OWASP AppSec Pipeline
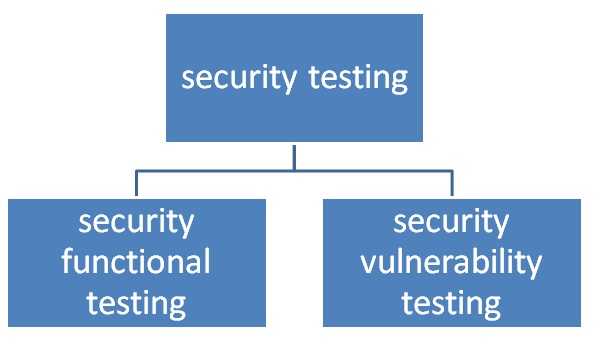
Security testing tools There is eight security tool categories: source code analyzers, web application (black-box) scanners, database scanners, binary analysis tools, runtime analysis tools, configuration management tools, HTTP proxies, miscellaneous tools.
http://slideplayer.com/slide/6869389/
https://www.checkmarx.com/wp-content/uploads/2016/02/Requirement.png
https://www.owasp.org/images/5/58/OWASP_ASVS_Version_2.pdf https://www.checkmarx.com/2016/02/05/5-best-practices-perfect-secure-code-review/ http://slideplayer.com/slide/6869389/ https://www.slideshare.net/ajin25/g4h-webcast-automated
Very good one with action items https://www.sans.org/reading-room/whitepapers/application/framework-secure-application-design-development-842
Cyber Security vs. Information Security Cyber security and information security aren’t different at all, but are related to each other in much the same way that the wider field of “science” is related to the practice of chemistry.
Cyber security is a broad practice, demanding mastery of a number of unique skills in computational theory and practice from its most effective practitioners. Ensuring that servers, intranets, and channels built for data transfer remain protected and accessible to only those permitted, for example, falls under the realm of “information security”. While some cyber security professionals may specialize in this area, this is only one of the many dimensions of the field.
Information security can be simply defined as “the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability.” Any point of data storage and transfer is considered to be an “information system”, which means this practice can apply to a wide variety of different environments, including those outside cyberspace.
Network security is another division within cyber security, focusing on data leaving or entering a device through an established network of computers and servers. Experts in network security monitor countless interactions between networked computers and other machines to make sure their connections are protected.
Umbrella covering everything to do with information security. InfoSec specialists cover a wide range of topics and are skilled generalists. In a big company setup, they are your CISOs and managers. In a smaller company, they are your practitioners.
Related more to software design and programming. AppSec specialists are familiar with programming and tend to focus on secure application design.
Firewalls, IDS, VPNs; practitioners understand lots of application-specific protocols. Anything that flows through a router is in their world.
Host-based security, domain controllers / auth servers, mandatory access controls systems. ITSec is focused inside of the system.
Backdoors – Backdoor is a kind of cyber threat in which the attacker uses a back door to install a keylogging software, thereby allowing an illegal access to your system. This threat can turn out to be possibly severe as it allows for modification of the files, stealing information, installing undesired software or even taking control of the entire computer.
Spoofing – Spoofing is another type of cyber attack where an individual or a program represent another by creating fake data to gain illegal access to a system. Such threats are commonly found in emails where the sender’s address is spoofed.
Bots – Bots is a type of software application that runs mechanized tasks which are simple and constant in nature. Bots may or may not be malicious, but they are usually found to initiate a DoS attack or a click scam while using the internet.
Tampering – Tampering is a web-based attack where certain parameters in the URL are changed without the consumer’s knowledge; and when the customer keys in that URL, it looks and appears the same. Tampering is done by hackers and criminals to steal the identity and obtain illegal access to information.
- SANS Institute
- OWASP
- Threat Modelling – MS TMT 2016
- Static Code Analysis – PMD, CheckMarx, Coverity, Fortify, Findbugs, Checkstyle
- Vulnerability Scanner – Arachni, Nikto, Nessus
- Packet Sniffing & Replay – TCPDUMP, Nmap, Tshark, Wireshark
- Penetration Testing – Metasploit, OpenVas, ZAP, Kali Linux
- REST API – Postman, SOAPUI
- Web Application Security – Burpsuite, SQLMap, SQLInjectMe, XSSME, TamperData, commix, Nmap, Zenmap, Hydra, Fiddler, Watobo, SSLScan
- Encryption & Cipher Test – GnuGPG, Bitlocker, Openssl, AES Online, md5sum
- Penetration testing
- Network and port scanning
- Authentication and authorization exploits
- Cross-site scripting exploits
- Session hijacking
- DNS poisoning
- Threats
- Attacks
- Vulnerabilities
- Countermeasures
Spoofing user identity. Tampering with data. Repudiation. Information disclosure. Denial of service. Elevation of privilege.
- Dynamic testing of web applications against major types of attacks: XSS, SQL Injection, buffer overflows, manipulations of the address bar and source code revealing
- Intrusion (penetration) tests (access control, authentication, input validation, cryptography reliability, error handling)
- Testing of payment mechanisms in different web systems
- Vulnerability testing of system's third-party components
- Security code audit (use of static code analysis tools, manual review of major components of the system, recommendations on improvements, patches, security alerts)
- Server configuration testing (search for errors in multithreaded environments that allow data to be shared or corrupted)
10 Steps To Kickstart Your Web Application Security Career https://dzone.com/articles/10-steps-to-kickstart-your-web-application-securit
Detect & fix security vulnerabilities, problematic open source licenses. https://marketplace.visualstudio.com/items?itemName=whitesource.ws-bolt
What Is Server-Side Request Forgery (SSRF)? https://dzone.com/articles/what-is-server-side-request-forgery-ssrf?
http://shapingsoftware.com/2009/03/09/security-hot-spots/
http://testingrants.blogspot.in/2017/03/some-security-podcasts-i-like.html
OWASP https://drive.google.com/file/d/0BxOPagp1jPHWYmg3Y3BfLVhMcmc/view 
- Read about OWASP Mutillidae II Web Pen-Test Training Environment
http://image.slidesharecdn.com/rss2010-s14-ucedavelezapplication-threat-modeling-101024185548-phpapp01/95/application-threat-modeling-38-638.jpg https://media.licdn.com/mpr/mpr/p/5/005/051/39d/319d58e.jpg http://2we26u4fam7n16rz3a44uhbe1bq2.wpengine.netdna-cdn.com/wp-content/uploads/2-9.png https://media.licdn.com/mpr/mpr/p/5/005/051/39e/1cfaaa9.jpg https://media.licdn.com/mpr/mpr/p/5/005/051/39e/3747637.jpg http://www.taosecurity.com/images/vulnerability-threat_pairs.png http://player.slideplayer.com/22/6405319/data/images/img16.png http://image.slidesharecdn.com/owaspocsept17presentationvs10reduced-091030221445-phpapp01/95/security-compliance-web-application-risk-management-34-728.jpg?cb=1258273619 http://2.bp.blogspot.com/-ZbvSKb6_n00/Upmte-znE9I/AAAAAAAAABc/kiZnBw4Oizw/s400/security.png
http://www.guidanceshare.com/images/7/7e/DatabaseServerThreatsAndVulnerabilities.gif
http://www.guidanceshare.com/images/d/d4/InternetWebtoDatabaseThreats.gif
http://www.guidanceshare.com/images/b/bd/InternetWebToDatabaseVulnerabilities.gif
http://www.guidanceshare.com/images/7/7e/DatabaseServerThreatsAndVulnerabilities.gif
http://www.guidanceshare.com/images/f/fe/LibraryThreatsAndVulnerabilities.gif
http://www.guidanceshare.com/images/7/75/WebAppThreatsAndVulnerabilities.gif
http://www.guidanceshare.com/images/2/28/WebServerThreatsAndVulnerabilities.gif
Thanks to J.D. Meier-He is Awesome
http://www.praxiom.com/iso-27001-sample.pdf
https://github.com/OWASP-Foundation/Project-Handbook
https://assets.publishing.service.gov.uk/government/uploads/system/uploads/image_data/file/35290/common_cyber_attacks.png