact based on the alias' email address. Rather, the `POST /api/aliases/:alias_id/contacts` endpoint requires the alias ID. So, I ended up downloading all aliases as multiple batches (each query returns upto 20 results) and saved them as json files in a folder. | ||
|
|
||
| With them in a folder, I could use jq to parse all of these json files for an alias email address, get its ID and further use it to create a new contact. All of this works like a charm now. My entire process works independent of the dashboard now: create a new alias, get its ID, create a contact, copy the reverse contact address, paste it on my email client. | ||
|
|
||
| The first part for getting the alias ID involves this command: | ||
|
|
||
| ```text | ||
| cat ~/Documents/SimpleLoginFiles/* | jq '.aliases[] | select(.email=="aliasAddress")' | jq '.id' | tr -d '\n' | pbcopy . | ||
| ``` | ||
|
|
||
| It was a pleasant surprise when I learned that I could pipe in all files in a folder to jq, instead of having to implement some sort of a loop logic. I don't know if it's bash's magic or something that jq handles elegantly. | ||
|
|
||
| The second part for creating the contact involves this command: | ||
|
|
||
| ```text | ||
| curl --location --request POST 'https://app.simplelogin.io/api/aliases/aliasID/contacts' --header 'Authentication: token' --header 'Content-Type: application/json' --data-raw '{"contact": "contactAddress"}' | jq '.reverse_alias' | tr -d "\\"" | pbcopy . | ||
| ``` | ||
|
|
||
| If you are wondering what the `tr -d "\\""` part is, it's to remove the unwanted escape characters that appears as a part of the SimpleLogin API output. I imagine it's possible to remove that using jq, but for now, the current workaround is sufficient. | ||
|
|
||
| The contact's reverse address is finally in my clipboard, which I can paste on Apple Mail: | ||
|
|
||
|  | ||
|
|
||
| Reverse alias on the "To" field of the composer | ||
|
|
||
| SimpleLogin recently announced an update to their Firefox extension too, to create reverse aliases (contact reverse address) on the go, but I like this API-based process better. The extension takes a while to populate all aliases. |